HTTP Middlewares¶
Controlling connections
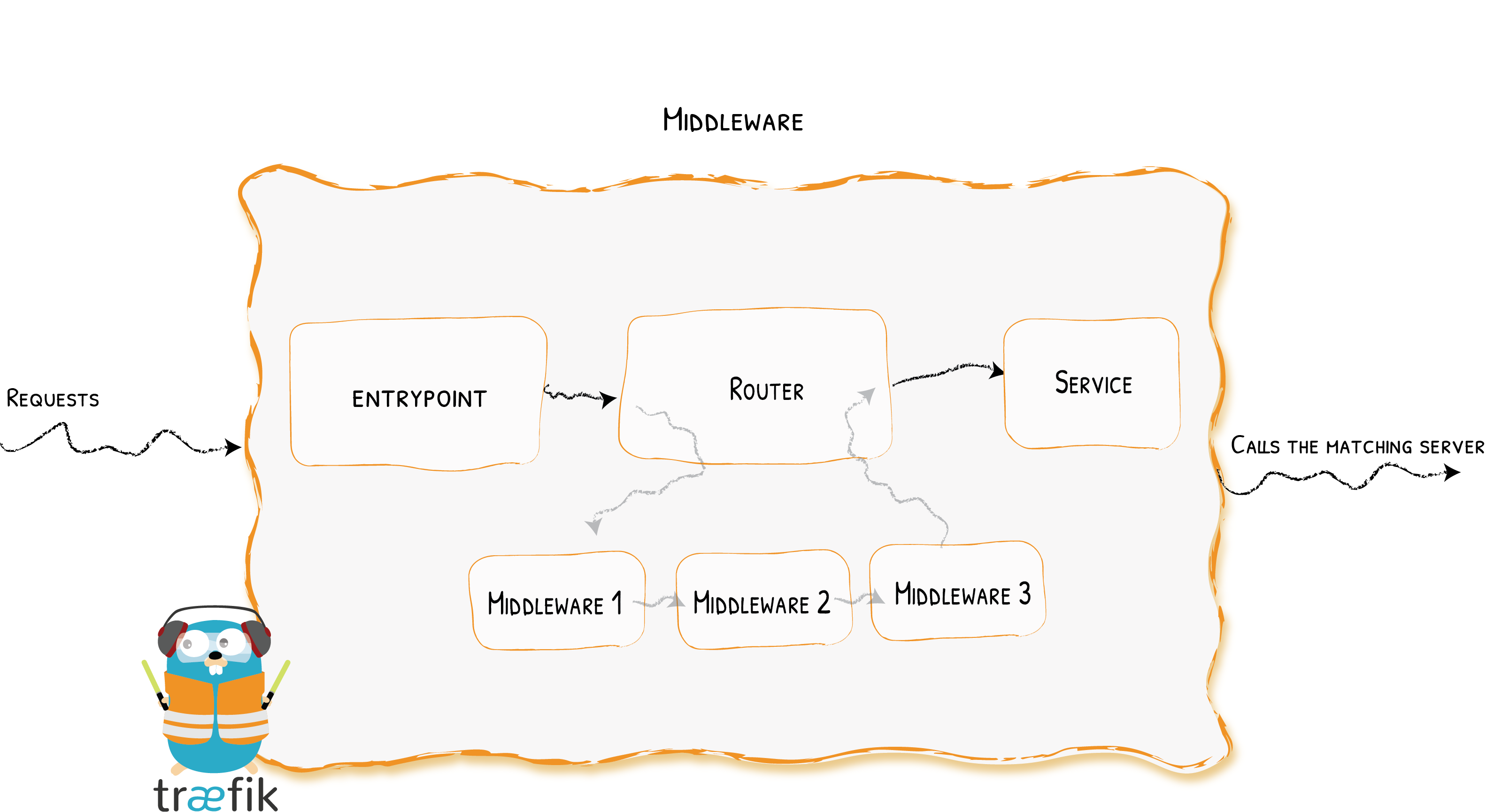
Configuration Example¶
# As a Docker Label
whoami:
# A container that exposes an API to show its IP address
image: traefik/whoami
labels:
# Create a middleware named `foo-add-prefix`
- "traefik.http.middlewares.foo-add-prefix.addprefix.prefix=/foo"
# Apply the middleware named `foo-add-prefix` to the router named `router1`
- "traefik.http.routers.router1.middlewares=foo-add-prefix@docker"# As a Kubernetes Traefik IngressRoute
---
apiVersion: traefik.io/v1alpha1
kind: Middleware
metadata:
name: stripprefix
spec:
stripPrefix:
prefixes:
- /stripit
---
apiVersion: traefik.io/v1alpha1
kind: IngressRoute
metadata:
name: ingressroute
spec:
# more fields...
routes:
# more fields...
middlewares:
- name: stripprefix# Create a middleware named `foo-add-prefix`
- "traefik.http.middlewares.foo-add-prefix.addprefix.prefix=/foo"
# Apply the middleware named `foo-add-prefix` to the router named `router1`
- "traefik.http.routers.router1.middlewares=foo-add-prefix@consulcatalog"# As TOML Configuration File
[http.routers]
[http.routers.router1]
service = "service1"
middlewares = ["foo-add-prefix"]
rule = "Host(`example.com`)"
[http.middlewares]
[http.middlewares.foo-add-prefix.addPrefix]
prefix = "/foo"
[http.services]
[http.services.service1]
[http.services.service1.loadBalancer]
[[http.services.service1.loadBalancer.servers]]
url = "http://127.0.0.1:80"# As YAML Configuration File
http:
routers:
router1:
service: service1
middlewares:
- "foo-add-prefix"
rule: "Host(`example.com`)"
middlewares:
foo-add-prefix:
addPrefix:
prefix: "/foo"
services:
service1:
loadBalancer:
servers:
- url: "http://127.0.0.1:80"Available HTTP Middlewares¶
| Middleware | Purpose | Area |
|---|---|---|
| AddPrefix | Adds a Path Prefix | Path Modifier |
| BasicAuth | Adds Basic Authentication | Security, Authentication |
| Buffering | Buffers the request/response | Request Lifecycle |
| Chain | Combines multiple pieces of middleware | Misc |
| CircuitBreaker | Prevents calling unhealthy services | Request Lifecycle |
| Compress | Compresses the response | Content Modifier |
| ContentType | Handles Content-Type auto-detection | Misc |
| DigestAuth | Adds Digest Authentication | Security, Authentication |
| Errors | Defines custom error pages | Request Lifecycle |
| ForwardAuth | Delegates Authentication | Security, Authentication |
| Headers | Adds / Updates headers | Security |
| IPAllowList | Limits the allowed client IPs | Security, Request lifecycle |
| InFlightReq | Limits the number of simultaneous connections | Security, Request lifecycle |
| PassTLSClientCert | Adds Client Certificates in a Header | Security |
| RateLimit | Limits the call frequency | Security, Request lifecycle |
| RedirectScheme | Redirects based on scheme | Request lifecycle |
| RedirectRegex | Redirects based on regex | Request lifecycle |
| ReplacePath | Changes the path of the request | Path Modifier |
| ReplacePathRegex | Changes the path of the request | Path Modifier |
| Retry | Automatically retries in case of error | Request lifecycle |
| StripPrefix | Changes the path of the request | Path Modifier |
| StripPrefixRegex | Changes the path of the request | Path Modifier |
Community Middlewares¶
Please take a look at the community-contributed plugins in the plugin catalog.
Using Traefik OSS in Production?
If you are using Traefik at work, consider adding enterprise-grade API gateway capabilities or commercial support for Traefik OSS.
Adding API Gateway capabilities to Traefik OSS is fast and seamless. There's no rip and replace and all configurations remain intact. See it in action via this short video.