User Management
Control access to your APIs and documentation.
Introduction
In Traefik Hub, Users are granted access to your APIs with Groups. Users can belong to multiple Groups.
The Identity Provider is the source of truth for Users and Groups. It is responsible for authenticating the users and telling Traefik Hub what groups they belong to. You can choose between the Traefik Hub (Internal IdP) embedded Identity Provider, LDAP, Keycloak, Okta, or any generic OIDC mechanism to manage authentication.
Traefik Hub uses the embedded IdP as default.
Throughout the documentation, the term Users refers to people browsing the Portal, and the term Consumers refers to the machine to machine consumption of APIs.
Users can have many Consumers attached to their accounts.
Consuming APIs & Authorizations
APICatalogItem define which APIs are visible on the developer portal. On the portal, a user can create an Application. What an Application can consume is then defined by a ManagedSubscription, which specifies access to specific APIs. Alternatively, users can also utilize a Self-Service subscription to request access.
| Group Name | Visible APIs (via CatalogItem) |
|---|---|
| Group AB | API A & API B |
| Group C | API C |
For example, if an Application is associated with both Group AB and Group C, it will see API A, API B, and API C on the portal.
Consuming APIs - API Keys & JWT
When configuring the authorization system with API keys, users will generate keys from the Portal. Consumers will send that key to authenticate themselves.
When configuring the authorization system with JWT. Consumers won't need API keys but will need to reference the User ID (which is acting on behalf on) in the token.
Users
From the Dashboard, you can see known users. Known users are, depending on your configuration:
- Users who have connected to the Portal (OIDC use case)
- Synchronized Users (Keycloak / Okta use case)
- LDAP-authenticated Users (LDAP use case)
- Every User (Internal IdP use case)
Synchronized Users (Keycloak / Okta / LDAP) will be listed in the Traefik Hub after a first successful login (online mode only).
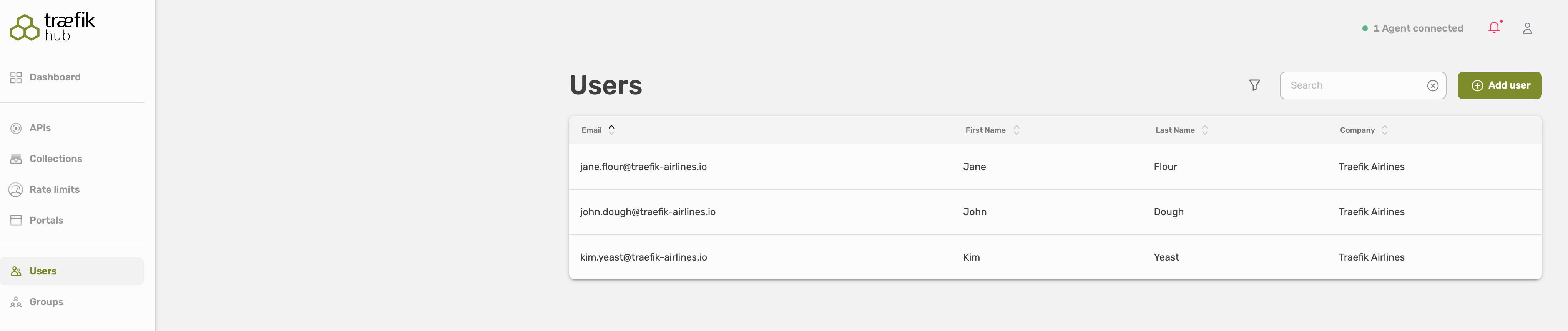
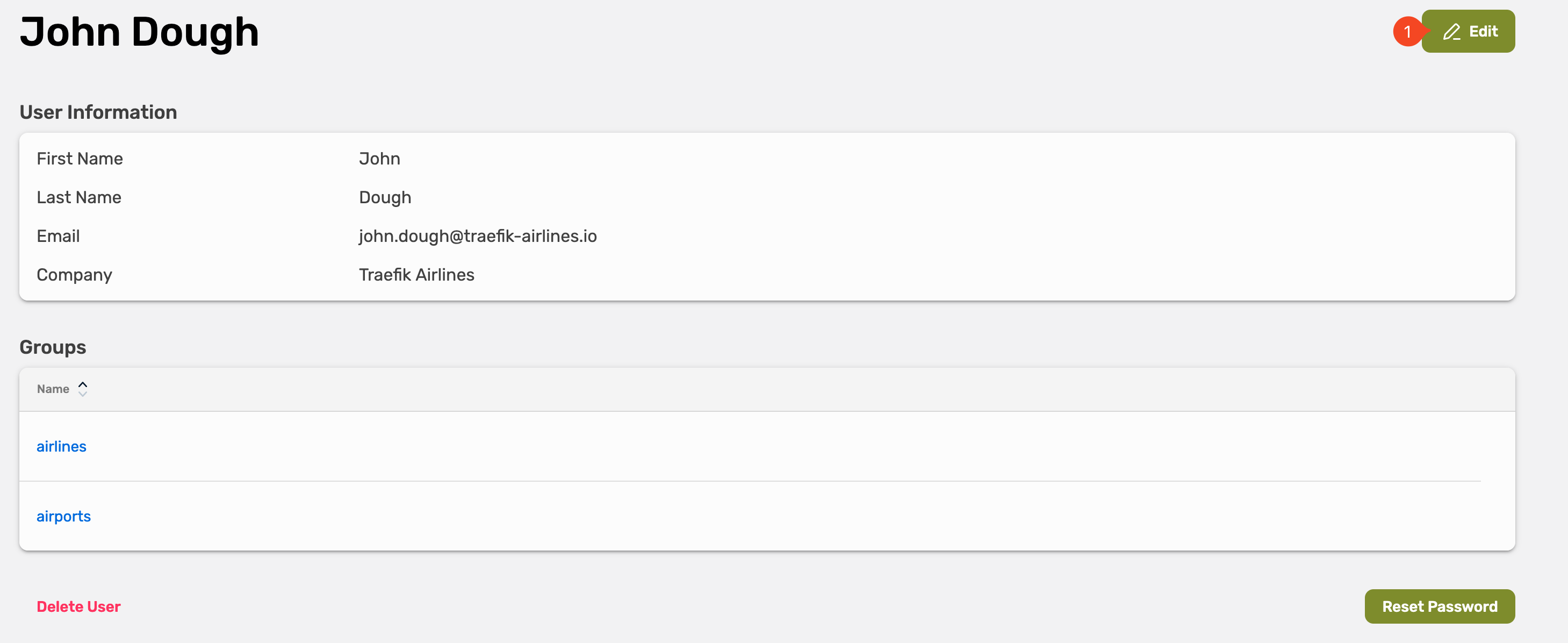
Each User contains the following information:
- First Name
- Last Name
- Email Address
- Company
- Group(s)
Add a User
Select Users, here you will see all existing user, and you can validate and adjust their permissions and groups.
Select Add user in the right top corner to add a new user.
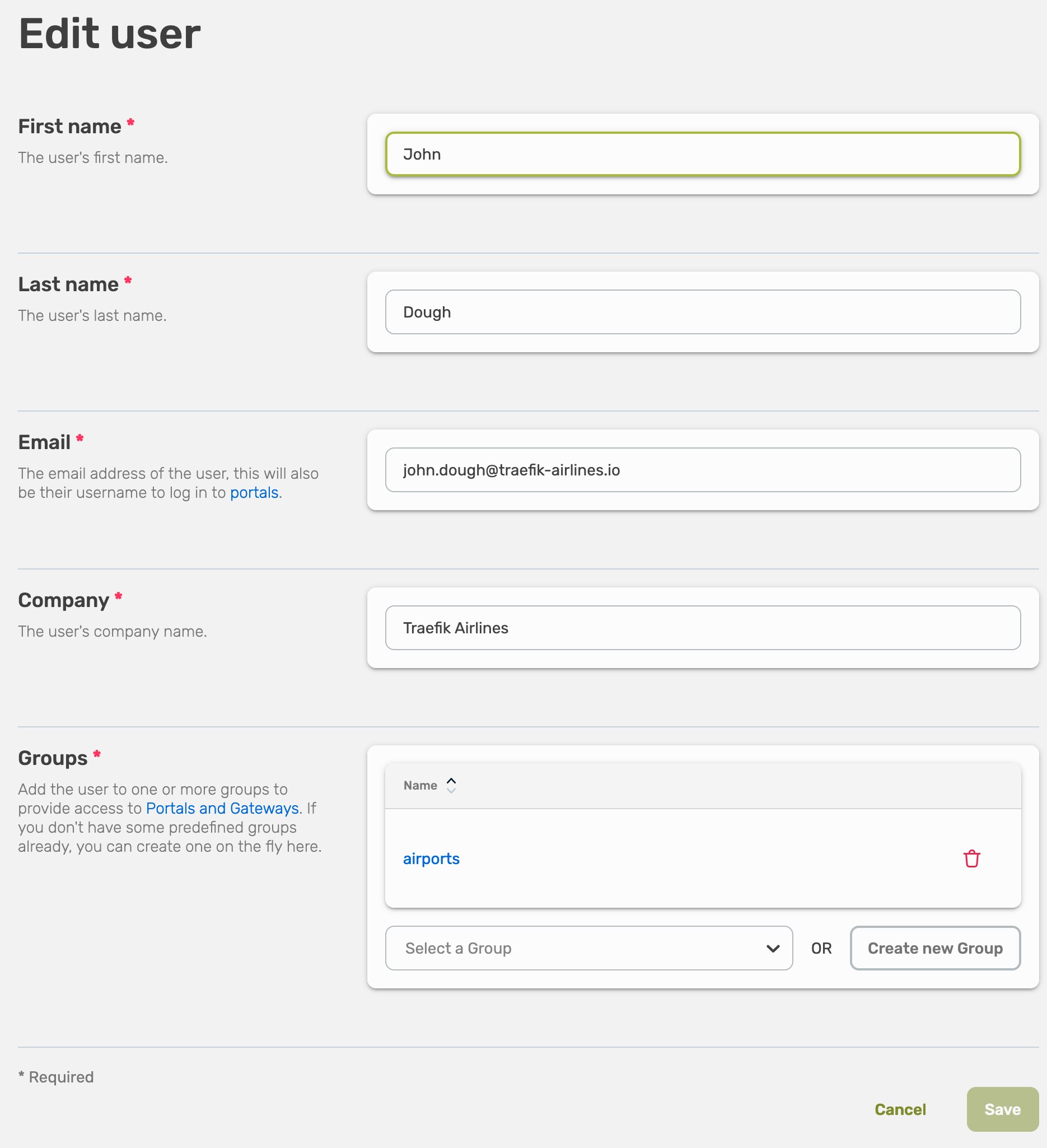
Fill out the form, all fields are required.
- First name
- Last name
- Company
- Groups
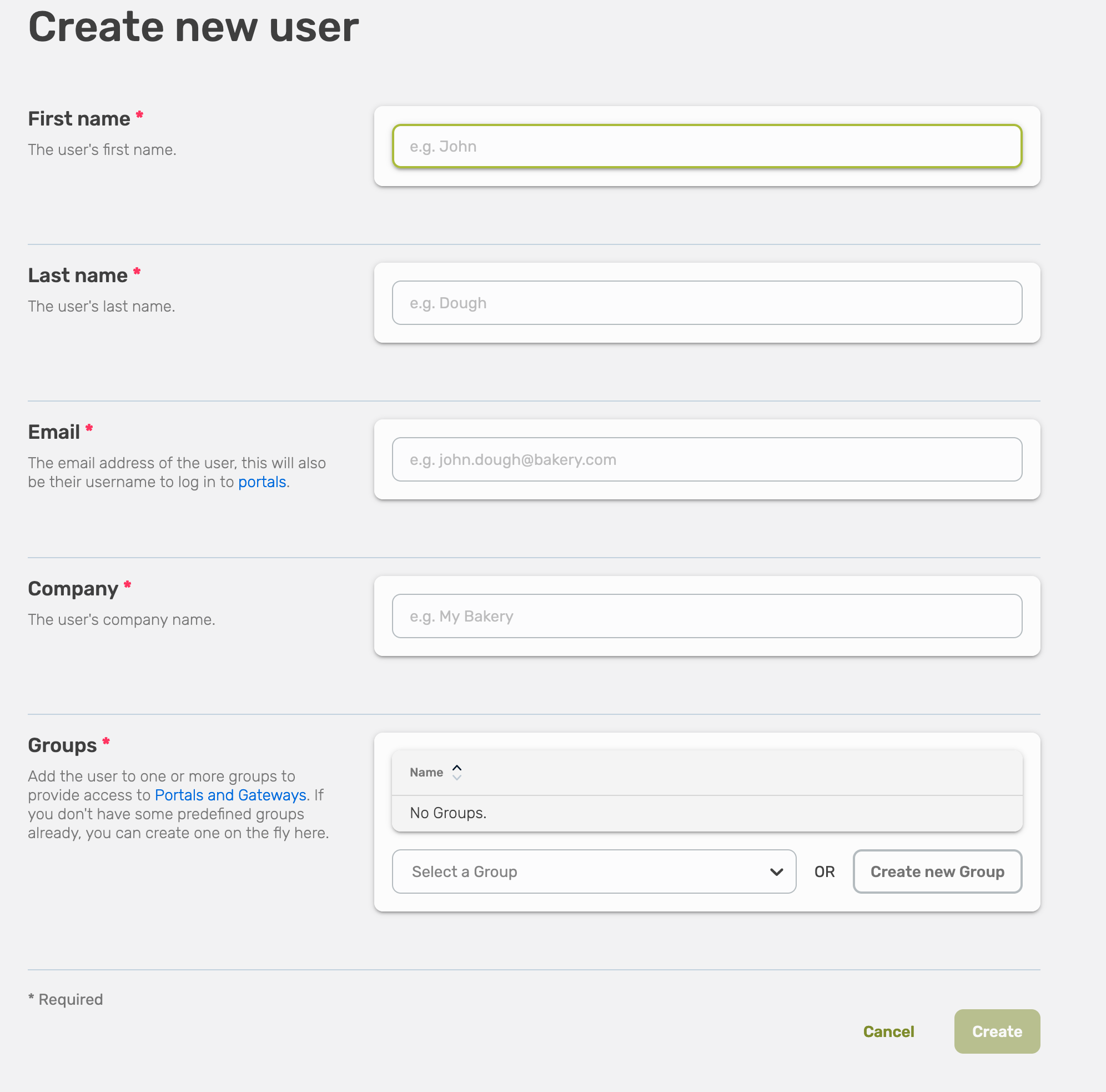
Every user has to be part of a user group, it is not possible to assign an individual user to an API or API collection.
You can assign the user to an already existing user group, or you can create a new one.
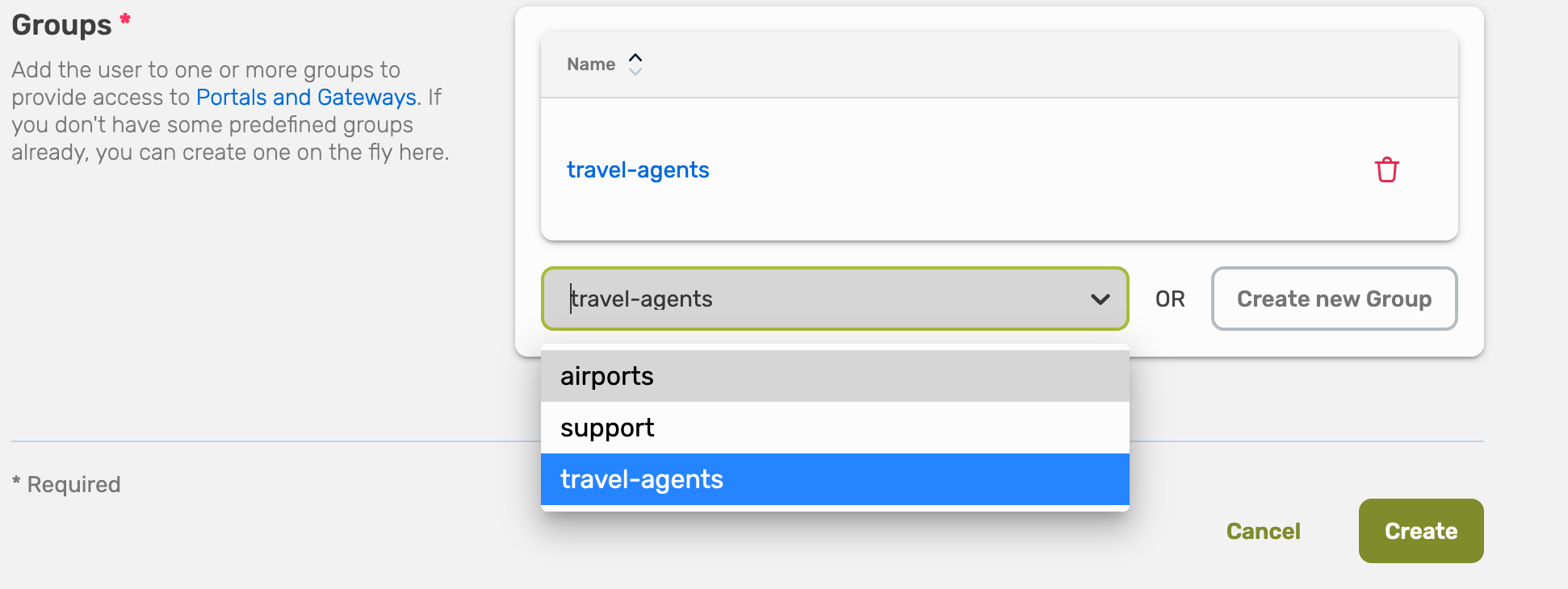
Choose an existing user group and select Save.
If you want to create a new user group, choose Create new User Group.
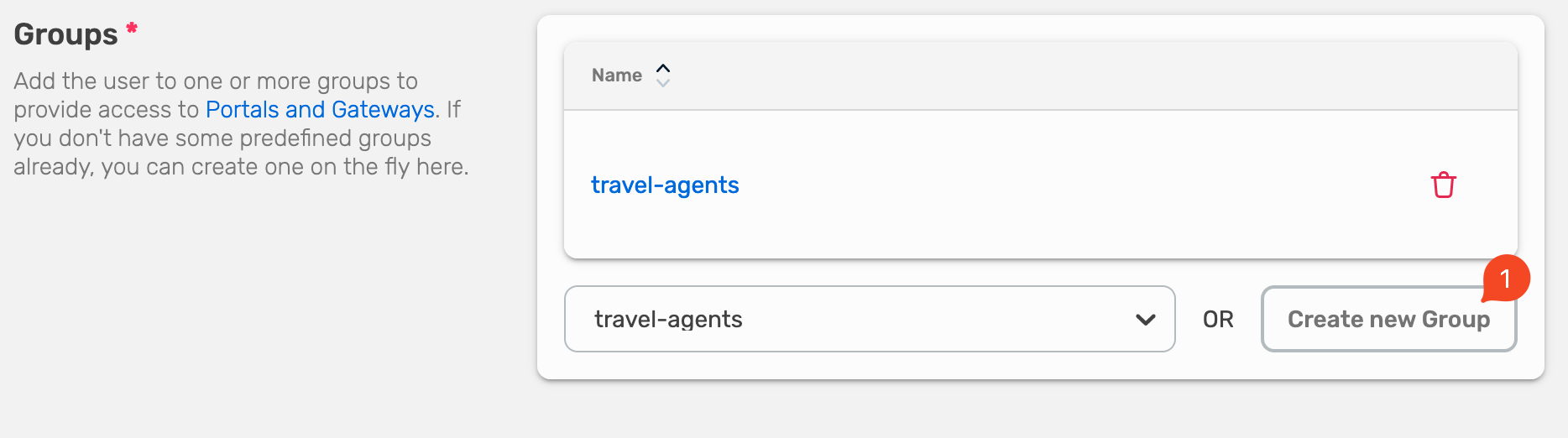
Fill out the name of the new user group and select Create.

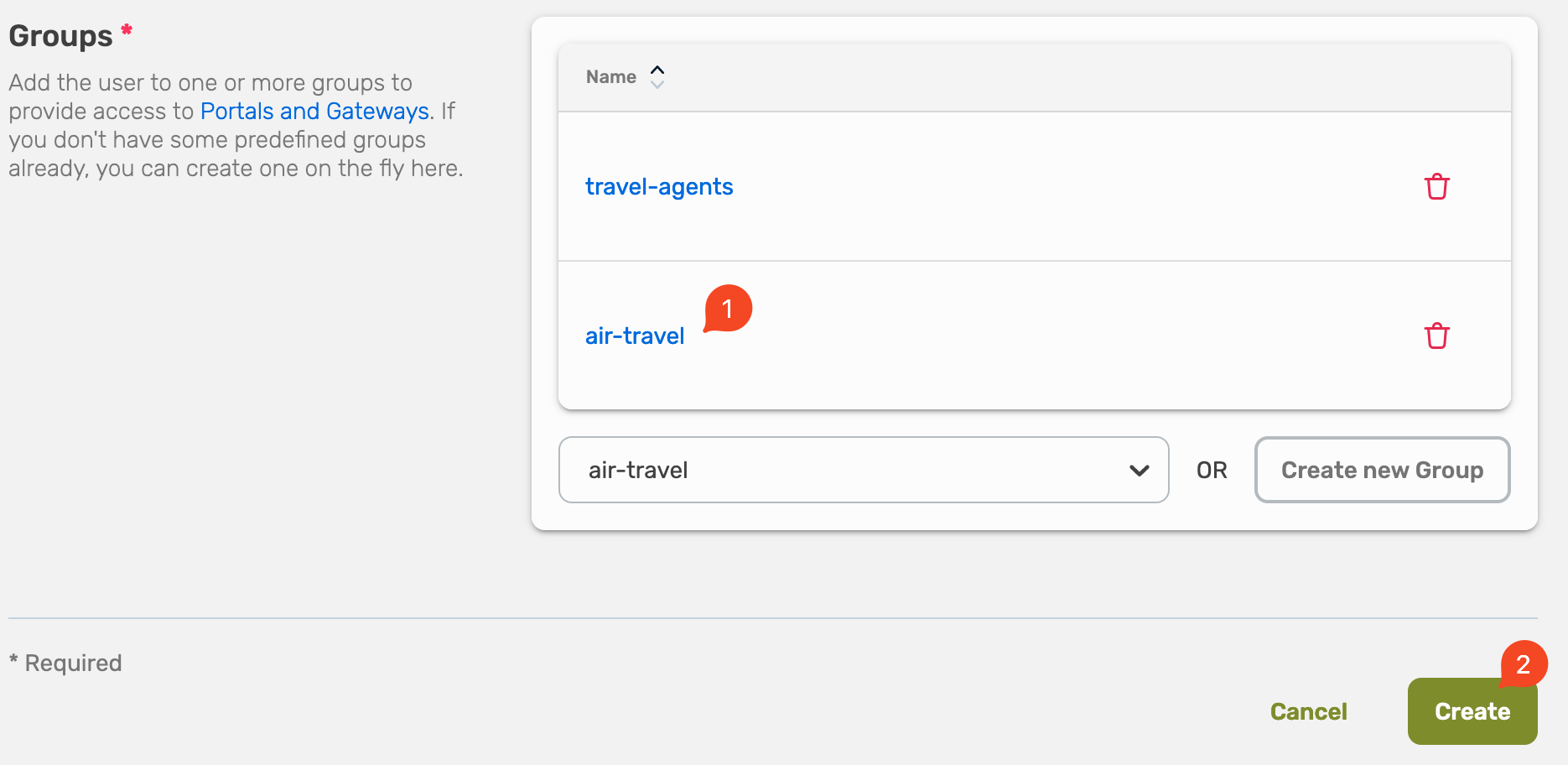
Now you will see that the new user is part of the user group, select Save to finish the process.
Edit a User
To change user details—such as a user’s email, or contact information—edit the user account.
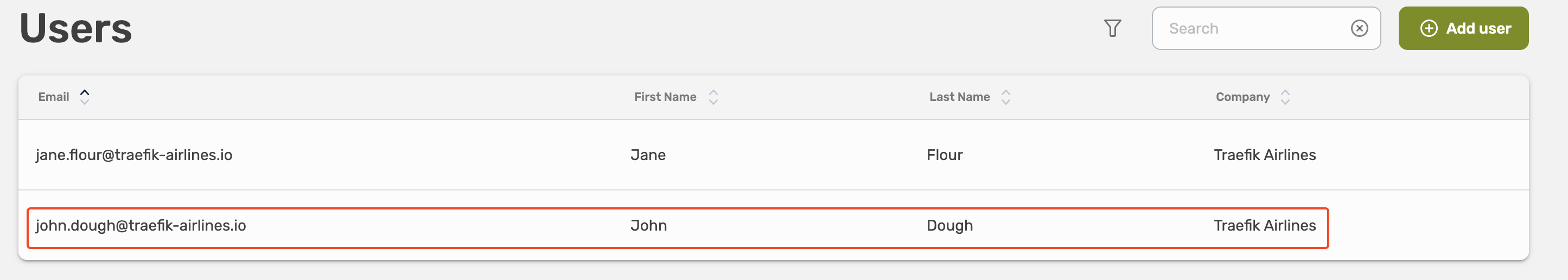
Select Users, here you will see all existing user, and you can validate and adjust their permissions and groups.
Select the user you want to edit.
This will show you the overview about the user. Now select Edit in the top right corner.
Adjust the settings and select Save.
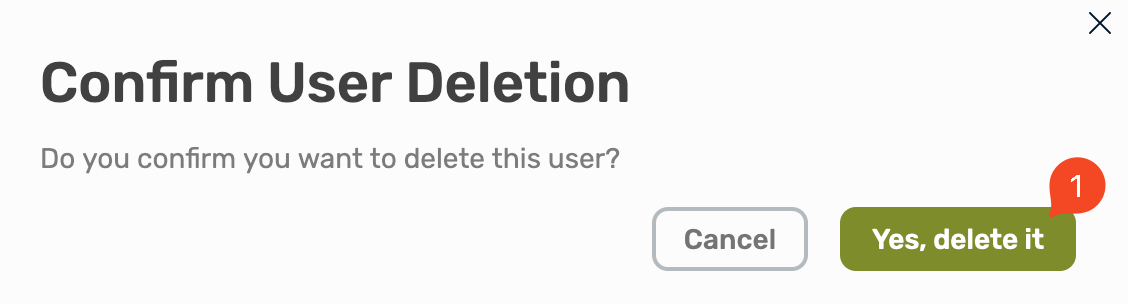
Delete a User
To delete a user.
Select Users, here you will see all existing user, select the user you want to delete.

Now select Delete User in the left bottom.
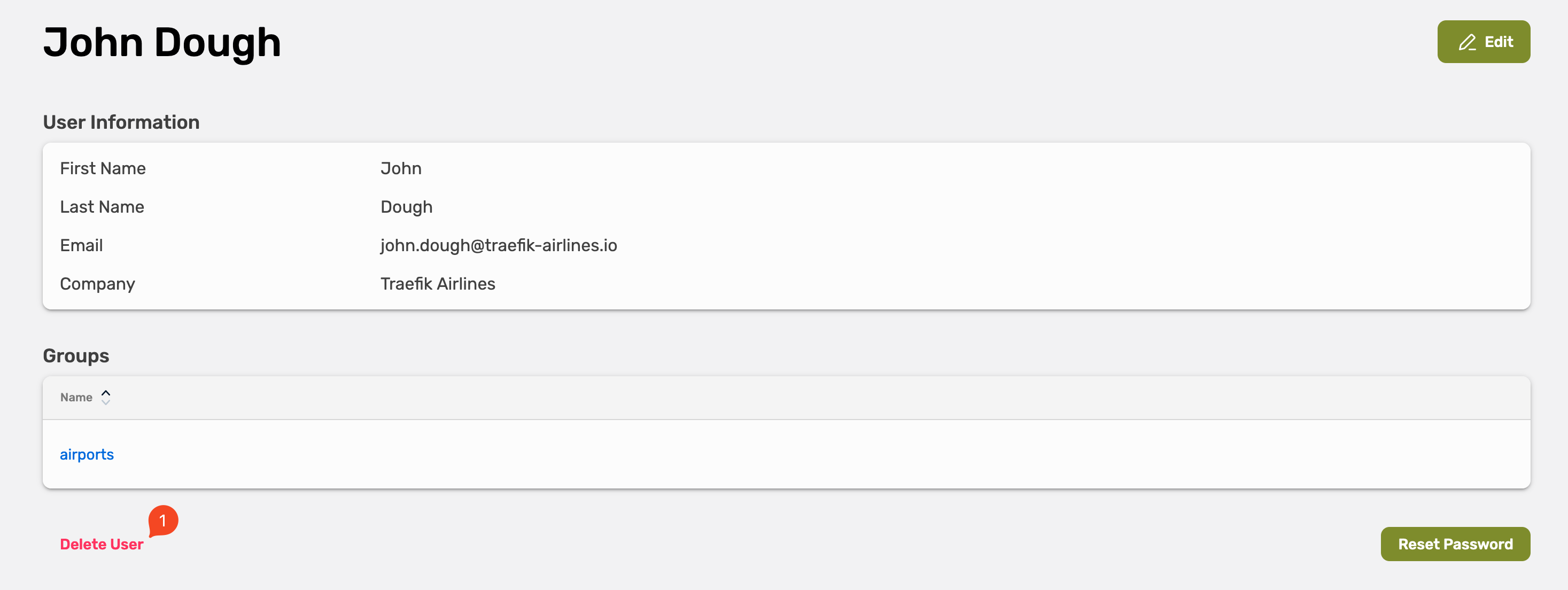
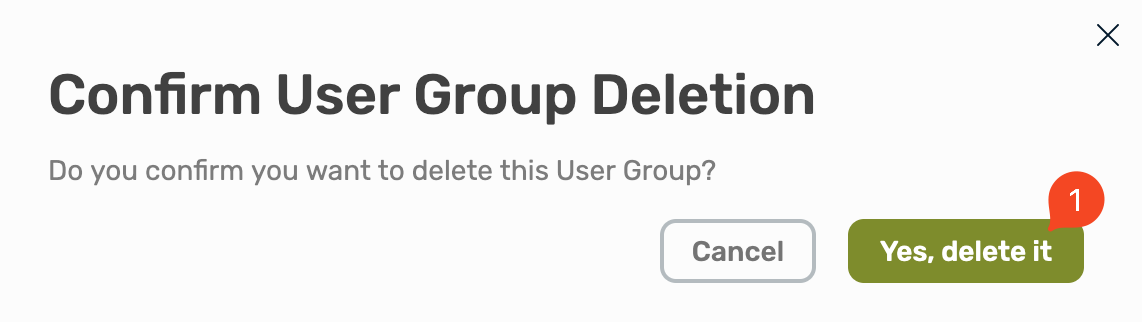
Confirm the removal by selecting Yes, delete it.
Reset a User Password
Select Users, here you will see all existing user, select the user where you want to reset the password.
Select Reset password
User Groups
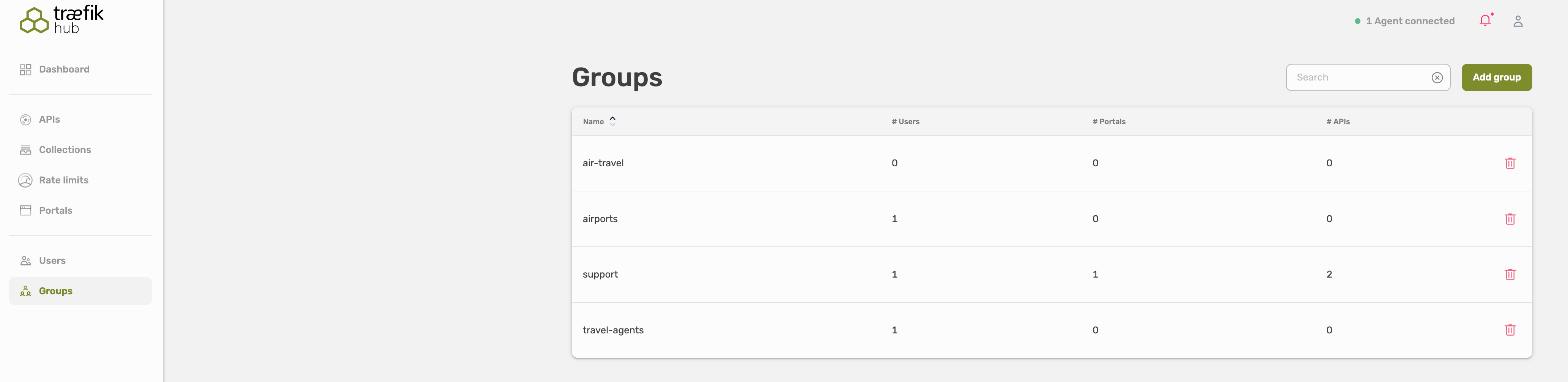
Groups don't carry additional information, they are a means of categorizing users and referencing these categories later in API Catalog Item.
LDAP Groups
When using LDAP authentication, groups are synchronized from your LDAP directory server.
How LDAP Groups Work
LDAP groups are retrieved using the memberOf attribute:
- Static Group Retrieval: Groups are read directly from the user's
memberOfattribute in LDAP - No Nested Groups: Traefik Hub does not perform nested group lookups or dynamic queries
- Automatic Synchronization: In online mode, groups are synchronized when users authenticate to the portal
- Group-Based Access: Portal and API access can be controlled using LDAP group memberships
LDAP Group Configuration
LDAP groups are configured in the APIPortalAuth resource:
apiVersion: hub.traefik.io/v1alpha1
kind: APIPortalAuth
metadata:
name: ldap-portal-auth
namespace: apps
spec:
ldap:
groups:
memberOfAttribute: memberOf
# ... other LDAP configuration
LDAP Group Synchronization
Online Mode:
- Groups are synchronized from LDAP when users log in to the portal
- Group memberships are updated with each user authentication
- Groups appear in the Traefik Hub Dashboard after first user login
- You can view LDAP-synchronized groups in the Groups section
Offline Mode:
- Groups are used for authentication but not synchronized to the platform
- Group information is not visible in the Dashboard
- Access control still works based on LDAP group membership
LDAP Group Format
LDAP groups are typically stored as Distinguished Names (DNs) in the memberOf attribute:
memberOf: cn=developers,ou=groups,dc=example,dc=org
memberOf: cn=managers,ou=groups,dc=example,dc=com
Traefik Hub extracts the Common Name (CN) from the group DN for display and access control:
cn=developers,ou=groups,dc=example,dc=org→developerscn=managers,ou=groups,dc=example,dc=com→managers
Using LDAP Groups for Access Control
LDAP groups can be referenced in APICatalogItem to control API visibility:
apiVersion: hub.traefik.io/v1alpha1
kind: APICatalogItem
metadata:
name: internal-api-catalog
namespace: apps
spec:
title: "Internal APIs"
groups:
- developers
- managers
apis:
- name: internal-api
namespace: apps
Users who belong to the developers or managers LDAP groups will see these APIs in the portal.
Differences Between IdP Group Handling
| Feature | LDAP | Keycloak/Okta (Direct Integration) | OIDC (Generic) | Internal IdP |
|---|---|---|---|---|
| Group Source | LDAP memberOf attribute | IdP group claims | IdP group claims | Manually created in Hub |
| Nested Groups | Not supported | Depends on IdP | Depends on IdP | N/A |
| Group Creation | Automatic from LDAP | Automatic from IdP sync | On login only | Manual only |
| Offline Mode | Authentication only (no sync) | Supported (self-hosted IdP) | Supported (self-hosted IdP) | Not supported (no platform connection) |
| Group Updates | On each login | Periodic sync + login | On login only | Manual only |
Troubleshooting LDAP Groups
Groups not appearing in Dashboard:
- Verify you're running in online mode (offline mode doesn't sync groups)
- Check that the user has logged in at least once
- Ensure the
memberOfAttributeis correctly configured in APIPortalAuth - Verify the LDAP user has the
memberOfattribute populated
Users can't access APIs despite being in the correct LDAP group:
- Check the APICatalogItem references the correct group name (CN only, not full DN)
- Verify the user has logged in since joining the group (re-authentication may be required)
- Ensure the APIPortalAuth is correctly configured and active
Group names appear as full DNs:
- This may indicate the
memberOfattribute contains nested groups or is misconfigured - Verify your LDAP schema and
memberOfoverlay configuration (OpenLDAP) - Check that groups use standard LDAP naming conventions
Create a Group
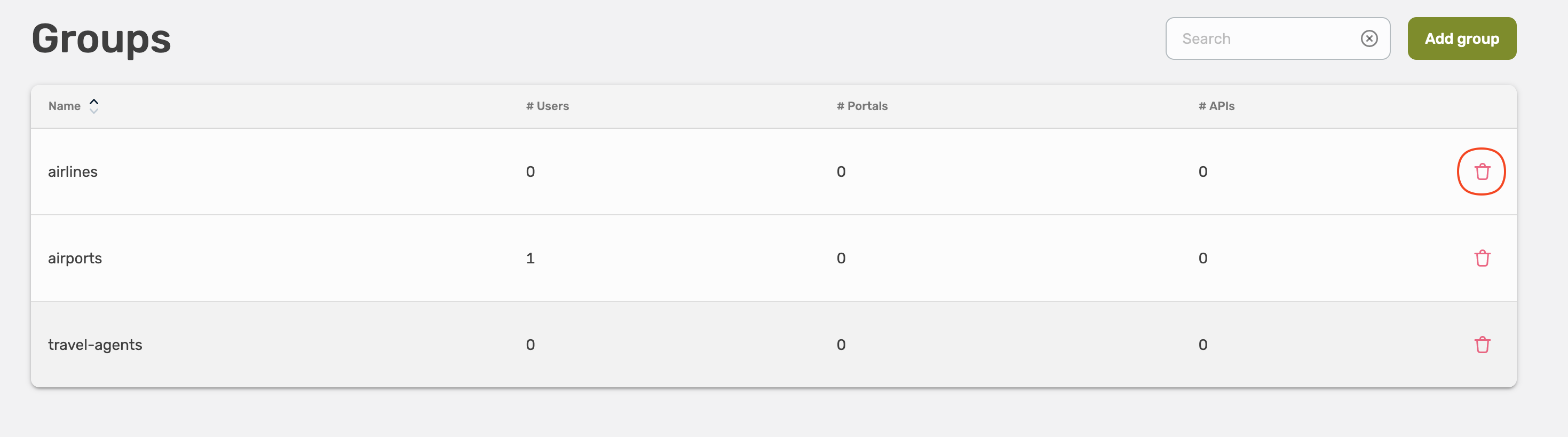
Select Groups, here you will see an overview about all user groups.
To create a new user group, select Add group on the right top corner.
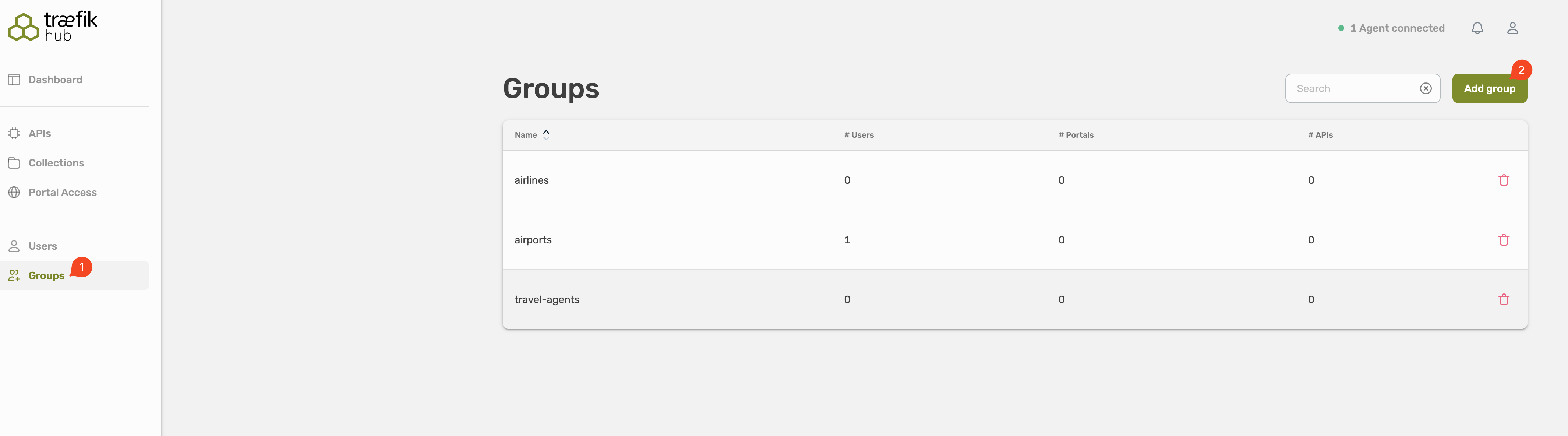
Delete a Group
It is only possible to remove empty groups!
Select the trash icon on the right site to remove a group.