API Key Authentication
How to configure API keys.
Introduction
API Key authentication is a method that utilizes unique keys to authenticate and authorize access to APIs. API consumers can generate API keys in the Traefik Hub Portal or use JWT (JSON Web Token) to authorize.
API keys are managed via the API Portal and stored in Traefik Hub.
Enable API Key Authentication in Traefik Hub
API Key authentication is the default enabled authentication method.
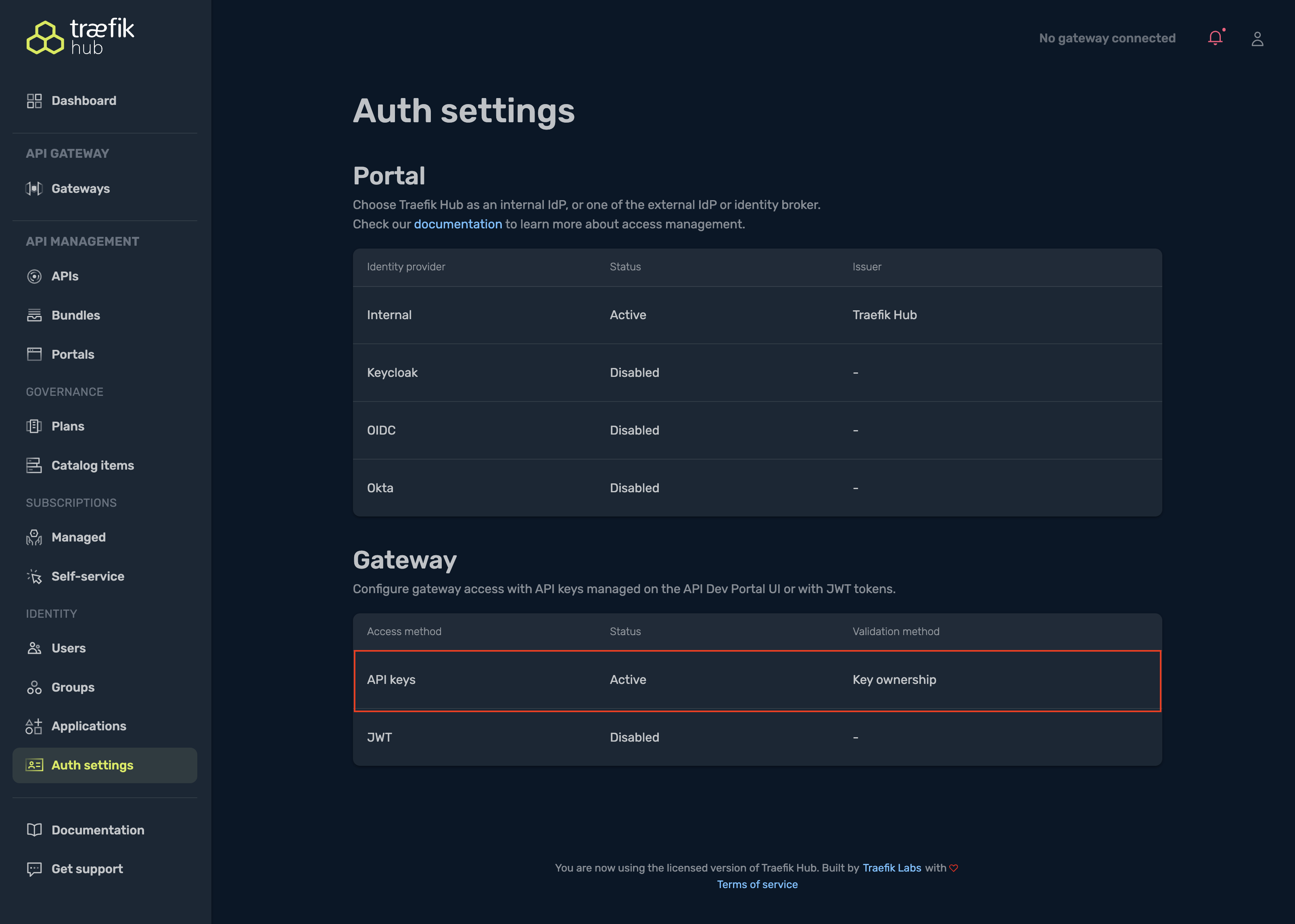
Set Up Keys
In Traefik Hub, you configure API keys for authentication through API Portals.
The tokens are tied to the user. If you add a key on one Portal, it will appear on other Portals, even on other agents.
Please follow the detailed documentation about how to create API Keys in the Portal.
Key Authentication Example
The following example uses curl to send test requests to an API using API Keys as the authentication method.
Please replace api.example.com and XXXX with your settings!
curl -v --location https://api.example.com/customers/customers -H 'accept: application/json' -H 'Authorization: Bearer XXXX'
Which will show:
curl -v --location https://api.example.com/customers/customers -H 'accept: application/json' -H 'Authorization: Bearer XXXX'
* Trying XX.XX.XX.XX:443...
* Connected to api.example.com (XX.XX.XX.XX) port 443 (#0)
* ALPN: offers h2
* ALPN: offers http/1.1
* CAfile: /etc/ssl/cert.pem
* CApath: none
* [CONN-0-0][CF-SSL] (304) (OUT), TLS handshake, Client hello (1):
* [CONN-0-0][CF-SSL] (304) (IN), TLS handshake, Server hello (2):
* [CONN-0-0][CF-SSL] (304) (IN), TLS handshake, Unknown (8):
* [CONN-0-0][CF-SSL] (304) (IN), TLS handshake, Certificate (11):
* [CONN-0-0][CF-SSL] (304) (IN), TLS handshake, CERT verify (15):
* [CONN-0-0][CF-SSL] (304) (IN), TLS handshake, Finished (20):
* [CONN-0-0][CF-SSL] (304) (OUT), TLS handshake, Finished (20):
* SSL connection using TLSv1.3 / AEAD-CHACHA20-POLY1305-SHA256
* ALPN: server accepted h2
* Server certificate:
* subject: CN=*.api.example.com
* start date: Feb 28 11:52:59 2023 GMT
* expire date: May 29 11:52:58 2023 GMT
* subjectAltName: host "api.example.com" matched cert's "*.api.example.com"
* issuer: C=US; O=Let's Encrypt; CN=R3
* SSL certificate verify ok.
* Using HTTP2, server supports multiplexing
* Copying HTTP/2 data in stream buffer to connection buffer after upgrade: len=0
* h2h3 [:method: GET]
* h2h3 [:path: /customers/customers]
* h2h3 [:scheme: https]
* h2h3 [:authority: api.example.com]
* h2h3 [user-agent: curl/7.87.0]
* h2h3 [accept: */*]
* Using Stream ID: 1 (easy handle 0x12b010a00)
> GET /customers/customers HTTP/2
> Host: api.example.com
> user-agent: curl/7.87.0
> accept: */*
>
* Connection state changed (MAX_CONCURRENT_STREAMS == 250)!
< HTTP/2 200
< access-control-allow-credentials: true
< cache-control: no-cache
< content-type: application/json; charset=utf-8
< date: Fri, 31 Mar 2023 13:04:11 GMT
< etag: W/"152-YYUUBmMg0FfHP0BwM9kbIO/ll84"
< expires: -1
< pragma: no-cache
< vary: Origin, Accept-Encoding
< x-content-type-options: nosniff
< x-powered-by: Express
< content-length: 338
<
[
{
"id": 1,
"firstName": "John",
"lastName": "Doe",
"points": 100,
"status": "bronze"
},
{
"id": 2,
"firstName": "Jane",
"lastName": "Doe",
"points": 200,
"status": "silver"
},
{
"id": 3,
"firstName": "John",
"lastName": "Smith",
"points": 300,
"status": "gold"
}
* Connection #0 to host api.example.com left intact
]%
