Welcome to Traefik Enterprise!¶
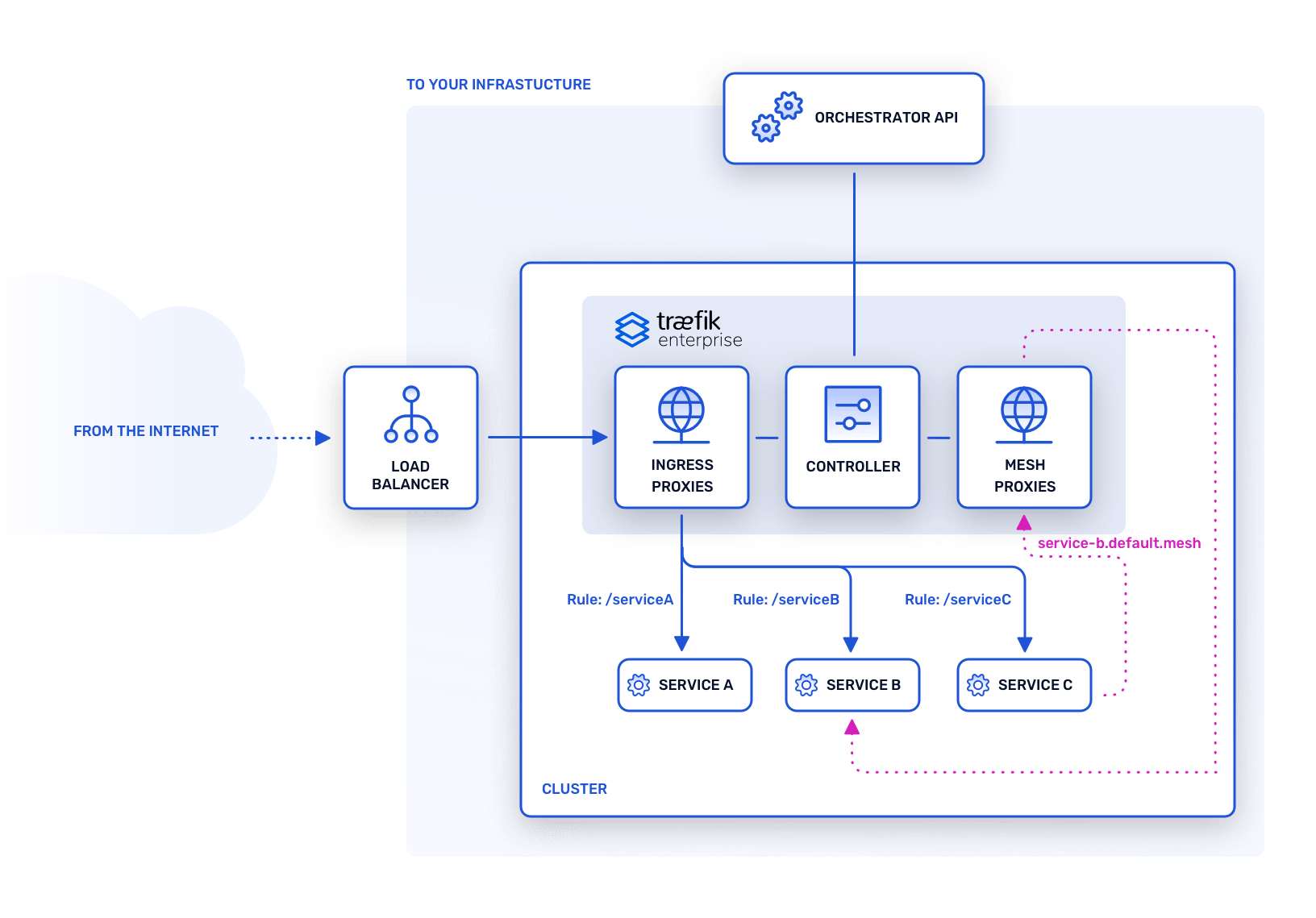
Traefik Enterprise runs on the edge of your platform to route traffic to your applications.
By splitting responsibilities between two planes, Traefik Enterprise follows the principle of "separation of concerns." To ensure that sensitive information only runs on a closed and safe environment, the control plane is not exposed to the outside. As a result, any malicious action from external traffic stays within the data plane and your platform stays safe. Moreover, Traefik Enterprise only relies on encrypted communications between nodes, to add an extra layer of security.
This distributed architecture is the cornerstone of Traefik Enterprise’s strengths: natively highly available, scalable, and secure.
New. Traefik Enterprise 2.2 introduces optional service mesh capabilities that support the latest Service Mesh Interface (SMI) specification, offering integrated management of inter-process communications between services.
Learn more about Traefik Enterprise features in the Features section.
Smooth Operations¶
Traefik Enterprise is based on the Raft consensus algorithm. Installing and managing a Raft-based application is usually a painful experience. Because Traefik Proxy's popularity is due to its usability and refreshing user experience, however, we have extended those benefits to Traefik Enterprise for you.
Traefik Enterprise comes with an additional command-line tool called teectl (pronounced "teakettle") that can deploy and operate a cluster with several nodes in only one command line. We hope you will love using this time-saving tool.
Dashboard¶
Traefik Enterprise's dashboard shows all the relevant information about your cluster at a glance, including enabled features, providers, entry points, and routers. In addition, it enables easy inspection and error reporting for the optional service mesh.
Distributed Features¶
Traefik Enterprise improves Traefik Proxy features by making them distributed throughout your cluster.
Distributed Rate Limiting¶
Centralize the rate limiting process of all of your proxies, for services with standard rate limiting configuration, just like in Traefik Proxy.
Distributed In-Flight Request Limiting¶
Centralize the in-flight request limiting process of all of your proxies, for services with standard in-flight request limiting configuration, just like in Traefik Proxy v2.
Service Mesh¶
Enabling Traefik Enterprise's service mesh capabilities provides a straightforward, easy-to-use way to manage inter-process communication between microservices on a cluster. Features include access control, traffic splitting, and support for the circuit breaker pattern.
Support¶
Traefik Enterprise licenses come with built-in support: contact our team of engineers at support.traefik.io.
What's Next?
If you want to learn more about Traefik Enterprise concepts, please visit the Concepts section.
If you are interested in getting started with Traefik Enterprise right away, please have a look at the "Getting Started" page.
You might also want to check the other sections on Installing, Operating, and Integrating Traefik Enterprise, or contact support.