Traefik Provider¶
The Traefik provider allows Traefik Enterprise to route requests to other Traefik Enterprise instances.
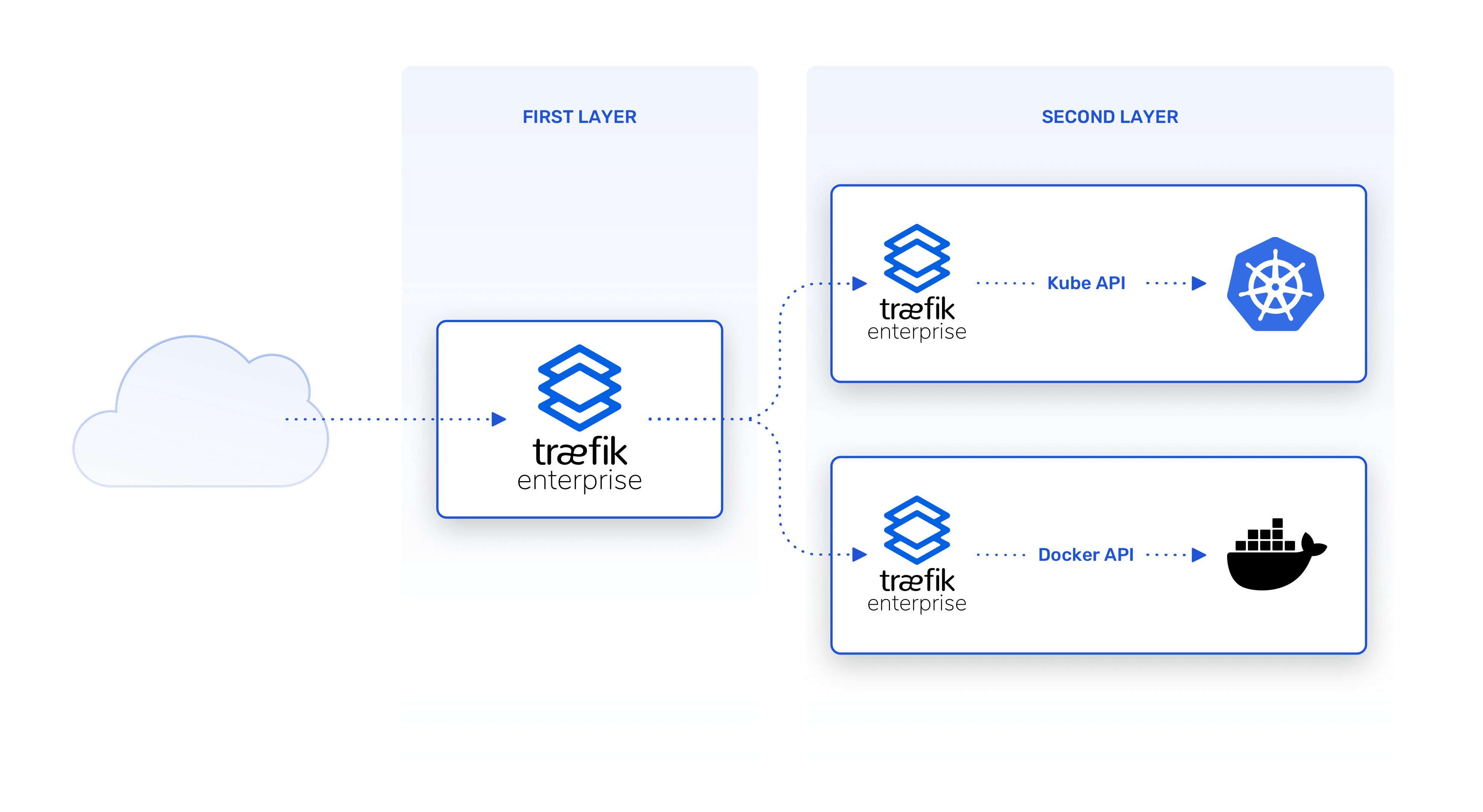
Layer 2 Traefik Enterprise Configuration¶
The Traefik provider relies on the API exposed by the layer 2 Traefik Enterprise instances. This section will show you how to expose this API.
Secure you API routes
We strongly recommend you secure your API routes. The Traefik provider allows you to set an authorization header with the credentials required by layer 2. In this example, we demonstrate how to do this with the API Key middleware, but any authentication middleware can work.
First, update the static configuration to enable the API:
# Static Configuration
entryPoints:
http:
address: ":80"
https:
address: ":443"
api:
address: ":8080"
api: {}# Static Configuration
[entryPoints]
[entryPoints.http]
address = ":80"
[entryPoints.https]
address = ":443"
[entryPoints.api]
address = ":8080"
[api]Then, create a route that uses API Key middleware to securely expose it:
http:
routers:
api-tls:
entryPoints:
- "api"
middlewares:
- "api-key-auth"
service: api@internal
rule: "Host(`<CLUSTER1_HOST>`)"
tls: {}
middlewares:
api-key-auth:
plugin:
apiKey:
secretParam: Authorization
secretValue: $2y$05$aWnGD0X128wkQL4Pj7osie1KhyDz5j/JLnP02pLcS0GPcrXL22GCa # "secret-api-key"
kind: header# Dynamic Configuration
[http.routers.api-tls]
entryPoints = ['api']
rule = "Host(`<CLUSTER1_HOST>`)"
service = "api@internal"
# Secured route with API Key middleware
middleware = ["api-key-auth"]
[http.routers.api-tls.tls]
[http.middlewares]
[http.middlewares.api-key-auth.plugin.apiKeyAuth]
secretParam = Authorization
secretValue = $2y$05$aWnGD0X128wkQL4Pj7osie1KhyDz5j/JLnP02pLcS0GPcrXL22GCa # "secret-api-key"
kind = headerYour layer 2 Enterprise cluster is now ready to accept requests from the layer 1 cluster. Let's enable the Traefik provider in the next section.
Layer 1 Traefik Enterprise Configuration¶
This section describes how to enable the Traefik provider on layer 1 Traefik Enterprise cluster.
Use the same entryPoints
You must use the same entry point names on both layer 1 and layer 2 clusters for requests to be routed correctly.
Note that the API does not need to be exposed on the layer 1 Traefik Enterprise cluster.
# Static Configuration
entryPoints:
http:
address: ":80"
https:
address: ":443"
providers:
plugin:
traefik:
cluster1:
apiAddr: "https://<CLUSTER1_HOST>:8080"
authorizationHeader: "secret-api-key"# Static Configuration
[entryPoints]
[entryPoints.http]
address = ":80"
[entryPoints.https]
address = ":443"
[providers.plugin.traefik]
[providers.plugin.traefik.cluster1]
apiAddr = "https://<CLUSTER1_HOST>:8080"
authorizationHeader = "secret-api-key"When enabled, a new router will be created at the layer 1 cluster for each entrypoint associated to the original layer 2 routers. This is done to ensure correct routing between entrypoints, which might include different ports, transport configuration or middleware.
It's also important to note that at layer 1 any middleware configuration is ignored as this layer acts as a simple hop to the next one where the actual middleware execution happens.
Provider Configuration Reference¶
The Traefik provider can be enabled and configured from the static configuration:
providers:
plugin:
traefik:
cluster1:
apiAddr: "https://cluster1:8080"
cluster2:
apiAddr: "https://cluster2:8080"[providers.plugin.traefik]
[providers.plugin.traefik.cluster1]
apiAddr = "https://cluster1:8080"
[providers.plugin.traefik.cluster2]
apiAddr = "https://cluster2:8080"apiAddr¶
Required, Default=""
Defines the API address of the layer 2 Traefik Enterprise cluster to target.
providers:
plugin:
traefik:
cluster1:
apiAddr: "https://cluster1:8080"[providers.plugin.traefik]
[providers.plugin.traefik.cluster1]
apiAddr = "https://cluster1:8080"authorizationHeader¶
Optional, Default=""
Defines an authorization header to add to the requests sent to fetch the configuration from the layer 2 Traefik Enterprise cluster.
providers:
plugin:
traefik:
cluster1:
authorizationHeader: "secret-api-key"[providers.plugin.traefik]
[providers.plugin.traefik.cluster1]
authorizationHeader = "secret-api-key"