Managed Applications
Traefik Hub Managed Applications bring full GitOps workflow to application registration and credential management.
Traditionally, API consumers first needed to sign in to the API Portal and carry out several manual steps before their application could call the Gateway.
With Managed Applications the publisher declares the consumer’s application as a Kubernetes CRD and links it to a Managed Subscription. No portal login or other action is required from the consumer—the entire registration and credential lifecycle is handled on their behalf.
Key Concepts
| Term | Description |
|---|---|
| Application | Logical consumer (mobile app, backend, partner system). Identified by an App ID issued by your IdP. |
| ManagedApplication | Defines and manages application identities, ownership, and authentication credentials through GitOps workflows. |
| Self-Service Application | An Application created by a developer via the portal. Managed Applications provide the GitOps alternative. |
| Managed Subscription | Grants runtime access to APIs only to the ManagedApplications it references. |
| Self-Service Subscription | Allows API consumers to subscribe their Applications to APIs—or entire API Bundles—directly from the API Portal. |
How It Works
- The Hub Agent syncs the Managed Application + hashed Secret to the platform (for API key authentication) or validates LDAP credentials (for LDAP authentication).
- During request-time Hub API Management matches the
appIdin the Managed Application and the ManagedSubscription rules. - Both valid credentials (API key, JWT, or LDAP) AND the application's subscription must be valid for the request to proceed. This zero-trust approach ensures credentials cannot be shared between applications.
- If everything lines up, the call proceeds and the APIPlan quotas/rate-limits are enforced.
How to Use Managed Applications
Define a ManagedApplication resource:
- ManagedApplication with Secret Reference
- Secret with data (base64)
- Secret with stringData (no base64)
- ManagedApplication with Inline Value
apiVersion: hub.traefik.io/v1alpha1
kind: ManagedApplication
metadata:
name: weather-mobile
namespace: apps
spec:
appId: weather-mobile # must match IdP client ID
owner: 67f67907ee260b44336a952e # Hub user UUID (sub/externalID)
notes: "For IOS & Android clients"
apiKeys:
- secretName: weather-mobile-key
title: mobile-key
apiVersion: v1
kind: Secret
metadata:
name: weather-mobile-key
namespace: apps
type: Opaque
data:
# echo -n "secret-api-key" | openssl dgst -SHAKE256 -xoflen 64 | awk '{ print $2; }' | tr -d "\n" | base64 -w0
key: NzJiZjE2ZGRlY2I3YTNlYzA0YjVjZTAyOTZmODVhMGFiOWQwNDkxMDUyNDNiNGI3OTI0YTM0MGYyNjUyM2U3ZDc0M2UyNDEyNmNlZDkzZTlkZGU2M2QxYjRmNzNjMjQyYzVmMGVkOTdjY2UzOTRhNWFlZTNlY2RiMzg2NmQ4NGY=
apiVersion: v1
kind: Secret
metadata:
name: weather-mobile-key
namespace: apps
type: Opaque
stringData:
# echo -n "secret-api-key" | openssl dgst -SHAKE256 -xoflen 64 | awk '{ print $2; }' | tr -d "\n"
key: 0617ed8b2664c25a1dfd25e9f594c79356bcb0ba4ea1f6c39e8140de0a8d917611030c486ad62754df770b13ad9e698ad163aa8ca3fda14adfbab4b5a837e302
apiVersion: hub.traefik.io/v1alpha1
kind: ManagedApplication
metadata:
name: weather-mobile-inline
namespace: apps
spec:
appId: weather-mobile-inline # must match IdP client ID
owner: 67f67907ee260b44336a952e # Hub user UUID (sub/externalID)
notes: "For IOS & Android clients with inline API key"
apiKeys:
# Use the raw SHAKE-256 hash directly (no base64 encoding needed)
# echo -n "secret-api-key" | openssl dgst -SHAKE256 -xoflen 64 | awk '{ print $2; }' | tr -d "\n"
- value: 0617ed8b2664c25a1dfd25e9f594c79356bcb0ba4ea1f6c39e8140de0a8d917611030c486ad62754df770b13ad9e698ad163aa8ca3fda14adfbab4b5a837e302
title: mobile-key
The examples above demonstrate three different approaches for managing API keys:
Secret with data field: Uses base64-encoded values. The data field requires you to base64-encode the SHAKE-256 hash. This approach provides an extra layer of encoding but requires additional steps during key generation.
Secret with stringData field: Stores the raw SHAKE-256 hash directly without base64 encoding. Kubernetes automatically handles the base64 encoding when storing the secret. This approach is simpler and reduces the chance of encoding errors.
Inline value: Embeds the raw SHAKE-256 hash directly in the ManagedApplication resource. This approach eliminates the need for a separate Secret resource.
Choose the approach that best fits your security policies and operational preferences. The stringData approach typically offers the best balance of simplicity and security for most use cases.
Link that application to an API via ManagedSubscription:
apiVersion: hub.traefik.io/v1alpha1
kind: ManagedSubscription
metadata:
name: weather-mobile-sub
namespace: apps
spec:
managedApplications:
- name: weather-mobile
apis:
- name: weather-api
apiPlan:
name: standard-plan
Configuration Options
| Field | Required | Description |
|---|---|---|
| appId | Yes | Unique identifier for an application. |
| owner | Yes | Hub user identifier of the application owner: use the OIDC sub, an external IdP externalID, or the long user ID visible in the Hub dashboard URL when you are using the built‑in Hub IdP. |
| notes | No | Free-form notes for operators. |
| apiKeys[] | No | Defines the API keys for the application. Up to 100 keyed items. |
| apiKeys[].title | No | Human-readable key label shown in metrics. |
| apiKeys[].secretName | No (One of secretName or value) | Name of an Opaque Secret whose data.key field stores the SHAKE-256 hash of the raw key. |
| apiKeys[].value | No (One of secretName or value) | SHAKE-256 hash inline (max 4096 chars). |
| apiKeys[].suspended | No | Set true to disable this key without deleting. |
Provide either secretName or value in each apiKeys[] item and not both.
When to Use Managed Applications
- Your organisation is fully GitOps and developers should not touch the portal.
- App IDs already exist in your IdP (OIDC client IDs, external IDs) and must be recognised by the Gateway before a human ever logs in.
- You want publishers (cluster admins / platform engineers) to issue or rotate API keys on behalf of consumers.
- Duplicate App ID: If a Self-Service and Managed Application share the same App ID, the
ManagedApplicationversion wins. - Static Analyzer: The Hub Static Analyzer warns whenever more than one
ManagedApplicationin the same namespace defines the sameappId. When this occurs, Hub keeps only theManagedApplicationwhose resource name comes first in alphabetical order and disregards the others.
API keys are bound to specific ManagedApplication resources and their subscriptions.
If you reuse the same API key across multiple ManagedApplication resources, each application must have its own valid ManagedSubscription to access an API. An application without a subscription
will receive a 403 Forbidden response, even if another application using the same key has valid access.
This design prevents unauthorized access and ensures that API permissions are explicitly granted on a per-application basis, rather than relying solely on key possession.
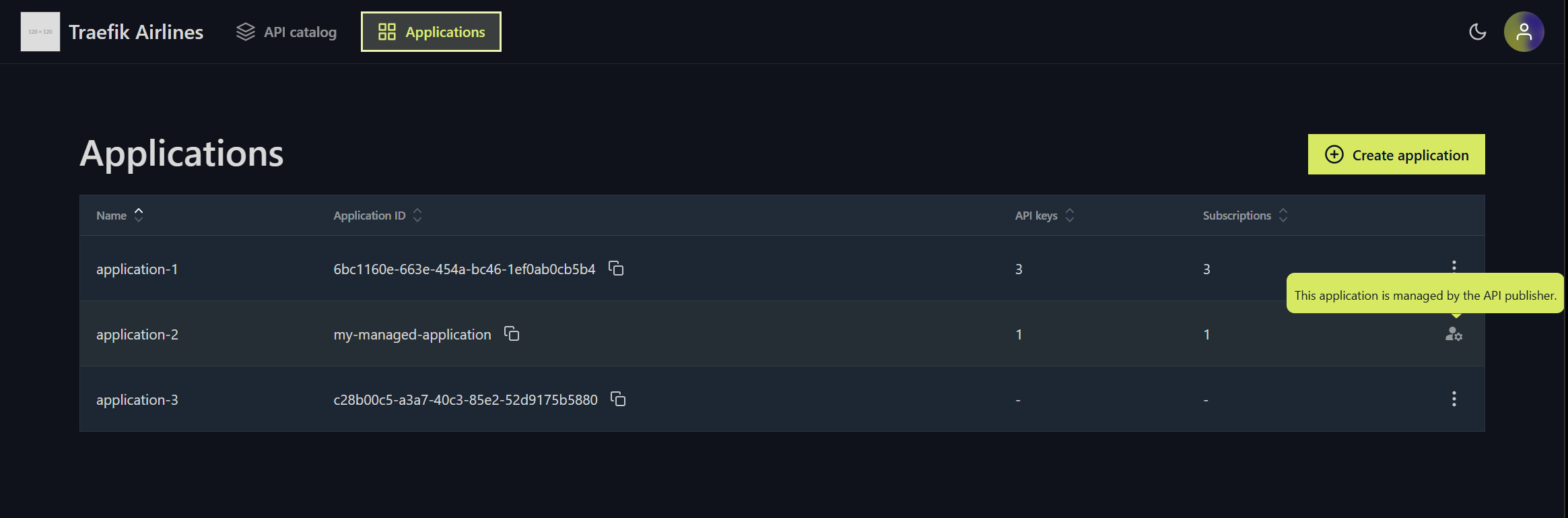
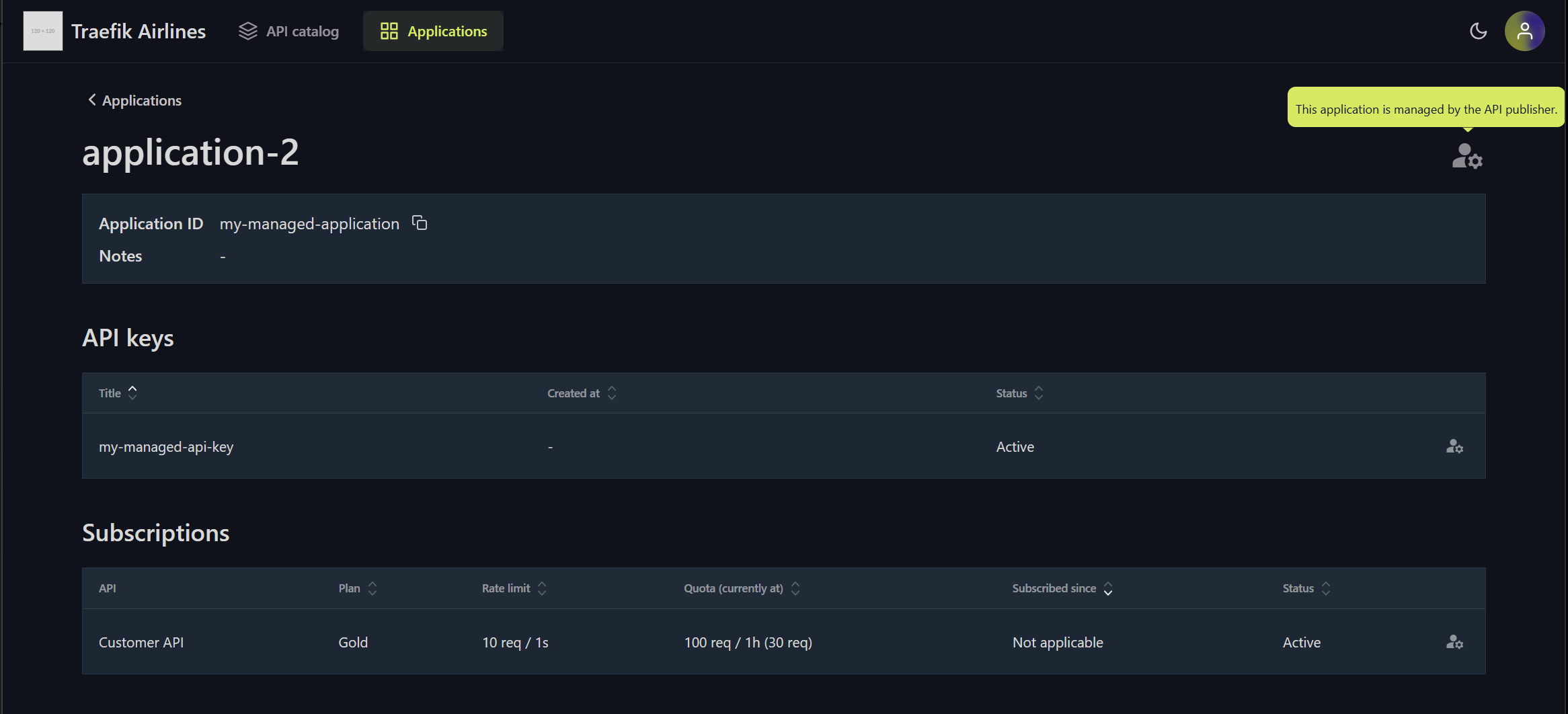
Managed Application Experience in the API Portal
The API Portal provides an interface for viewing managed applications. This allows you to see all applications and access their details.
- API Portal - Managed Applications List
- API Portal - Managed Application Details
LDAP Applications
When using LDAP authentication for API authentication, ManagedApplications work differently than with API key authentication.
How LDAP Applications Work
With LDAP authentication configured via APIAuth:
- Applications authenticate using HTTP Basic Authentication with LDAP credentials
- The username from Basic Auth must match the
appIdin a ManagedApplication - The ManagedApplication must have a valid ManagedSubscription granting API access
- No API keys are required—authentication is handled entirely by LDAP
LDAP Application Example
apiVersion: hub.traefik.io/v1alpha1
kind: ManagedApplication
metadata:
name: john-doe-app
namespace: default
spec:
appId: app.john.doe # Machine user - authenticates API requests
owner: john.doe # Human user - manages app in portal
notes: "Application for John Doe authenticated via LDAP"
# No apiKeys needed - authentication done via LDAP
Service Account Example
For service accounts or machine users in LDAP:
apiVersion: hub.traefik.io/v1alpha1
kind: ManagedApplication
metadata:
name: inventory-service
namespace: default
spec:
appId: svc.inventory # Must match LDAP service account username
owner: platform.head
notes: "Inventory microservice using LDAP service account"
LDAP Application Requirements
When using LDAP authentication:
- appId must match LDAP username: The
appIdfield must exactly match the username in your LDAP directory - No API keys required: The
apiKeysfield should be omitted or empty - ManagedSubscription required: Applications still need a ManagedSubscription to access APIs
- LDAP credentials for authentication: Applications authenticate using their LDAP username and password via HTTP Basic Auth
Making API Requests with LDAP
Applications use HTTP Basic Authentication with their LDAP credentials:
curl -i https://api.example.com/products \
-u john.doe:ldap-password \
-H "Accept: application/json"
The authentication flow:
- Traefik Hub validates the LDAP credentials against the LDAP server
- Matches the username (
john.doe) to theappIdin the ManagedApplication - Checks the ManagedSubscription for API access
- Applies APIPlan rate limits if configured
- Forwards the request to the backend service
Mixing Authentication Methods
You can have different authentication methods across namespaces within the same workspace:
- API Key namespace: Configure APIAuth with
apiKey: {}, and ManagedApplications includeapiKeys - LDAP namespace: Configure APIAuth with LDAP settings, and ManagedApplications omit
apiKeys - JWT namespace: Configure APIAuth with JWT settings
Each namespace can only have one active authentication method (determined by the APIAuth resource with isDefault: true in that namespace).
However, different namespaces within the same workspace can use different authentication methods simultaneously.
Related Content
- Learn more about the API object in its dedicated section.
- Learn more about the
APIPlanresource in its dedicated section. - Learn more about the Managed Subscription resource in its dedicated section.
- Learn more about the Self-Service Subscription resource in its dedicated section.
- Learn about LDAP Authentication for API access.
