Okta JWT Configuration
How to configure Okta for JWT.
If you switch from the default configuration to JSON Web Tokens, all API keys generated in the API Portal will be turned off.
This walk-through covers a basic example configuration of Okta using the minimal needed settings, please don't use it in production!
Requirements
Please ensure you have the following:
- An Okta instance with admin permissions.
- Admin permissions for the Traefik Hub workspace.
curl
Create an Authorization Server
As the first step, create a custom authorization server in Okta.
Browse to Security → API and select Add Authorization Server.
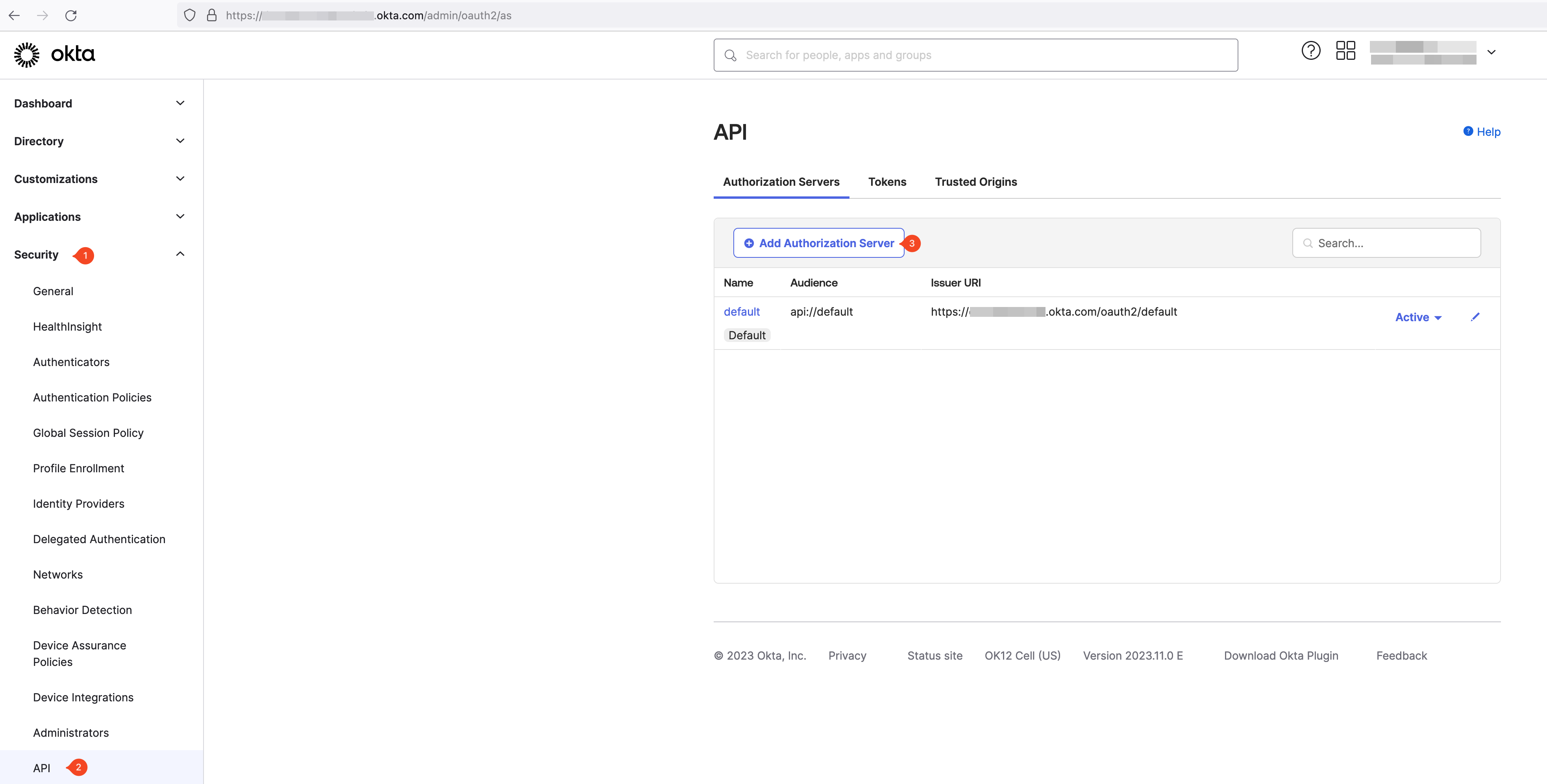
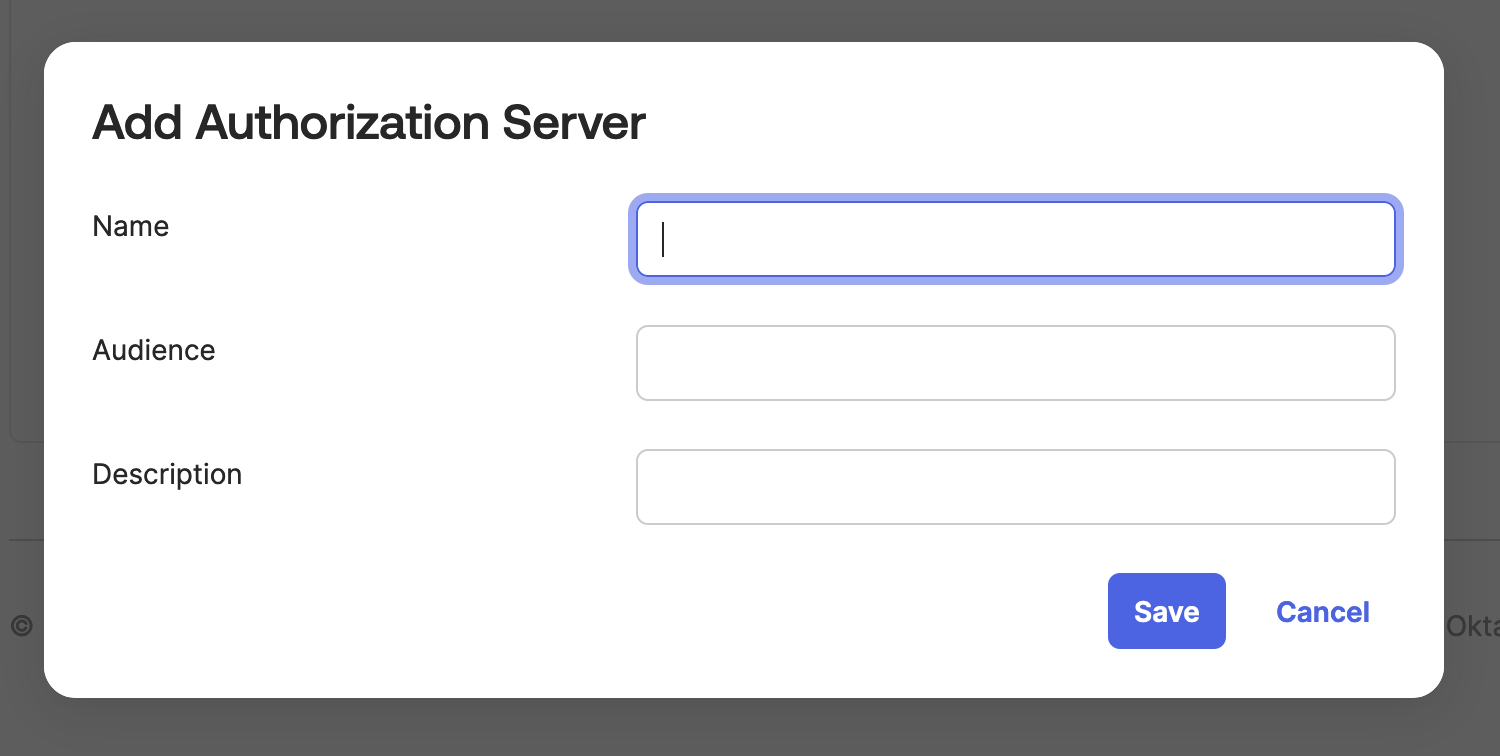
Enter the Name, Audience1, and Description for the authorization server.
Add an Access Policy
Now it is time to add an access policy to the new authorization server.
In the overview of the new authorization server, select Access Policies followed by Add New Access Policy.
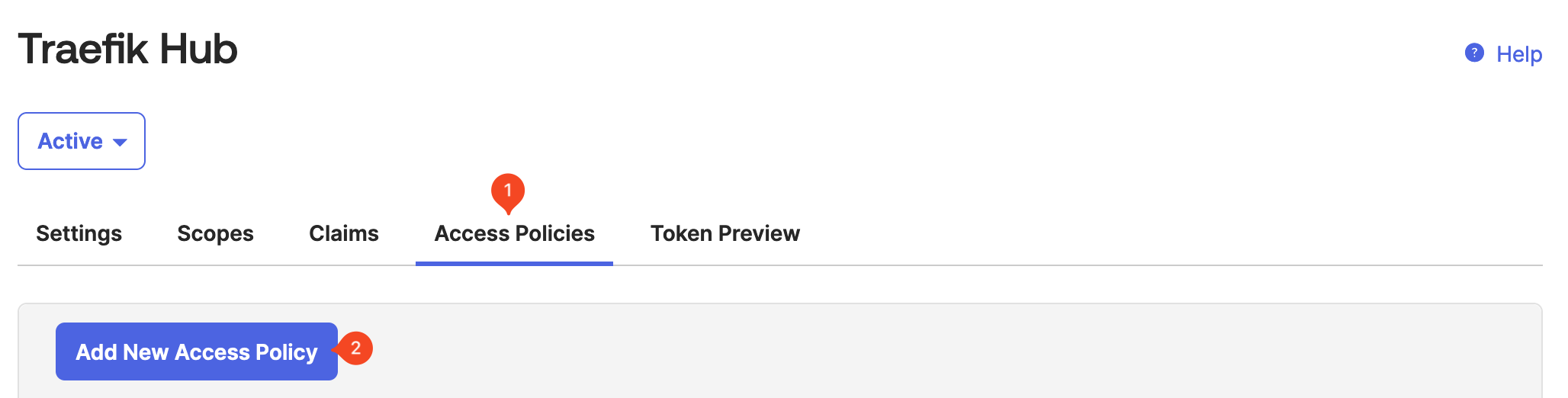
Enter the Name, the Description and assign a client. In this example, the policy is assigned to all clients.
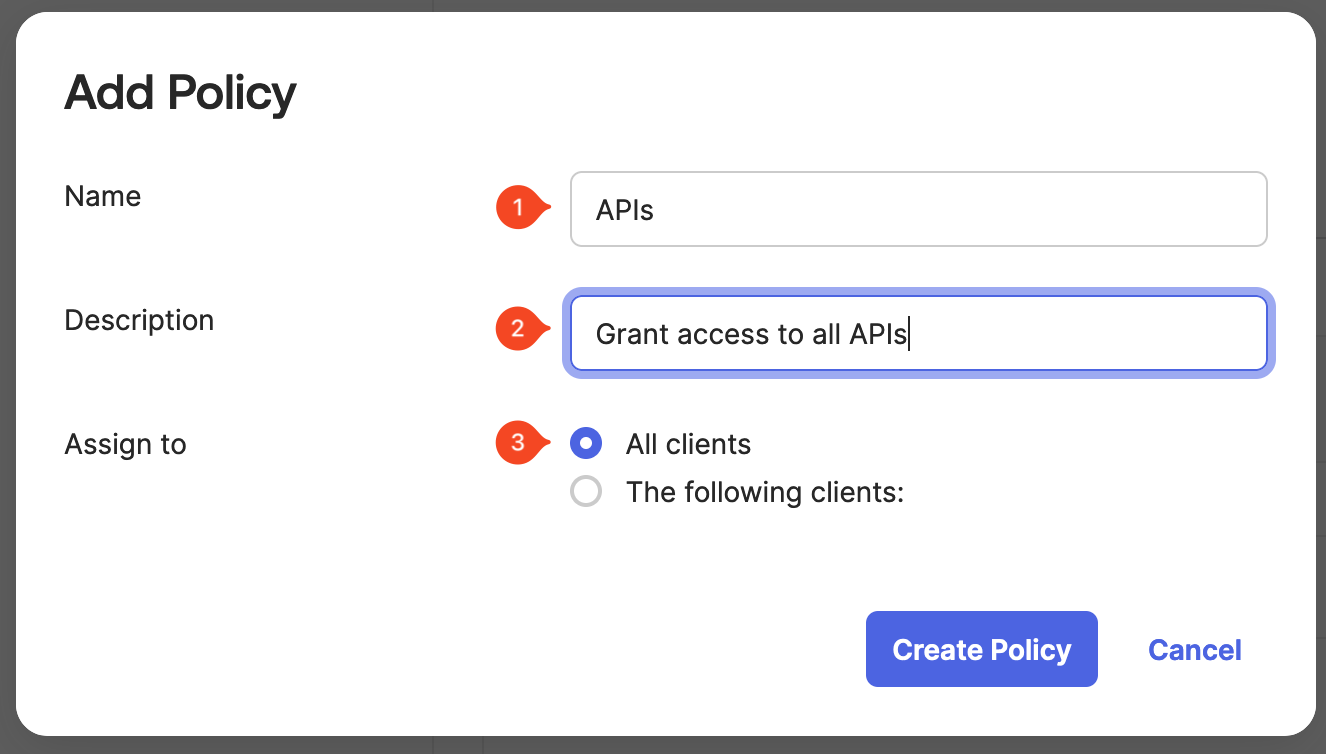
Once you're done, select Create Policy.
Add an Access Policy Rule
After the new policy is created, it is time to add a new rule to the policy. In a rule, you define the access permissions.
Select Add rule in the access policy overview.
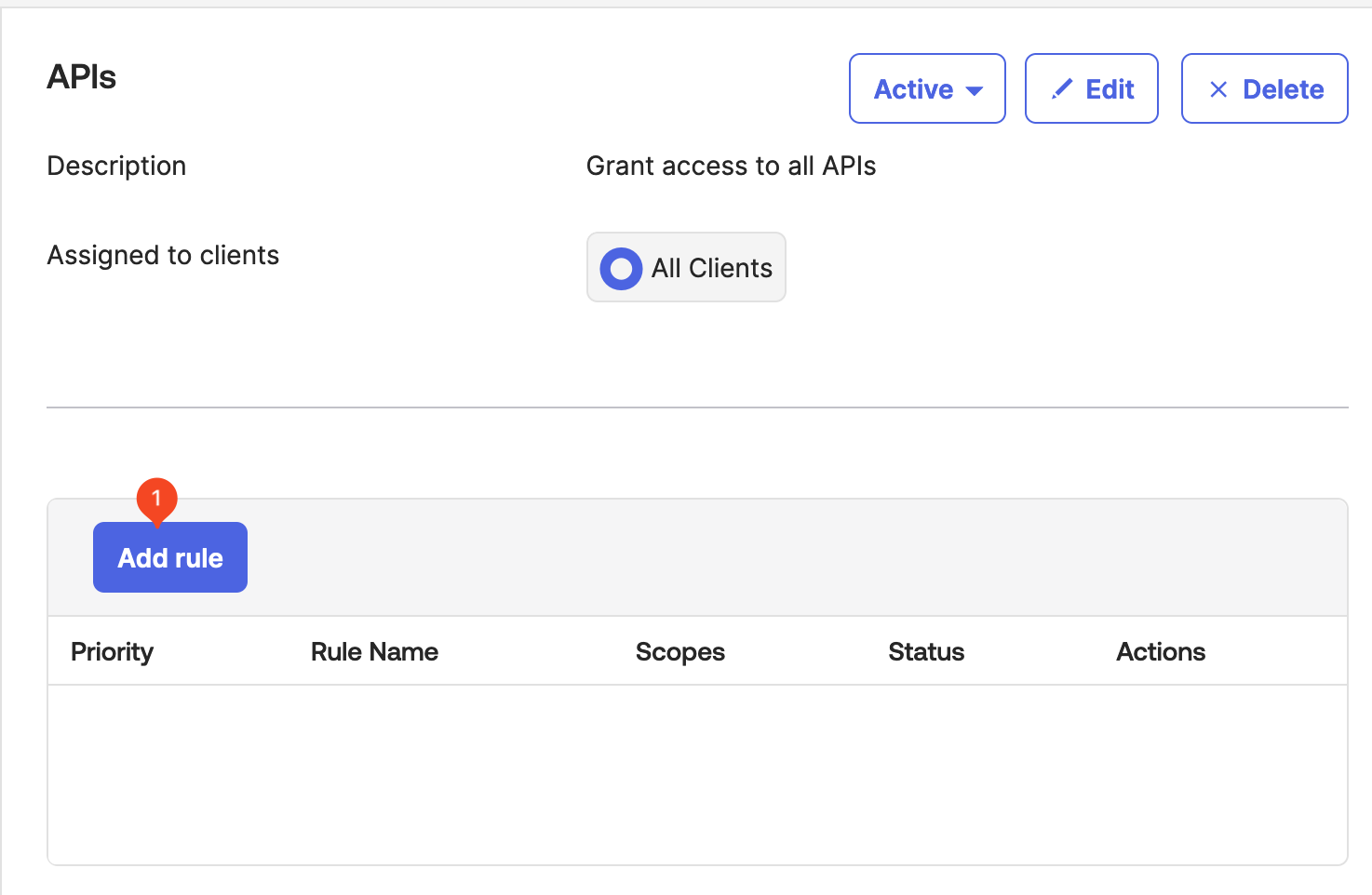
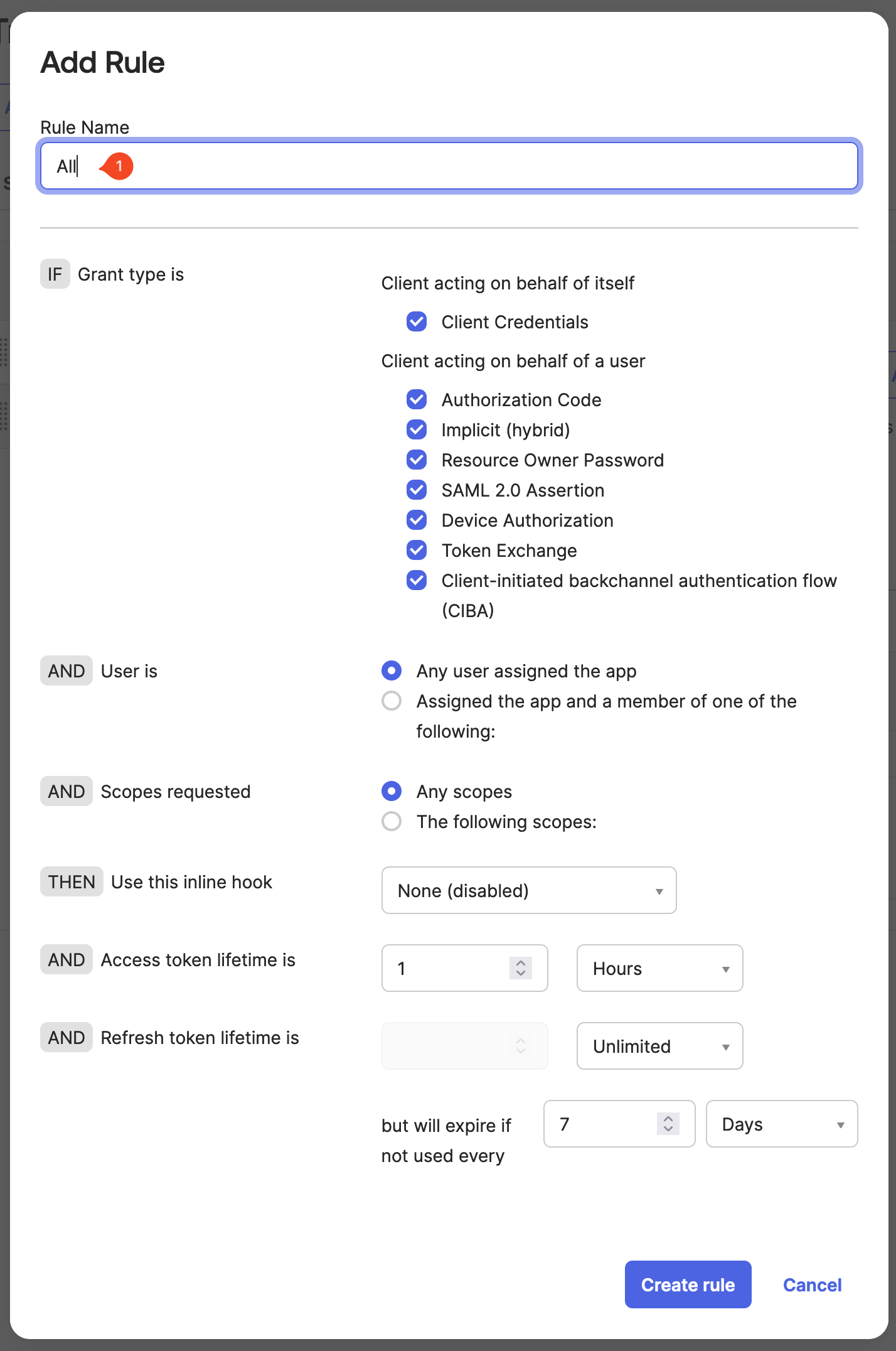
Enter a Rule Name and select Create rule.
This example uses the default rule configuration. You may want to adjust that for your production environment.
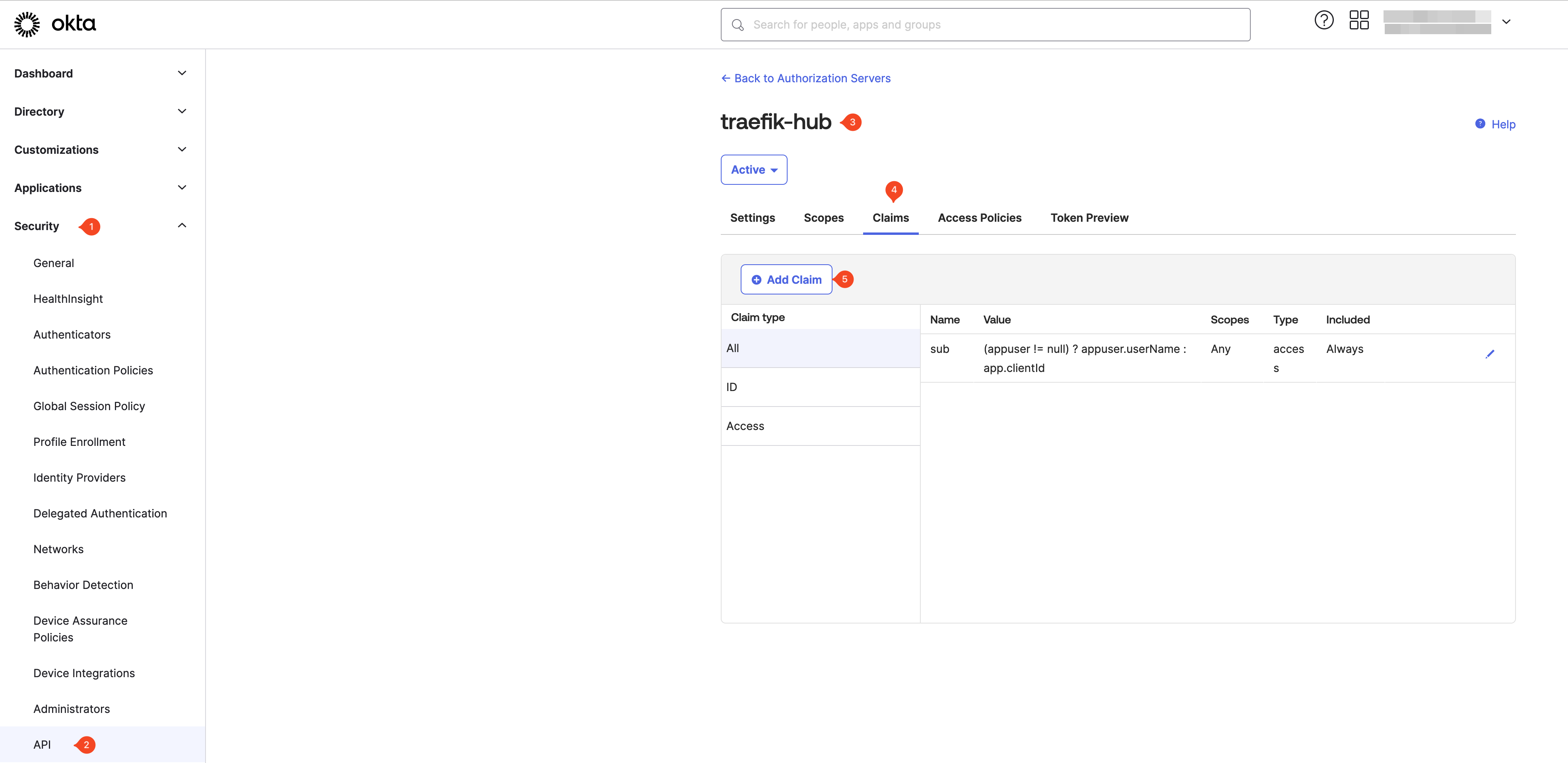
Claims
As the last part of the custom authorization server configuration, you will add a custom claim for groups. In Traefik Hub, every user must be a member of a user group. These groups are used to configure API access and rate limiting.
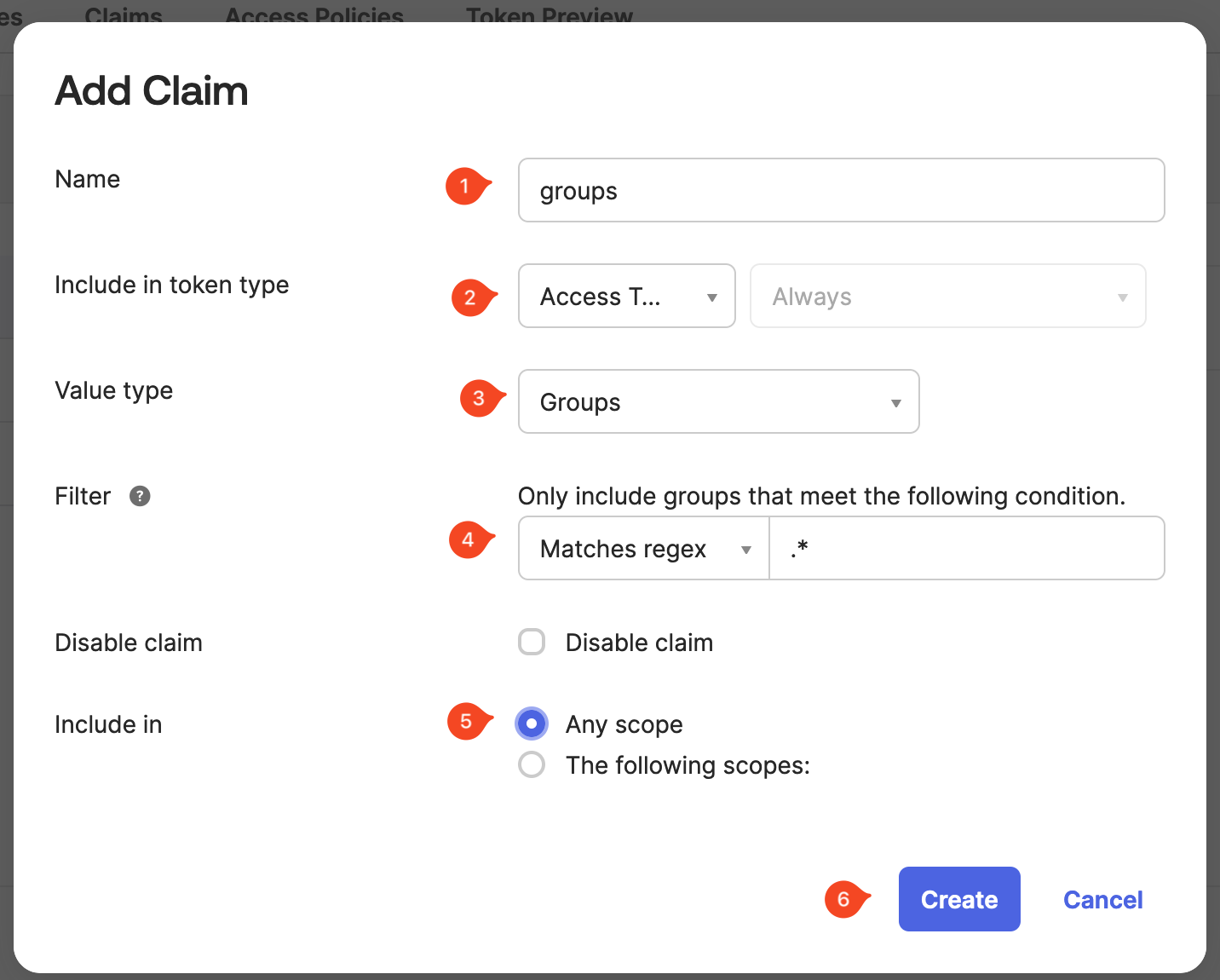
Browse to Security → API choose the new authorization server, select Claims, choose Add Claim and provide the requested information.
| Field | Description | Example |
|---|---|---|
| Name | Name of the claim needed by Traefik Hub. | groups |
| Include in token type | Select Access Token for(OAuth 2.0/2.1). For ID tokens, in the second dropdown, choose Always. | Access Token and Always |
| Value type | Choose whether the values defined in the claim use a Group filter or an Expression written using the Okta Expression Language. | .* |
| Disable claim | Check this option to temporarily disable the claim for testing or debugging. | Empty |
| Include in | Specify whether the claim is valid for any scope, or select the scopes for which it’s valid. | Any Scope |
Create an Application Integration
After you created and configured the custom authorization server, it's now time to create an Okta application.
In the Okta admin panel, go to → Applications -→ Applications and select Create App Integration.
Select the following settings:
- Sign-in method: OIDC
- Application type: Native Application
and Select Next.
![Create integration configuration] Create integration configuration](/traefik-hub/assets/images/okta-new-application-6c25eaec85d8cfdb5e35c34420a31c88.png)
In the following step, you will configure the new app integration.
Select the following settings:
- Grant type: Resource Owner Password
- Assignments (Controlled access): Allow everyone in your organization to access
and select Save.
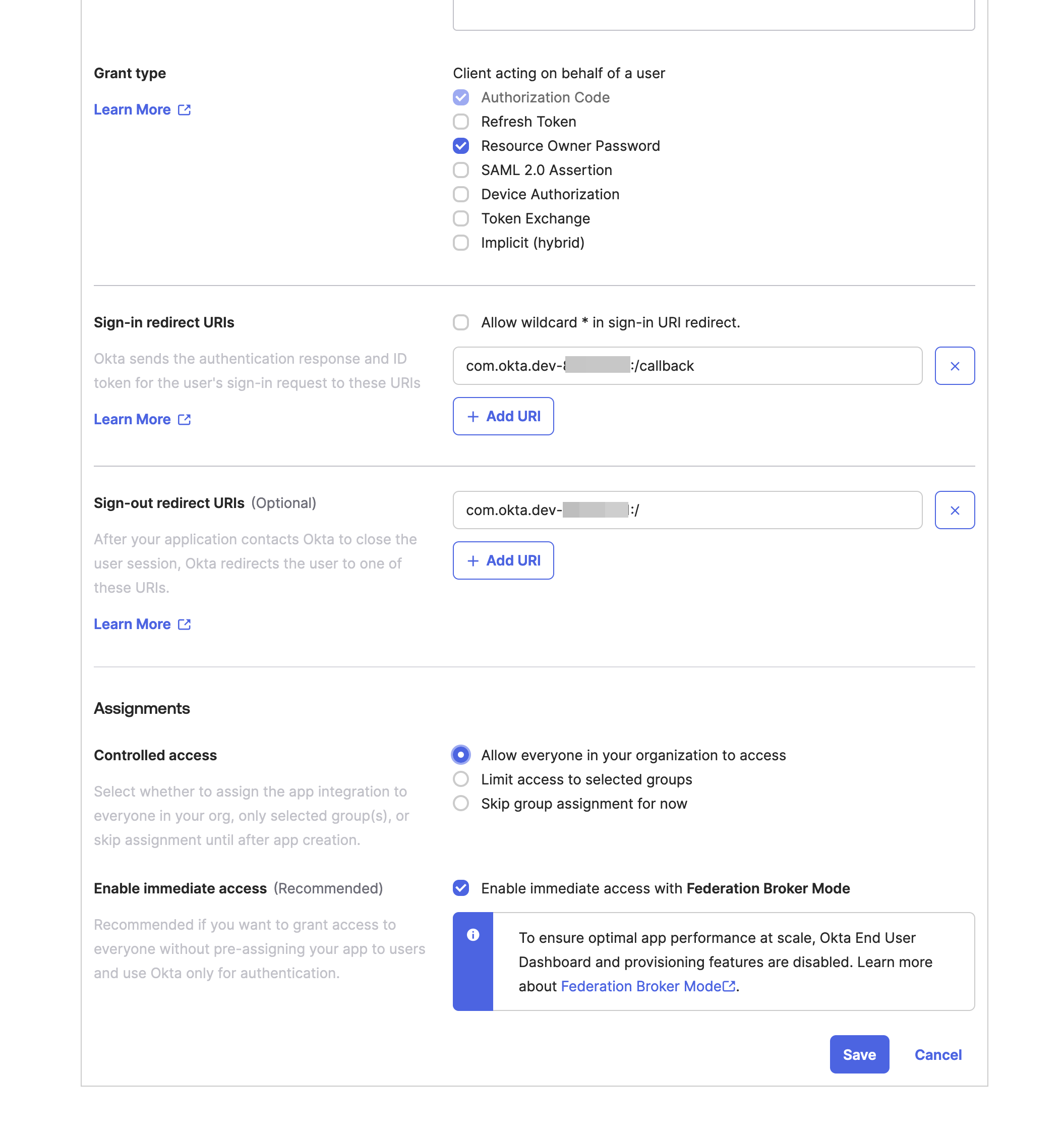
Congratulations, OKta is now ready to issue JWTs.
Test the Configuration
Use curl to generate a JWT and validate it against your Okta instance.
Please refer to the Okta OpenID Connect & OAuth documentation to learn more about the Okta authorization settings used below.
The following example uses the password grant type as a validation method.
curl -L -s -X POST 'https://$your-okta-org/oauth2/${authorizationServerId}/v1/token' \
-H 'Content-Type: application/x-www-form-urlencoded' \
--data-urlencode '[email protected]' \
--data-urlencode 'password=$your-secure-password' \
--data-urlencode 'grant_type=password' \
--data-urlencode 'scope=openid' \
--data-urlencode 'client_id=$your-client-id'
{"token_type":"Bearer","expires_in":3600,"access_token":"eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ2ZXIiOjEsImp0aSI6IkFULkZxUXZ4dzN1TmY5WWVLUXNadkluMWxROE9oUWNMM2ZwV2p4eEh6WFFXRVIiLCJpc3MiOiJodHRwczovL2Rldi1leGFtcGxlLm9rdGEuY29tL29hdXRoMi9hdXNkOHNsbmRpYVNnMXY0MTIzNCIsImF1ZCI6ImFwaTovL2h1YiIsImlhdCI6MTcwMDcyNzExOCwiZXhwIjoxNzAwNzMwNzE4LCJjaWQiOiIwb2FkOWZrbW81NjRUM2pSMzVlNiIsInVpZCI6IjAwdWRnZTJmcjBPcThJTXFLNWU2Iiwic2NwIjpbIm9wZW5pZCJdLCJhdXRoX3RpbWUiOjE3MDA3MjcxMjEsInN1YiI6ImphbmUuZG9lQHRyYWVmaWstYWlybGluZXMuaW8iLCJncm91cHMiOlsiRXZlcnlvbmUiXX0.8LHqpNnh-JxX-mb7YyTLPhnxYtSxSjQIWXIxmcsG6qA"}
Related Content
- Learn how to enable JWT authentication in the dashboard.
Footnotes
-
The recipients that the tokens are intended for. This becomes the audience claim in an access token. Currently, Okta supports only one audience. See the official Okta documentation. ↩
