API Management Offline Mode
Traefik Hub API Management (APIM) Offline Mode enables you to deploy and operate comprehensive API management capabilities without requiring connectivity to the Traefik Hub Online Dashboard. This mode is designed for air-gapped environments, regulated industries, or scenarios where external communication is restricted while still maintaining full API management functionality.
API Management Offline Mode is only available on Kubernetes and can only be enabled when creating a new gateway. You cannot switch an existing gateway to offline mode.
Prerequisites
- License Requirement: Offline Mode is a licensed feature. Access to this feature must be granted by the Traefik Labs sales team.
- Kubernetes Cluster: API Management Offline Mode is only supported on Kubernetes.
- License Token: Your license token must include the offline claim to enable this feature.
Enabling API Management Offline Mode
API Management Offline Mode is enabled through the Traefik Hub Online Dashboard during gateway creation. You can now enable both Offline Mode and API Management features simultaneously.
Step-by-Step Process
-
Navigate to Traefik Hub Online Dashboard: In the Traefik Hub Online Dashboard, go to the Gateways section and select "Create new gateway".
-
Configure Gateway Settings: Fill in your gateway name and other details.
-
Enable Both Offline Mode and API Management: Toggle both the "Offline gateway" switch and "API management features" switch in the gateway creation form.
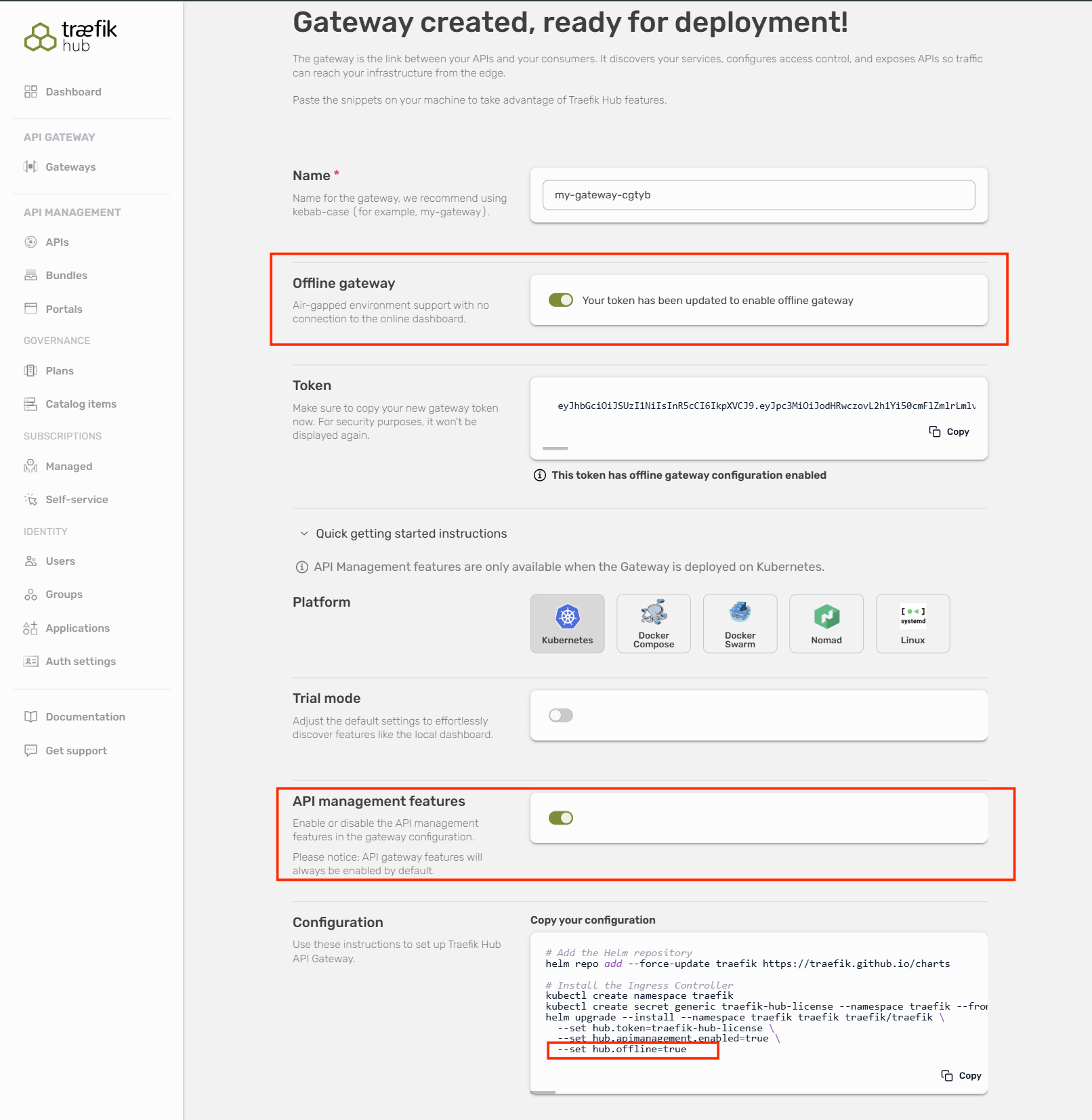
-
Copy Updated Token: Once offline mode is enabled, copy the updated token that now includes the offline configuration. The APIM toggle updates the installation snippet to include the necessary CLI flags.
-
Deploy with Updated Configuration: Use the updated token when deploying your gateway. The deployment configuration will automatically include the
--set hub.offline=trueflag:
- Helm Values
hub:
token: "<your-updated-token>"
offline: true
apimanagement:
enabled: true
- Gateway Status Confirmation: Once deployed, your gateway will appear in the dashboard with an "Offline gateway" status, confirming that it's operating without connectivity to the online dashboard while providing API management capabilities.
Authentication Configuration
In offline mode, API Management uses Custom Resource Definitions (CRDs) to configure authentication instead of relying on the online dashboard settings.
Two resources are available to configure authentication:
APIAuth Resource
The APIAuth CRD configures authentication for your APIs, replacing the gateway authentication settings that were previously configured at the workspace level.
- API Key Authentication
- JWT Authentication
apiVersion: hub.traefik.io/v1alpha1
kind: APIAuth
metadata:
name: default-auth
namespace: default
spec:
isDefault: true
apiKey: {}
apiVersion: hub.traefik.io/v1alpha1
kind: APIAuth
metadata:
name: jwt-auth
namespace: default
spec:
isDefault: true
jwt:
jwksUrl: https://your-auth-provider.com/.well-known/jwks.json
appIdClaim: azp
For comprehensive configuration options and examples, see the APIAuth documentation.
APIPortalAuth Resource
The APIPortalAuth CRD configures authentication for your API Portal, replacing the portal authentication settings configured in the online dashboard.
- APIPortalAuth
- OIDC Secret
apiVersion: hub.traefik.io/v1alpha1
kind: APIPortalAuth
metadata:
name: portal-auth
namespace: default
spec:
oidc:
issuerUrl: https://your-auth-provider.com/
secretName: portal-auth-secret
claims:
groups: groups
apiVersion: v1
kind: Secret
metadata:
name: portal-auth-secret
namespace: default
type: Opaque
data:
clientId: <base64-encoded-client-id>
clientSecret: <base64-encoded-client-secret>
For comprehensive configuration options and examples, see the APIPortalAuth documentation.
The attributes synchronization feature of the APIPortalAuth resource is not supported in offline mode.
Namespace Scope and Authentication
APIAuth Namespace Behavior
The APIAuth resource is namespace-scoped and affects all APIs within the same namespace:
- One APIAuth per namespace: Each namespace should have one APIAuth resource with
isDefault: true - Automatic application: All APIs in the namespace automatically use the authentication configuration
- Alphabetical precedence: If multiple APIAuth resources exist with
isDefault: true, the first one alphabetically is selected
APIPortalAuth Reference & Namespace Behavior
- The
APIPortalAuthresource must be explicitly referenced in your APIPortal resource:
apiVersion: hub.traefik.io/v1alpha1
kind: APIPortal
metadata:
name: my-portal
namespace: default
spec:
title: My API Portal
auth:
name: my-portal-auth # References APIPortalAuth resource
- Namespace-scoped: The
APIPortalAuthresource must be in the same namespace as theAPIPortalresource
Complete Configuration Examples
Here's a complete example demonstrating API Management in offline mode:
- API Configuration
- Portal Configuration
- API Management Resources
apiVersion: hub.traefik.io/v1alpha1
kind: APIAuth
metadata:
name: default-auth
namespace: apps
spec:
isDefault: true
apiKey: {}
---
apiVersion: hub.traefik.io/v1alpha1
kind: API
metadata:
name: weather-api
namespace: apps
spec:
openApiSpec:
path: /spec.json
override:
servers:
- url: "https://weather.example.com"
---
apiVersion: traefik.io/v1alpha1
kind: IngressRoute
metadata:
name: weather-ingress
namespace: apps
annotations:
hub.traefik.io/api: weather-api@apps
spec:
entryPoints:
- web
routes:
- match: Host(`weather.example.com`)
kind: Rule
services:
- name: weather-app
port: 8080
apiVersion: hub.traefik.io/v1alpha1
kind: APIPortalAuth
metadata:
name: portal-auth
namespace: apps
spec:
oidc:
issuerUrl: https://auth.example.com/
secretName: portal-auth-secret
claims:
groups: groups
---
apiVersion: hub.traefik.io/v1alpha1
kind: APIPortal
metadata:
name: api-portal
namespace: apps
spec:
title: Company API Portal
description: "Documentation for our APIs"
trustedUrls:
- https://portal.example.com
auth:
name: portal-auth
---
apiVersion: v1
kind: Secret
metadata:
name: portal-auth-secret
namespace: apps
type: Opaque
data:
clientId: <base64-encoded-client-id>
clientSecret: <base64-encoded-client-secret>
---
apiVersion: traefik.io/v1alpha1
kind: IngressRoute
metadata:
name: weather-portal
namespace: apps
annotations:
hub.traefik.io/api-portal: api-portal@apps
spec:
entryPoints:
- web
routes:
- match: Host(`portal.example.com`)
kind: Rule
services:
- name: apiportal
namespace: traefik
port: 9903
apiVersion: hub.traefik.io/v1alpha1
kind: APIPlan
metadata:
name: standard-plan
namespace: apps
spec:
title: Standard Plan
description: Standard access to APIs
rateLimit:
requests: 100
period: 1s
quota:
limit: 1000
period: 1h
---
apiVersion: hub.traefik.io/v1alpha1
kind: APICatalogItem
metadata:
name: standard-plan
namespace: apps
spec:
everyone: true
apis:
- name: weather-api
apiPlan:
name: standard-plan
---
apiVersion: hub.traefik.io/v1alpha1
kind: ManagedApplication
metadata:
name: partner-app
namespace: apps
spec:
appId: partner-app-id
owner: "67f67907ee260b44336a952e"
apiKeys:
- secretName: partner-app-key
---
apiVersion: v1
kind: Secret
metadata:
name: partner-app-key
type: Opaque
data:
# echo -n "secret-api-key" | openssl dgst -SHAKE256 -xoflen 64 | awk '{ print $2; }' | tr -d "\n" | base64 -w0
key: NzJiZjE2ZGRlY2I3YTNlYzA0YjVjZTAyOTZmODVhMGFiOWQwNDkxMDUyNDNiNGI3OTI0YTM0MGYyNjUyM2U3ZDc0M2UyNDEyNmNlZDkzZTlkZGU2M2QxYjRmNzNjMjQyYzVmMGVkOTdjY2UzOTRhNWFlZTNlY2RiMzg2NmQ4NGY=
---
apiVersion: hub.traefik.io/v1alpha1
kind: ManagedSubscription
metadata:
name: partner-subscription
namespace: apps
spec:
managedApplications:
- name: partner-app
apis:
- name: weather-api
apiPlan:
name: standard-plan
Offline Mode Capabilities
When operating in offline mode, certain self-service capabilities are currently not available:
API Portal Limitations
- No Self-Service Applications: Users cannot create, modify, or delete applications through the portal
- No Self-Service Subscriptions: Users cannot subscribe to APIs or manage existing subscriptions
- No API Key Management: Users cannot generate, rotate, or revoke API keys through the portal
Management Capabilities
- Managed Applications: Continue to work through CRDs and kubectl commands
- Managed Subscriptions: Can be configured and updated through Kubernetes resources
- API Catalog: Fully functional for browsing and documentation
- Authentication: Works normally through the configured authentication providers
Validation
Use the Traefik Hub static analyzer to validate your offline configuration:
hub-static-analyzer lint --path [path/to/manifests] --offline
The --offline flag enables additional validation checks for environments that don't have external connectivity to the Traefik Hub Online Dashboard .
Migration from Online to Offline
When migrating from online API Management to offline mode:
- Export existing auth configuration: Note your current authentication settings from the online dashboard
- Create CRD equivalents: Convert your online authentication configuration to APIAuth and APIPortalAuth resources
- Test configuration: Use the static analyzer to validate your offline configuration
- Deploy with offline flag: Update your deployment to include
hub.offline: true
Troubleshooting
Common Issues
-
APIs not protected: Ensure you have an APIAuth resource with
isDefault: truein the same namespace as your APIs. -
Portal authentication fails: Verify that your
APIPortalAuthresource is correctly referenced in yourAPIPortalspecification. -
No authentication configured: Check the gateway logs for messages about ignored APIs or portals due to missing authentication configuration.
Log Messages
In offline mode, you may see these informational messages:
API portal will be ignored: no authentication configuration found
API "example-api" will be ignored: no authentication configuration found
These messages indicate that authentication configuration is required for offline operation.
Conclusion
API Management Offline Mode provides a complete API management solution for environments with restricted connectivity.
The combination of APIAuth and APIPortalAuth resources enables full authentication configuration while maintaining the security and functionality of your API ecosystem.
Related Content
- Learn more about the APIAuth CRD in its dedicated section.
- Learn more about the APIPortalAuth CRD in its dedicated section.
- Learn more about API Gateway Offline Mode for general offline setup.
