Configuring OIDC SSO and Gateway Authentication with Oracle IAM Identity Domains
This guide explains how to integrate OpenID Connect (OIDC) Single Sign-On (SSO) for the Traefik Hub API Portal and Gateway authentication with Oracle IAM Identity Domains (OCI). It covers both user authentication for portals (SSO) and secure gateway access using JWT tokens.
Prerequisites
- Oracle Cloud Infrastructure (OCI) account
- Traefik Hub installed and running in your OCI Kubernetes Engine (OKE) cluster. If you haven't set this up yet, follow one of these guides:
- Oracle IAM Identity Domain configured and ready to use. If you haven't set this up yet, follow this guide:
Configure OIDC SSO for the Traefik Hub API Portal withOracle IAM Identity Domains
Register the Application in Oracle IAM
Log in to the Oracle Cloud Console and navigate to Identity & Security > Domains.
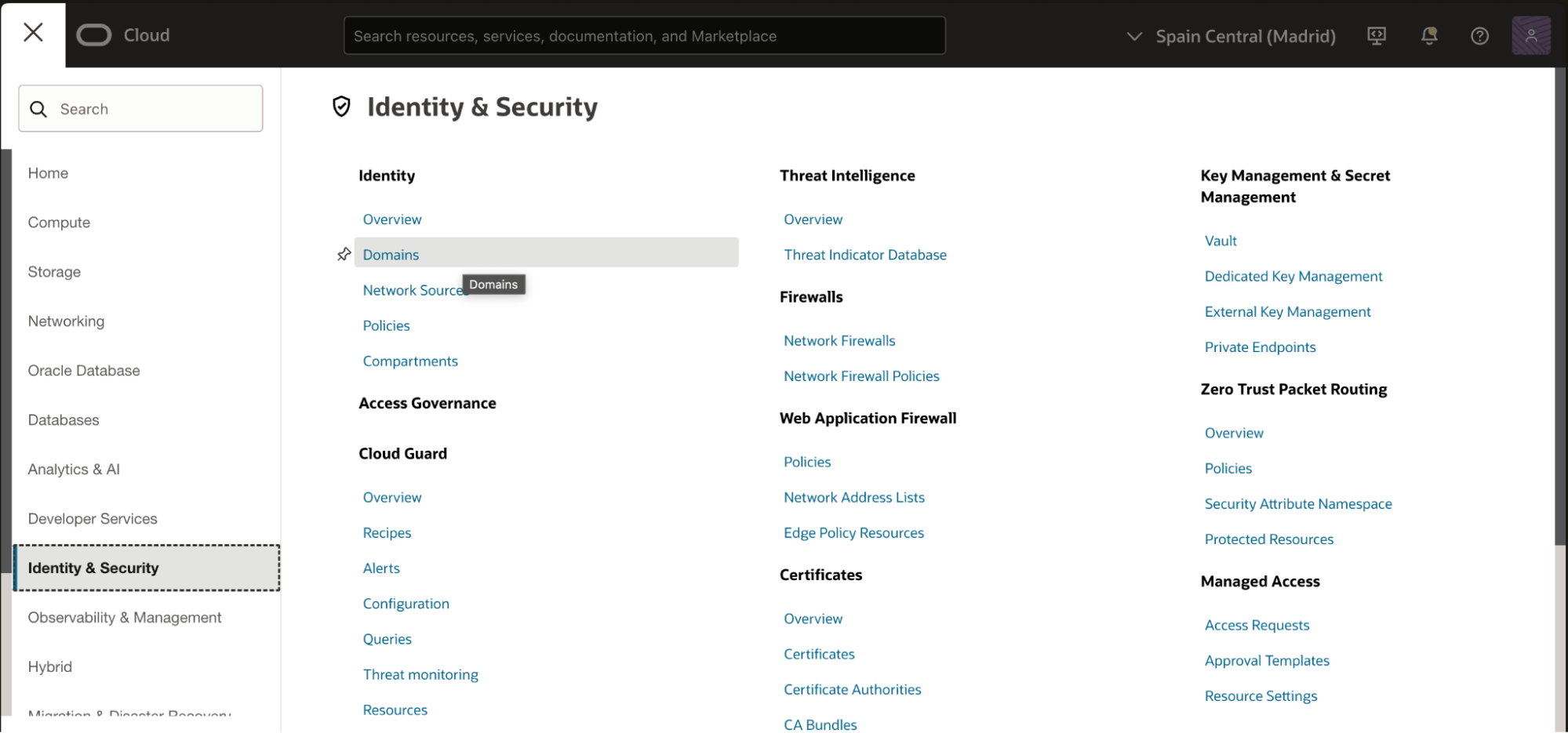
Select your Identity Domain and it should open the domain details page.
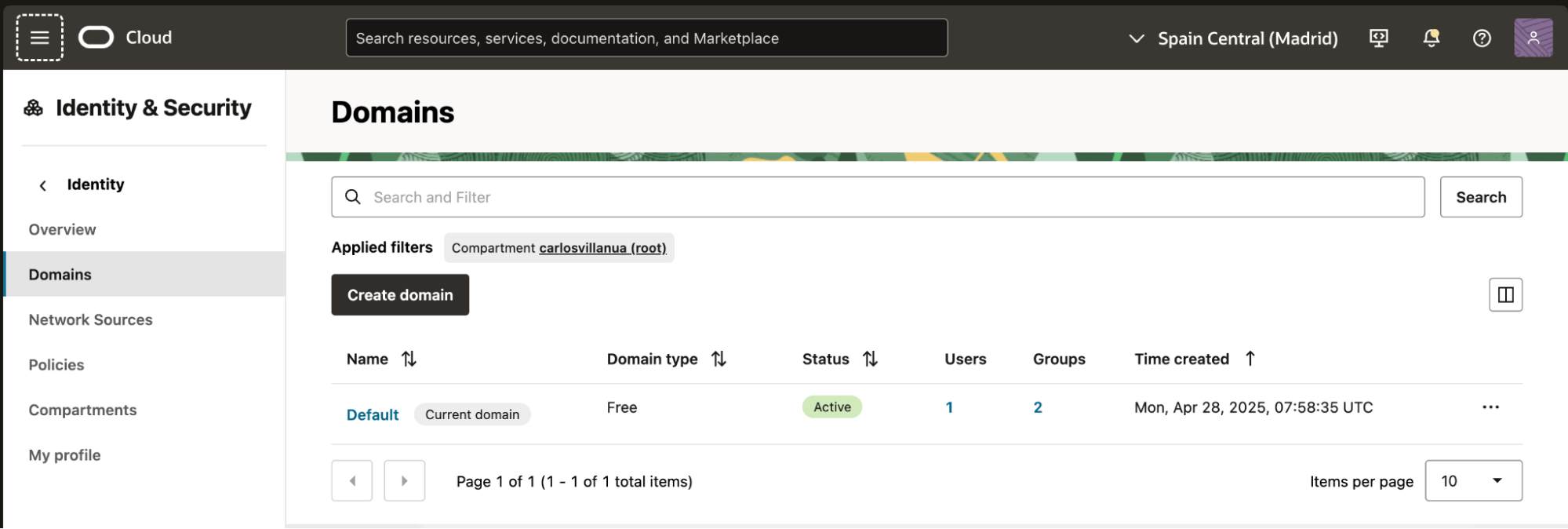
Next, Go to the Settings tab and select Edit domain settings
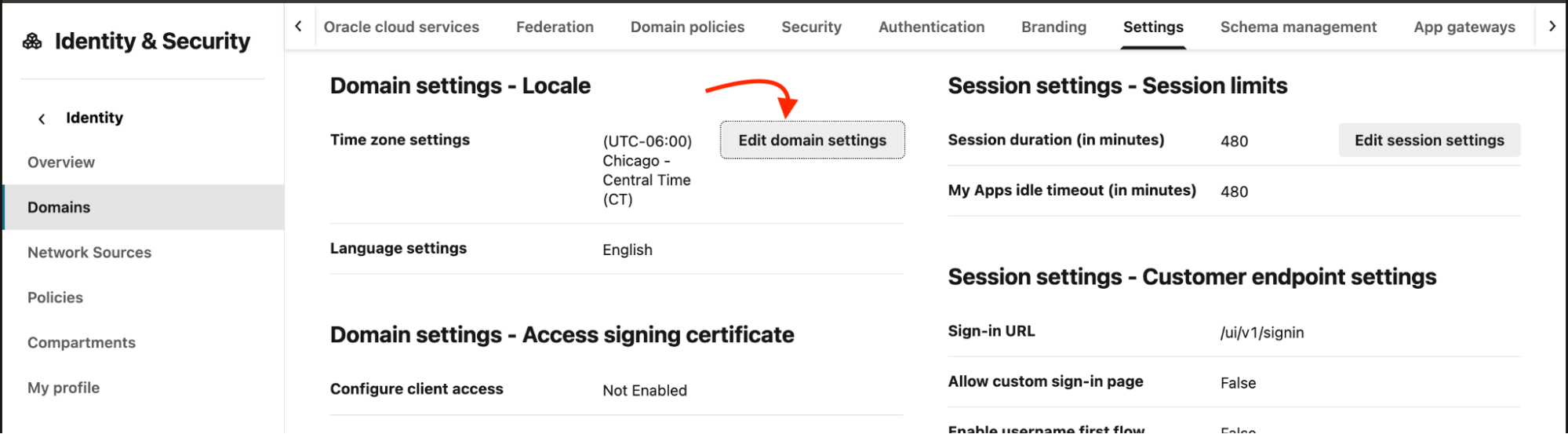
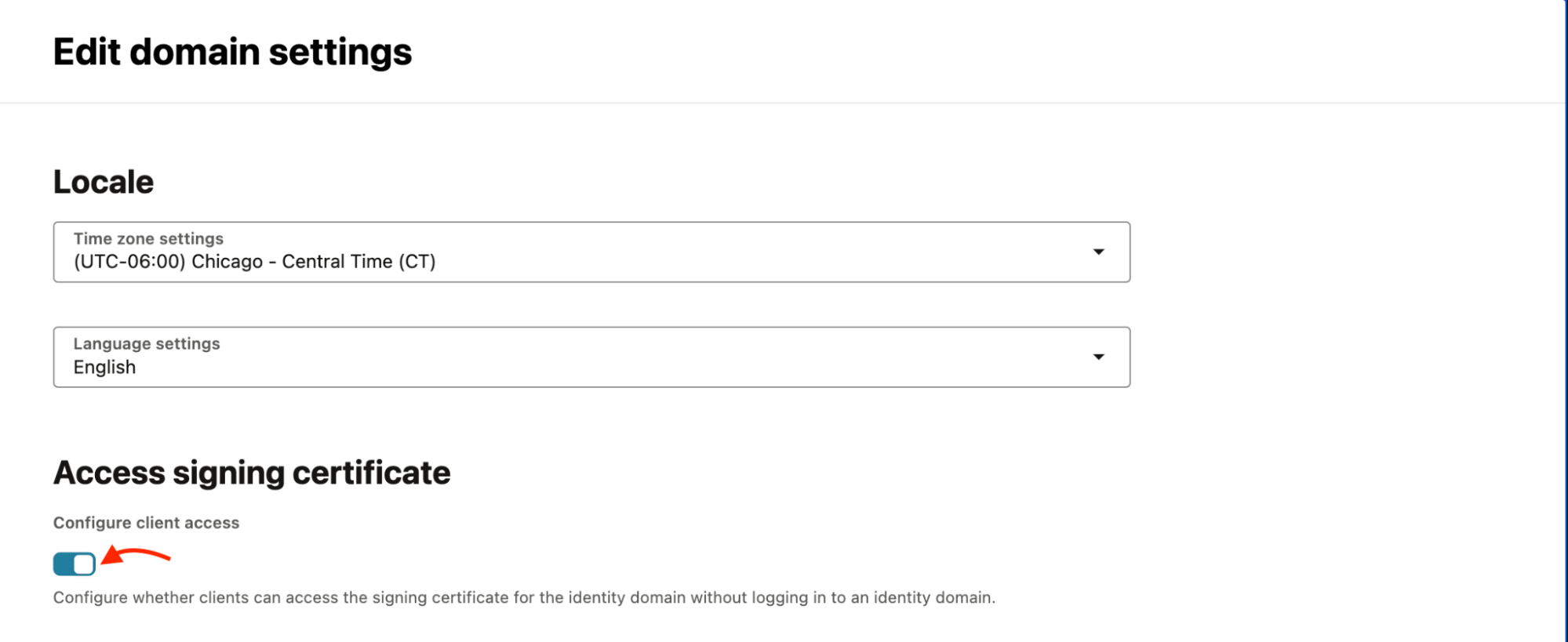
In the domain settings, enable Configure client access and save changes.
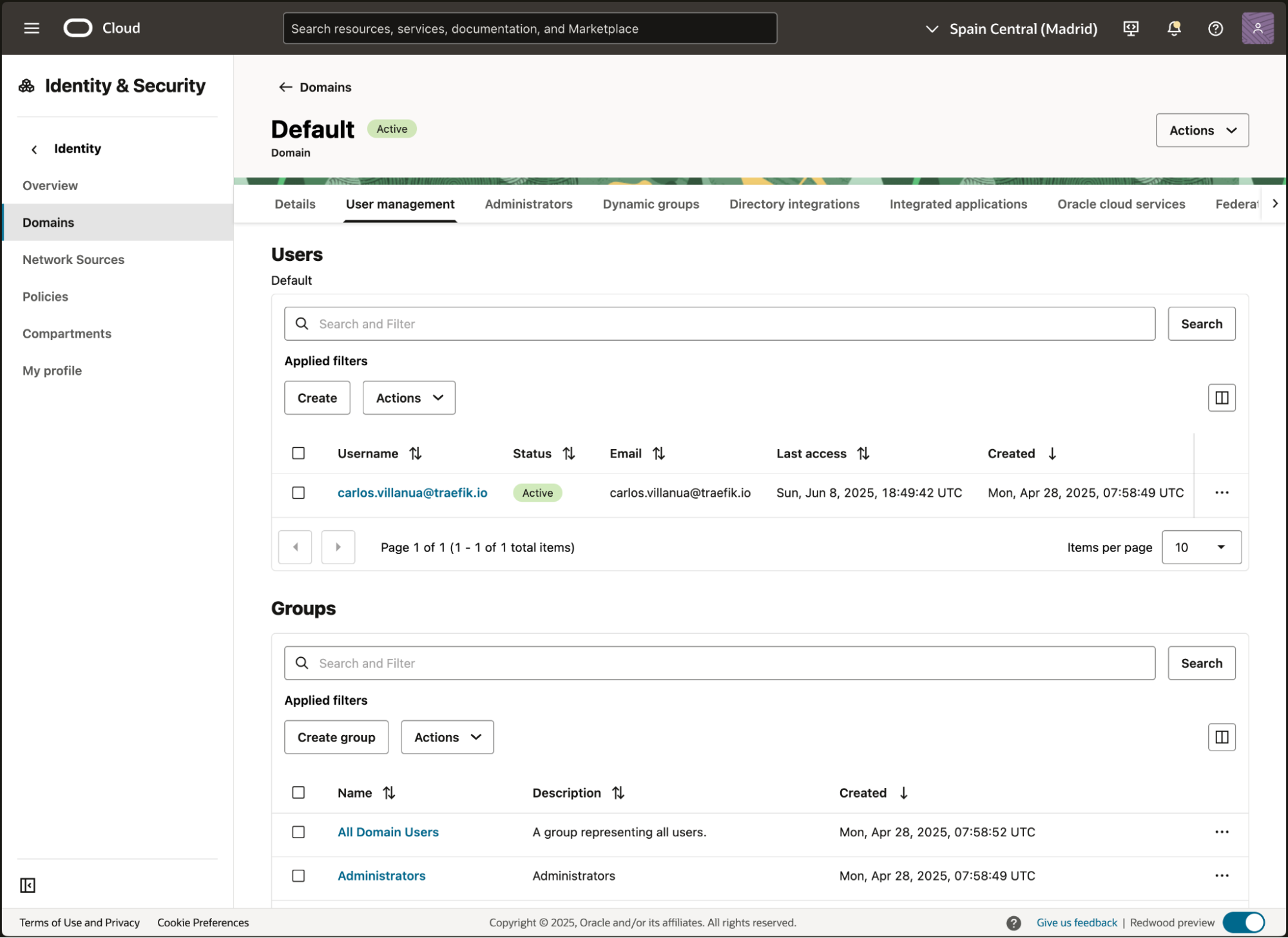
Create Users and Groups
In the domains menu, Navigate to the User Management tab, create users and groups that correspond to those in your Traefik Portal.
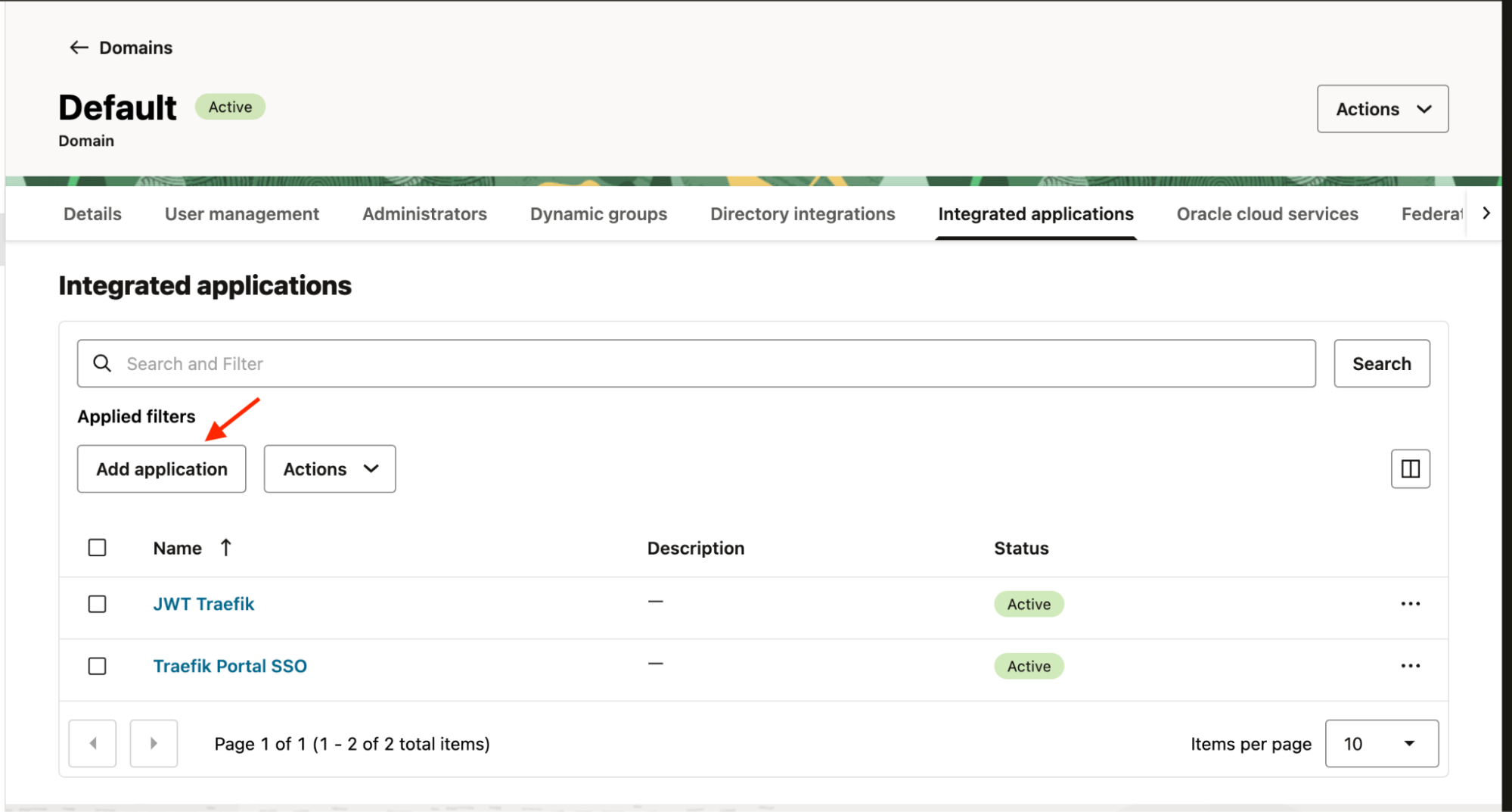
Add an Application
In the domains menu, navigate to the Integrated Applications tab and select Add Application.
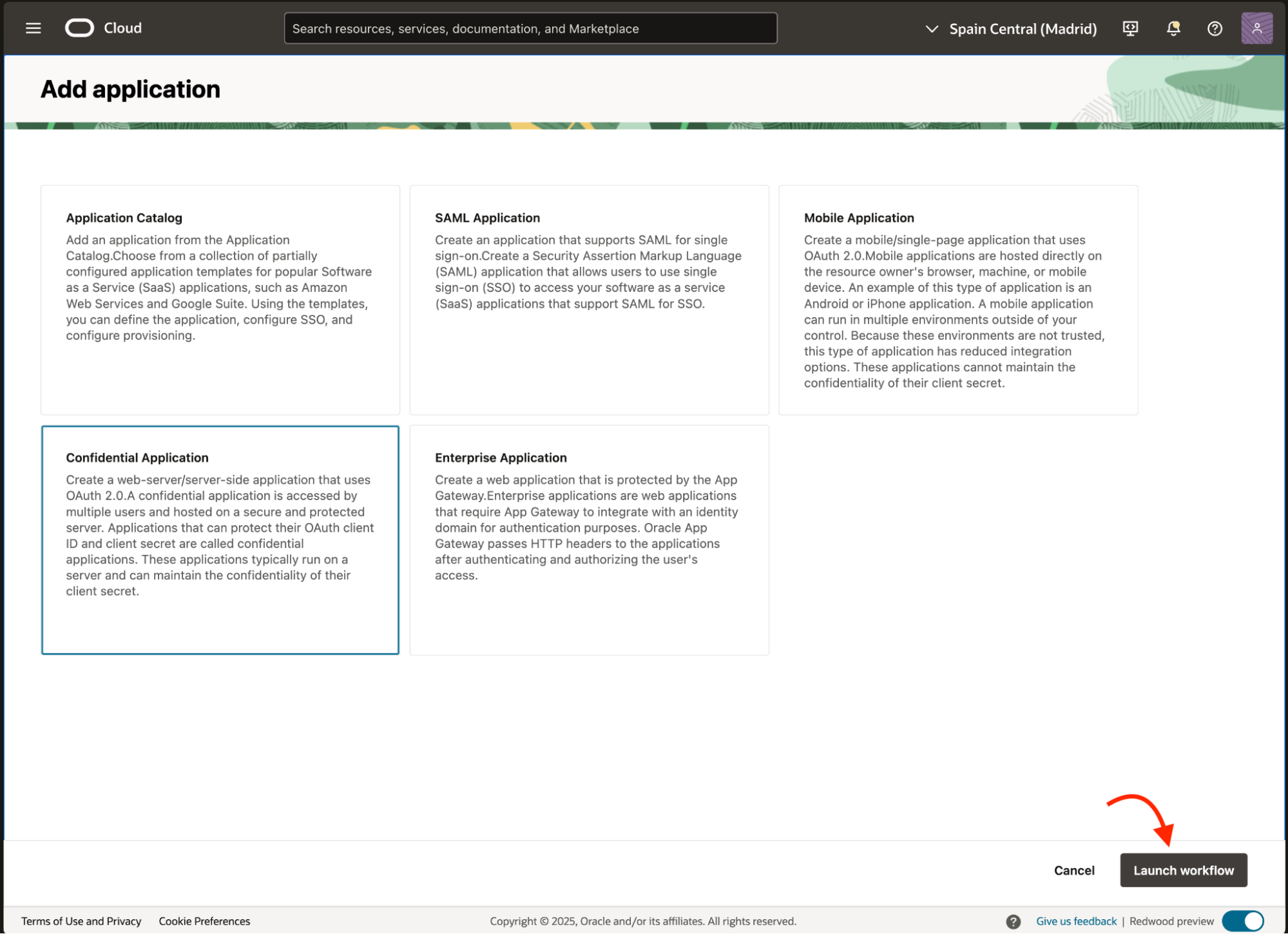
Next, Select Confidential Application and Launch workflow.
In the displayed form, enter the application details (only the Name field is required).
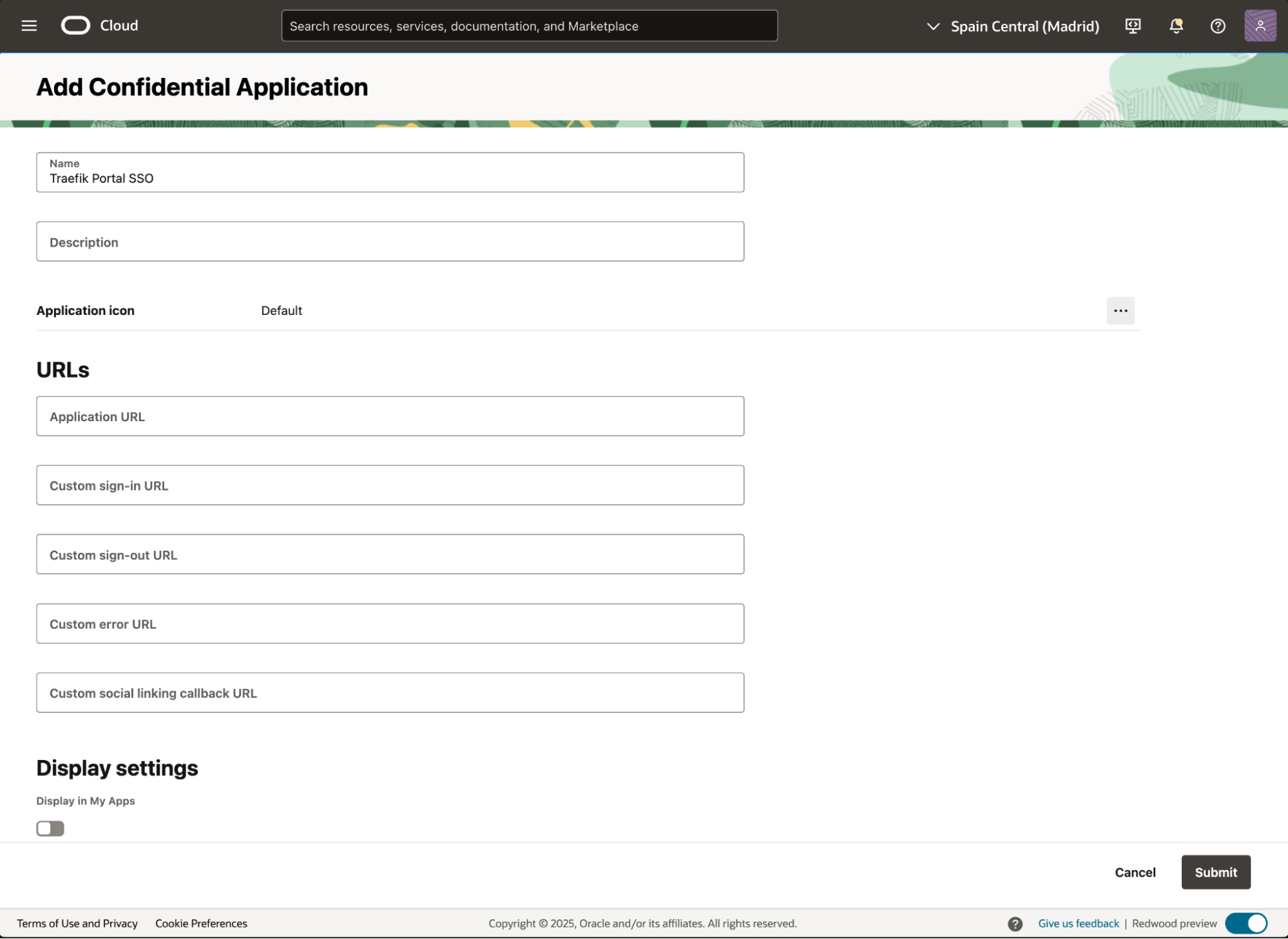
Next, select Next to proceed to OAuth configuration.
Configure OAuth
After creating the application, you will be redirected to the application details page to configure OAuth and Web tier policy.
Next, navigate to the OAuth configuration tab, select Edit OAuth configuration.
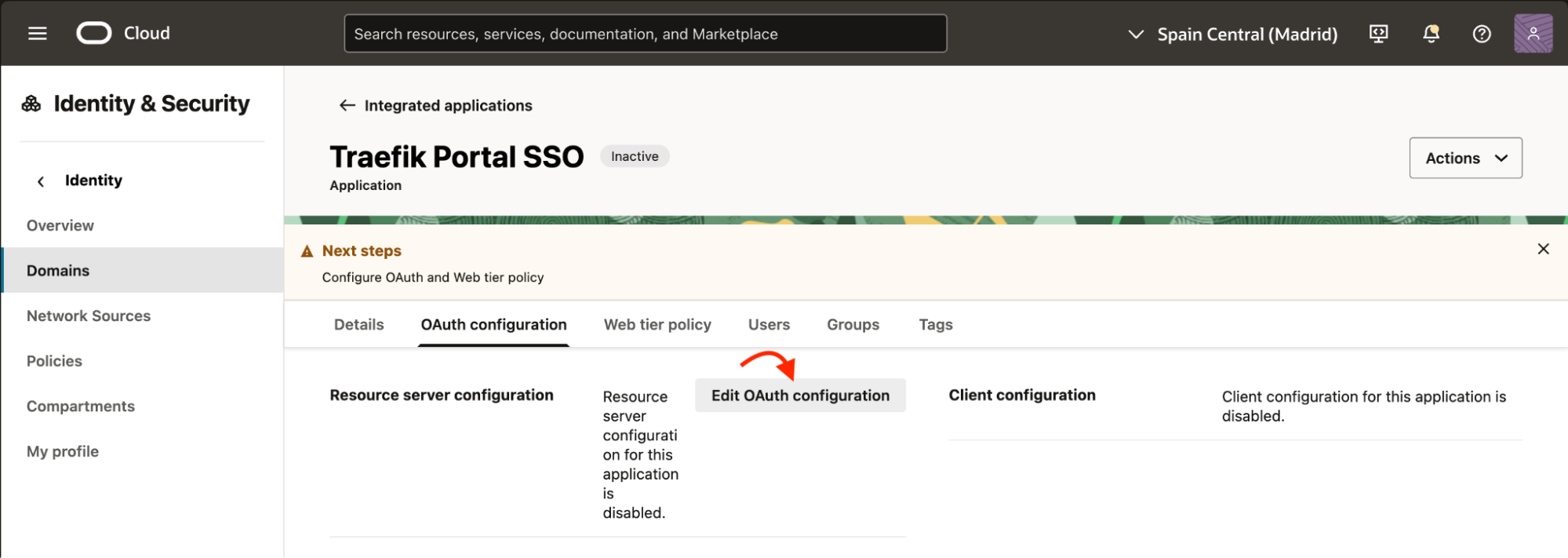
In the OAuth configuration menu, select the following options:
- Configure this application as a client now
- In the authorization allowed grant types list, select Authorization code
- In the redirect URIs field, enter the following:
https://<portal URL>/callback
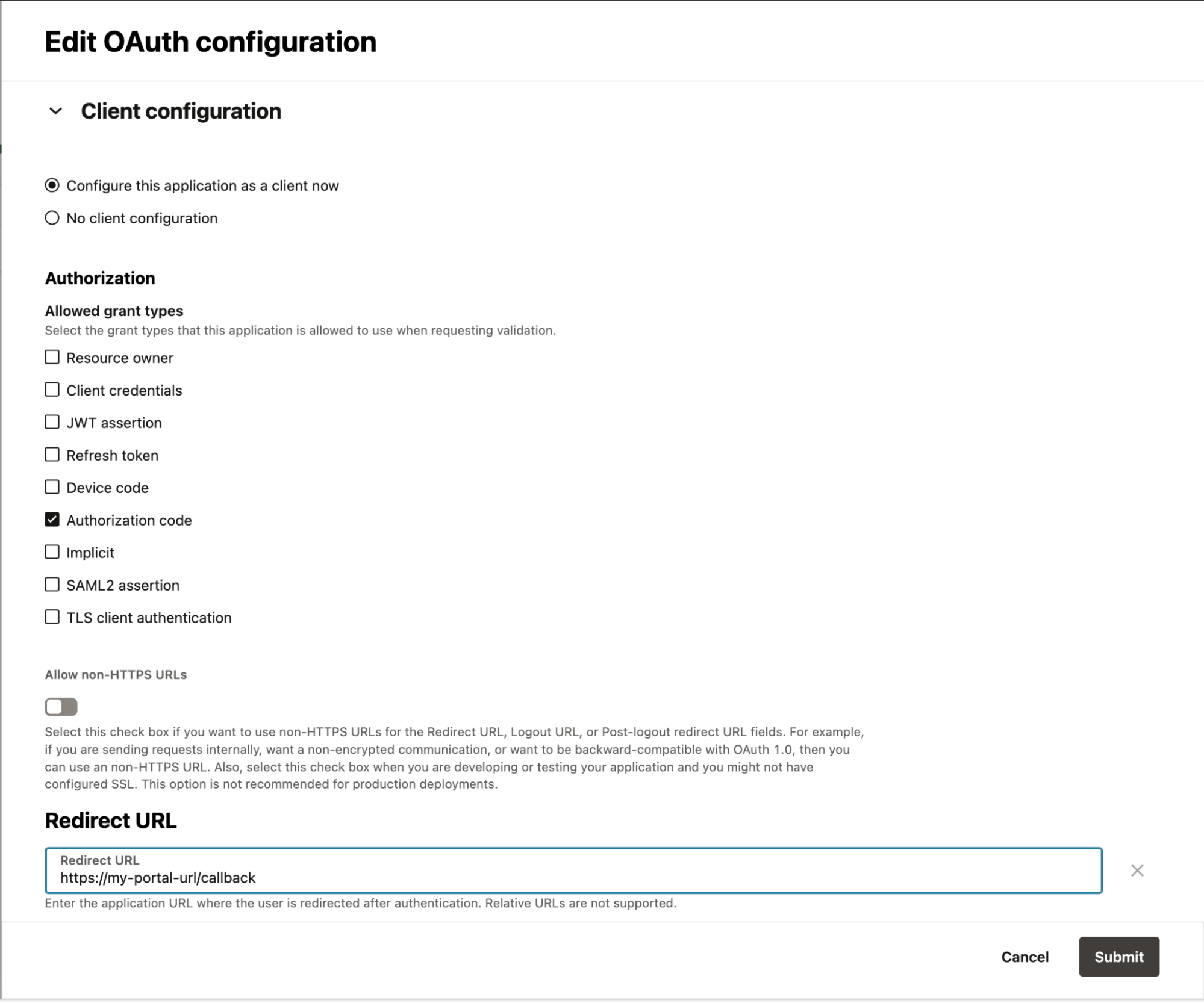
Select Submit to save the changes.
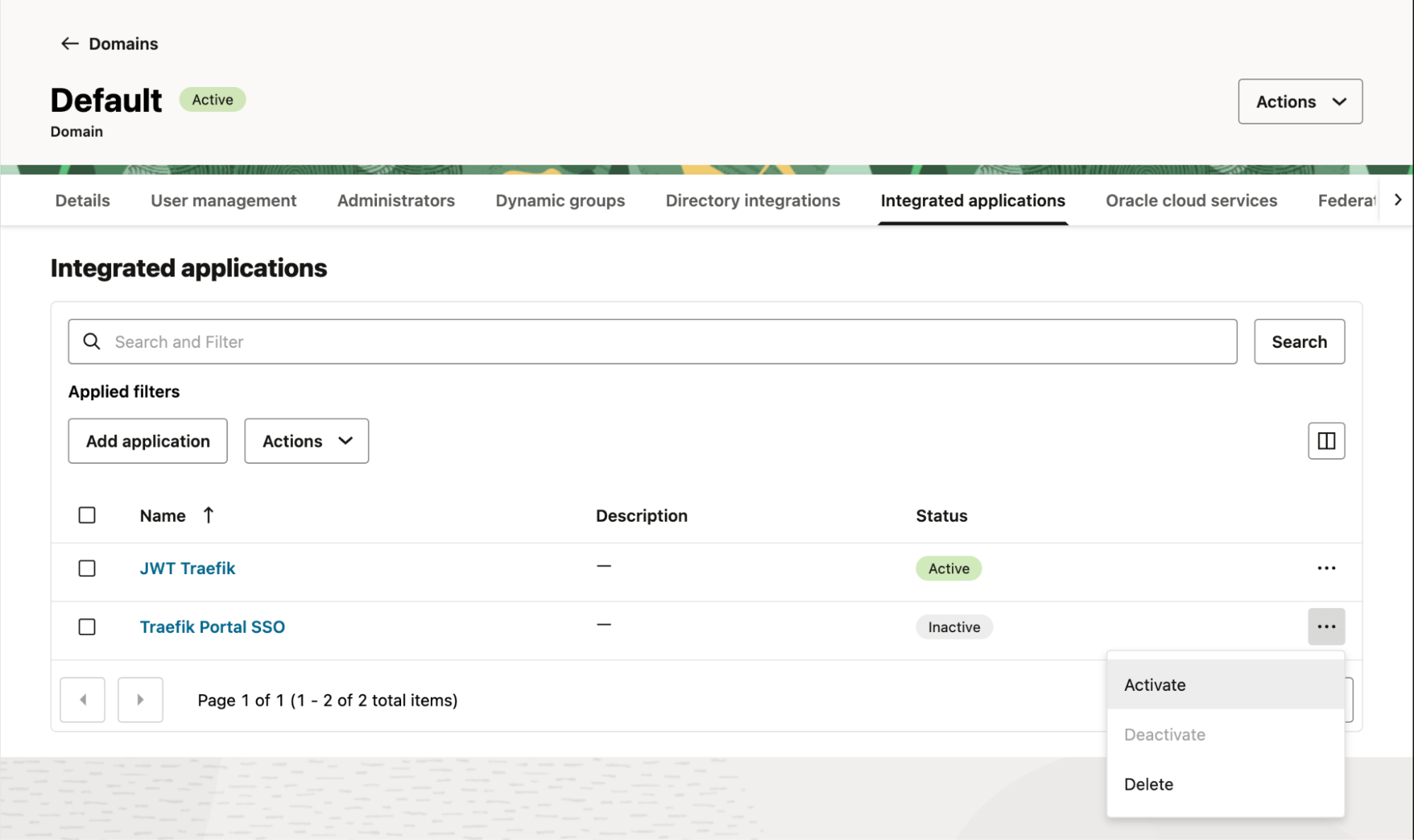
In the applications menu, select the ... icon next to the application you created and select Activate.
Retrieve Client Credentials
To retrieve the client credentials, select the application you created and navigate to the OAuth configuration tab.
In the OAuth configuration menu, Copy the Client ID and Client Secret.
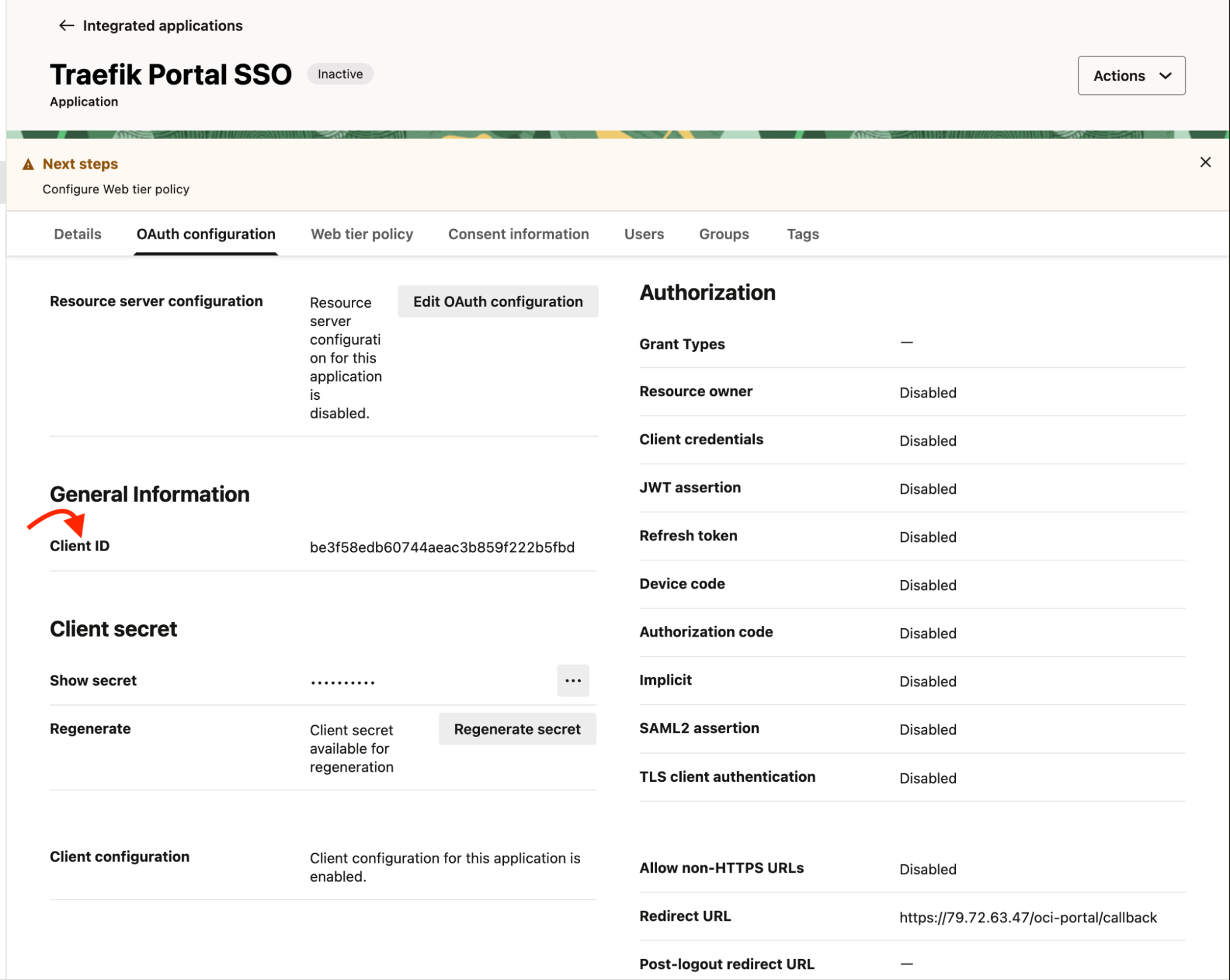
The Client Secret is generated automatically, you can regenerate it if needed.
Set the Issuer
In the domains menu, navigate to the Security tab and scroll down to the Oauth settings section.
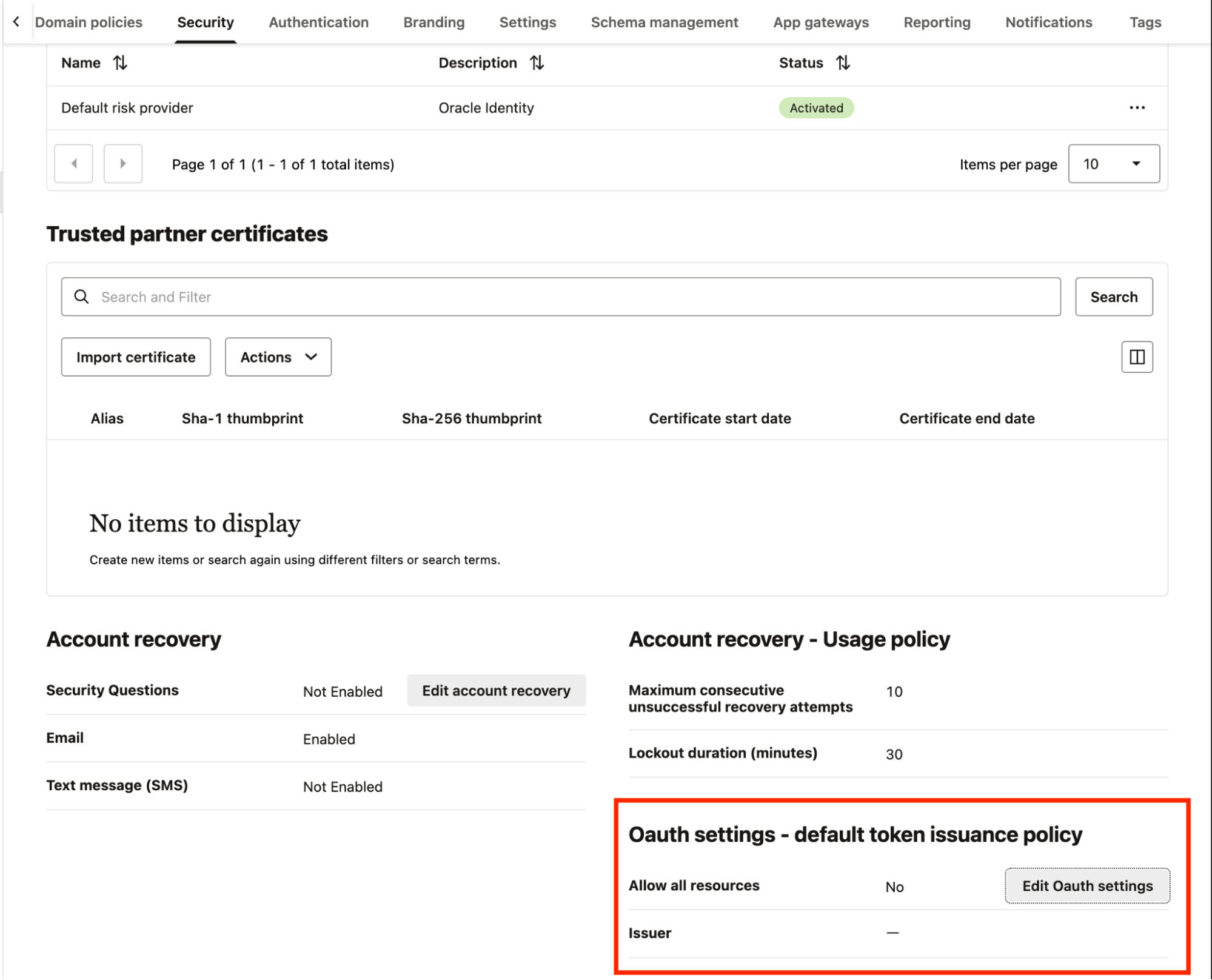
Next, select Edit OAuth settings and add the following:
- Issuer URL:
https://<Your_Domain_URL>.identity.oraclecloud.com
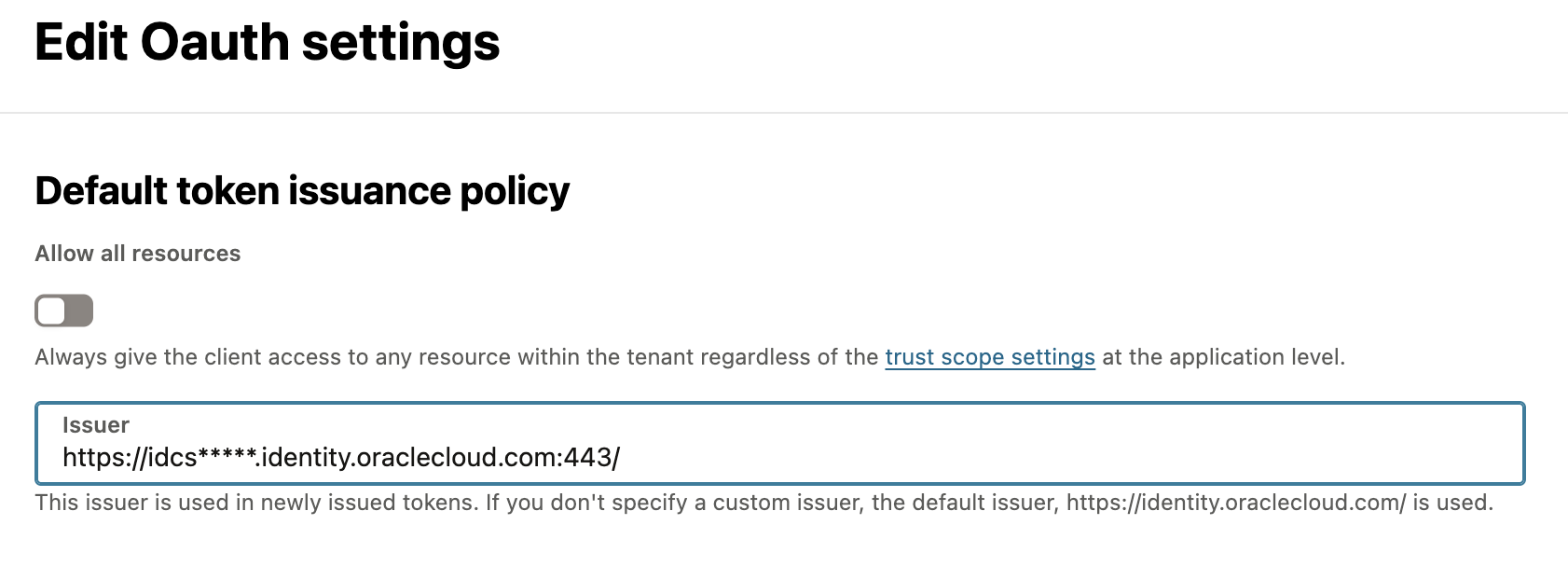
You can find the domain_url under Domains -> Details
Select Save Changes.
Configure SSO access to the Portal in Traefik Hub
To configure SSO access to the Traefik Hub API Portal, follow the steps in the Traefik Hub OIDC documentation:
Configure OIDC Gateway Authentication with JWT Tokens In Oracle IAM Identity Domains
To enable gateway access with JWT tokens, ensure the application allows the Client Credentials grant type.
Modify or Create the Application for Client Credentials
Create a new application using the steps above and edit the OAuth configuration to include the Client Credentials grant type.
To edit the OAuth configuration, select the application you created and navigate to the OAuth configuration tab.
In the OAuth configuration menu, select Edit OAuth configuration.
In the OAuth configuration settings, choose Client Credentials from the list of allowed grant types.
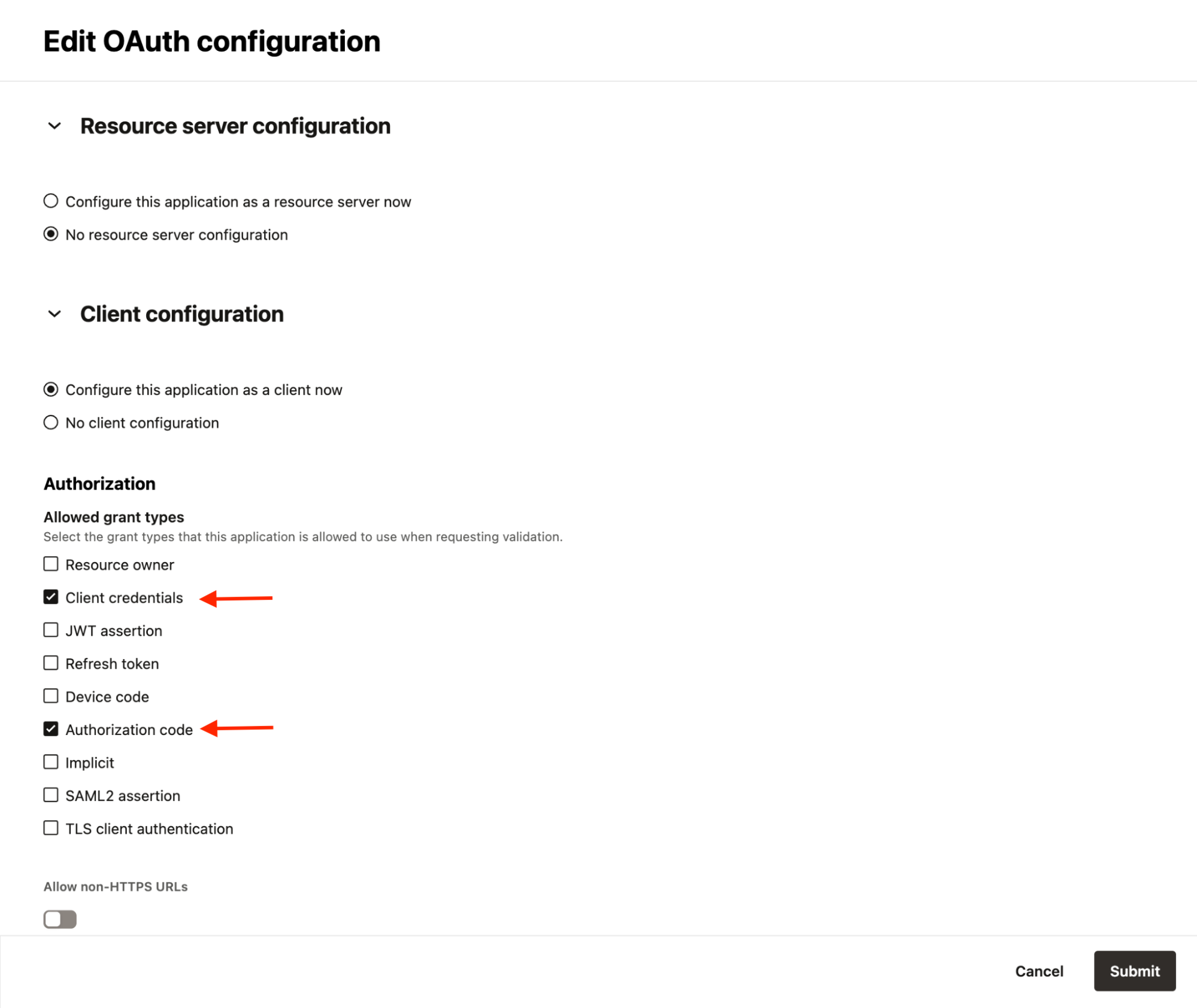
Ensure Authorization Code grant type is still enabled for portal SSO.
Test Token Retrieval
You can test the token retrieval by making the following request:
curl -X POST "<Your_Domain_URL>.identity.oraclecloud.com" \
-H "Content-Type: application/x-www-form-urlencoded" \
-d "grant_type=client_credentials" \
-d "client_id=YOUR_CLIENT_ID" \
-d "client_secret=YOUR_CLIENT_SECRET" \
-d "scope=urn:opc:idm:__myscopes__"
Configure Gateway JWT Authentication
To configure gateway JWT authentication, retrieve the JWKs URI from:
curl -X GET "https://<your-idcs-url>/.well-known/openid-configuration"
The JWKs URI will look like this:
https://idcs-****.identity.oraclecloud.com:443/admin/v1/SigningCert/jwk
Finally, continue the gateway JWT authentication configuration following the steps in the Traefik Hub OIDC documentation:
