What's new in Traefik Hub?
January 2026
What's New
New Middleware: Responses API (AI Gateway)
The Responses API middleware enables support for OpenAI's Responses API, the successor to the Chat Completions API. This middleware automatically promotes routes to OpenAI-compatible endpoints while providing the same governance, security, and observability capabilities available for Chat Completions.
Key features include:
- Seamless promotion of routes to OpenAI Responses API endpoints with automatic formatting
- Model governance with configurable default models and override controls
- Generation parameter management including
max_output_tokens,temperature,reasoning_effort, and more - Tool control with allow/block lists for function calling governance
- Full OpenTelemetry integration with GenAI semantic conventions for comprehensive observability
- Complete compatibility with existing AI Gateway middlewares including Content Guard, LLM Guard, and Semantic Cache
All Traefik Hub AI Gateway middlewares can be adapted to work with Responses API by configuring them to inspect the appropriate fields.
For complete configuration details and middleware adaptation patterns, see the Responses API middleware documentation and the Adapting Middlewares guide.
Enhanced OIDC Middleware Issuer Validation
The OIDC middleware now includes the trustedIssuer option, allowing you to explicitly define the issuer value to validate in JWT tokens independent of the discovery URL. This addresses scenarios where the issuer URL used for discovery differs from the issuer in tokens, such as when using internal discovery URLs while tokens contain external issuers.
The disableIssuerCheck option now only disables JWT token issuer validation (not discovery mismatch handling), providing more granular control. This ensures production environments can maintain proper issuer validation even when discovery endpoints report different issuer URLs than what appears in tokens.
For configuration details and examples, see the OIDC middleware documentation.
Multiple Trusted Issuers for APIAuth (API Management)
The APIAuth resource in Traefik Hub API Management now supports validating JWTs from multiple identity providers using jwt.trustedIssuers. This is useful for multi-tenant setups where each tenant uses a different issuer.
See the APIAuth documentation for configuration details and examples.
Compatibility Matrix
This release comes with the following components:
| Component | Version |
|---|---|
| Traefik Hub | v3.19.0 |
| Helm Chart | v39.0.0 |
| Traefik Proxy | v3.6.7 |
| Coraza WAF | v3.3.3 |
| OWASP CRS | v4.14.0 |
| Static Analyzer | v1.6.0 |
| Kubernetes Gateway API | v1.4.0 |
Bug Fixes Timeline
- 2026-01-21: Traefik Hub v3.19.0 was released with the following security fixes:
- Fixed CVE-2025-66490 - Path normalization bypass vulnerability (CVSS 6.5). New
encodedCharactersoptions are available to enhance security. - Fixed CVE-2025-66491 - Logic inversion in
nginx.ingress.kubernetes.io/proxy-ssl-verifyannotation (CVSS 5.9). - Fixed CVE-2026-22045 (GHSA-cwjm-3f7h-9hwq) - ACME TLS-ALPN challenge vulnerability allowing resource exhaustion (CVSS 5.9).
- Fixed CVE-2025-66490 - Path normalization bypass vulnerability (CVSS 6.5). New
November 2025
What's New
Traefik Hub v3.19 with Traefik Proxy v3.6 (Early Access)
These features are currently in early access. See the compatibility matrix below for more information.
Traefik Hub v3.19 ships with Traefik Proxy v3.6, introducing powerful new routing capabilities and serverless integration:
-
Multi-Layer Routing: Advanced HTTP routing that enables sophisticated traffic management through prioritized route evaluation. Routes are now evaluated in sequence according to explicit priorities, allowing you to create complex routing strategies, such as API versioning, gradual rollouts, and conditional routing based on headers, paths, or query parameters (among others). This feature provides fine-grained control over request flow, enabling patterns such as blue-green deployments and sophisticated A/B testing. See the Multi-Layer Routing documentation for configuration details.
-
Knative Provider: Native integration with Knative Serving enables Traefik Hub to act as the networking layer for serverless workloads. This provider brings together Traefik's advanced routing capabilities with Knative's scale-to-zero architecture, supporting tag-based routing for A/B testing, percentage-based traffic splitting for canary deployments, and automatic service discovery. Traefik Hub becomes the only proxy that can seamlessly operate across cloud-native containers, traditional VMs, and serverless workloads in a unified deployment. See the Knative provider installation and routing configuration documentation.
-
Gateway API v1.4.0: Updated support for the latest Kubernetes Gateway API specification, bringing enhanced routing capabilities and improved conformance with the Gateway API standard.
LDAP Authentication for API Management
Traefik Hub API Management now supports LDAP (Lightweight Directory Access Protocol) authentication for both API Portal and API access. Organizations can leverage their existing LDAP infrastructure, including OpenLDAP, Active Directory, and Oracle Internet Directory, to authenticate users and applications without requiring additional identity providers.
LDAP Portal Authentication enables portal users to authenticate with their LDAP credentials through an interactive login form. User attributes (email, name) and group memberships are automatically synchronized from LDAP in online mode, providing seamless integration with existing directory services. Portal access can be controlled using LDAP group membership, making it easy to grant developers access based on their organizational roles.
LDAP API Authentication validates API requests using HTTP Basic Authentication with LDAP credentials. Each request is authenticated against the LDAP server, with the LDAP username matching the appId in a ManagedApplication resource. This stateless authentication method works with both ManagedSubscriptions for access control and APIPlans for rate limiting, providing the same governance capabilities as API Key and JWT authentication.
Key features include:
- Dual authentication modes: Portal authentication with interactive login forms and API authentication with per-request Basic Auth
- Multiple LDAP providers: Supports OpenLDAP, Active Directory, and Oracle Internet Directory
- Group-based access control: LDAP groups (via
memberOfattribute) control portal visibility and API access - Flexible deployment: Works in both online mode (with attribute sync) and offline mode (authentication only)
- Security options: LDAPS, StartTLS, and custom CA certificate support
- Configurable bucket strategies: Rate limits and quotas can be scoped per subscription, per application, or per application-API pair using the new
bucketfield inAPIPlan - UI and CRD configuration: Configure LDAP through the Traefik Hub Dashboard or using
APIPortalAuthandAPIAuthCRDs
For complete configuration details, see the LDAP Authentication , APIPlan, APIPortalAuth, and APIAuth documentation.
Artifactory Support for Private Plugins (Early-Access)
Traefik Hub API Gateway now supports loading plugins from Artifactory repositories configured as VCS mirrors (GitHub, Bitbucket, etc.). This feature enables organizations to use proprietary or internal plugins while maintaining security through token-based authentication and hash verification.
For more details, see the Private Plugins documentation and plugin development guide.
Multi-Issuer JWT Support
The JWT middleware now supports multiple trusted issuers through the new trustedIssuers option. This enables applications to accept JWTs from multiple identity providers simultaneously, with each issuer configured with its own JWKS endpoint and optional issuer validation. The feature supports both strict issuer matching and fallback scenarios for flexible multi-provider authentication. See the JWT middleware documentation for configuration details.
Compatibility Matrix
This release comes with the following components:
| Component | Version |
|---|---|
| Traefik Hub | v3.19.0-ea.9 |
| Helm Chart | v37.4.0 |
| Traefik Proxy | v3.6.2 |
| Coraza WAF | v3.3.3 |
| OWASP CRS | v4.14.0 |
| Static Analyzer | v1.5.0 |
| Kubernetes Gateway API | v1.4.0 |
October 2025
What's New
Private Plugins Support
Traefik Hub API Gateway now supports loading plugins from private GitHub and GitLab repositories. This feature enables organizations to use proprietary or internal plugins while maintaining security through token-based authentication and hash verification.
Key capabilities include:
- Private GitHub repositories: Support for GitHub.com, GitHub Enterprise Cloud, and GitHub Enterprise Server
- Private GitLab repositories: Support for GitLab.com and self-hosted GitLab instances
- Secure authentication: Token-based access using personal access tokens or project tokens
- Hash verification: SHA-256 hash verification ensures plugin integrity and prevents tampering
- Kubernetes secret integration: Secure token storage using URN secret references
- Multiple registry sources: Configure multiple plugin sources from different Git providers
This feature is particularly valuable for enterprises that need to distribute internal plugins, maintain proprietary middleware, or ensure plugin security through controlled access and verification.
For more details, see the Private Plugins documentation.
MCP Gateway with Task-Based Access Control (Early-Access)
Traefik Hub now includes MCP Gateway, a dedicated gateway for securing and governing Model Context Protocol (MCP) servers. The MCP Gateway acts as an OAuth-compliant proxy that enables organizations to centrally manage access to MCP servers, tools, and resources with Task-Based Access Control (TBAC)—a new authorization paradigm designed specifically for AI agents.
Why TBAC? Traditional Role-Based Access Control (RBAC) fails for AI agents because agents don't have static job functions—they complete tasks that span multiple domains. TBAC provides authorization across three dimensions: Tasks (business objectives), Tools (system access), and Transactions (parameter-level constraints), ensuring agents get precisely the permissions they need for their current work, nothing more.
Variable Substitution. Traefik's ${jwt.claim} and ${mcp.parameter} syntax enables writing a single adaptive policy that works for unlimited agents, with permissions determined by JWT claims. Instead of managing thousands of agent-specific policy lines, you write a handful of policies that dynamically enforce authorization based on each agent's claims—making TBAC practical at enterprise scale.
The MCP Gateway includes:
- Task-Based Access Control (TBAC) with three-dimensional authorization (tasks, tools, transactions) using variable substitution for scalable, adaptive policies
- MCP middleware with expression language supporting string matching (Equals, Contains, Prefix) and numeric comparisons (Lt, Gt, Lte, Gte) for transaction-level limits like approval amounts and rate quotas
- OAuth 2.1/2.0 Resource Server compliance with automatic
/.well-known/oauth-protected-resourceendpoint generation for MCP client discovery - JWT authentication for seamless integration with existing identity providers (Auth0, Okta, Azure AD, etc.)
- Zero infrastructure overhead by leveraging existing identity providers—no new databases, policy engines, or specialized infrastructure required
- Sub-millisecond authorization through stateless JWT validation with no external API calls or database queries
- Comprehensive audit trails capturing the complete three-dimensional authorization context for compliance (SOX, HIPAA, GDPR, PCI DSS)
- OpenTelemetry observability with metrics and traces for all MCP operations
The MCP Gateway is essential for organizations deploying AI agents that need controlled access to external tools and data sources. Unlike traditional approaches that rely on role inheritance or impersonation, TBAC ensures AI systems get precisely scoped permissions based on the work they're performing.
To enable MCP Gateway, use:
--set hub.mcpgateway.enabled=true
For more details, see the MCP Gateway documentation, Understanding TBAC guide, and getting started guide.
Traefik Hub v3.18 with Traefik Proxy v3.5
Traefik Hub v3.18 now ships with Traefik Proxy v3.5, bringing several new features and improvements like:
-
Kubernetes Ingress NGINX Provider: Native support for NGINX-specific Ingress annotations, enabling seamless migration from NGINX Ingress Controller to Traefik Hub while preserving existing configurations. See the Kubernetes Ingress NGINX provider documentation and routing configuration guide.
-
OCSP Stapling: Online Certificate Status Protocol (OCSP) stapling support improves TLS handshake performance and enhances client privacy by providing certificate revocation status directly during the TLS handshake. Learn more in the OCSP Stapling documentation.
-
Configuration Terminology Update: To better reflect the purpose of each configuration type, we've renamed "Static Configuration" to "Install Configuration" and "Dynamic Configuration" to "Routing Configuration" throughout the documentation. This change provides clearer guidance on where different settings should be configured.
-
ACME Provider HTTP Timeout: The ACME provider now supports HTTP timeout with the
clientTimeoutandclientResponseHeaderTimeoutoptions, allowing you to configure the timeout for HTTP requests and response headers to the ACME server. See the ACME provider documentation for more details.
Compatibility Matrix
This release comes with the following components:
| Component | Version |
|---|---|
| Traefik Hub | v3.18.0 |
| Helm Chart | v37.2.0 |
| Traefik Proxy | v3.5.3 |
| Coraza WAF | v3.3.3 |
| OWASP CRS | v4.14.0 |
| Static Analyzer | v1.5.0 |
| Kubernetes Gateway API | v1.3.0 |
September 2025
What's New
New Middleware: LLM Guard (AI Gateway)
The LLM Guard middleware brings flexible content security to any API traffic through external guard services or LLMs. This middleware supports four variants to handle different integration patterns, from generic APIs with custom security services to chat completions with LLM-based guards like Llama Guard.
The non-chat-completion variants (llm-guard and llm-guard-custom) provide a unique advantage by applying AI-powered security analysis to any incoming API traffic, not just AI or chat APIs. The -custom suffix variants integrate with non-chat-compatible upstream guard services. While traditional solutions only secure predefined AI formats, Traefik Hub protects your entire API ecosystem including e-commerce product APIs, banking transactions, HR systems, and customer data endpoints. This enables AI-driven threat detection, content policy enforcement, and fraud analysis across all business APIs.
Key features include:
- Custom Go templates for request formatting
- Powerful JSON path expressions for blocking conditions
- Integration with safety models supporting categories like hate speech and violence detection
- Streaming response analysis for chat completions
- Full response body logging with the
logResponseBodyoption for debugging - Multi-layered security pipelines where multiple guards can analyze different aspects of interactions before they reach backend services
For complete configuration details and deployment patterns, see the LLM Guard middleware documentation.
August 2025
What's New
New Middleware: Force Case
The Force Case middleware enforces specific header casing for both incoming requests and outgoing responses. HTTP headers are typically case-insensitive according to RFC specifications, but some legacy systems or APIs require headers to maintain specific capitalization patterns.
This middleware ensures that designated headers preserve their exact case format instead of being normalized to canonical MIME header format. It's particularly useful for SOAP services that expect headers like SOAPAction with exact capitalization, legacy API integrations with strict header casing requirements, and compliance scenarios where specific header formatting must be preserved.
For more details, see the Force Case middleware documentation.
Compatibility Matrix
This release comes with the following components:
| Component | Version |
|---|---|
| Traefik Hub | v3.18.0-beta3 |
| Helm Chart | v37.0.0 |
| Traefik Proxy | v3.4.5 |
| Coraza WAF | v3.3.3 |
| OWASP CRS | v4.14.0 |
| Static Analyzer | v1.5.0 |
| Kubernetes Gateway API | v1.2.1 |
July 2025
What's New
API Management Offline Mode
Traefik Hub API Management now supports full offline operation, providing the same level of authentication and API management configuration as the Online Dashboard. This release introduces two new Custom Resource Definitions:
APIAuthfor namespace-level API authentication using API Key or JWTAPIPortalAuthfor configuring API Portal authentication with OpenID Connect (OIDC). The OIDC integration works with major identity providers such as Auth0, Azure AD, and Keycloak and includes flexible claim mapping and attribute synchronization.
Enhanced Static Analyzer for Offline Mode
The static analyzer now supports offline mode validation using the --offline flag. This update checks that every namespace with APIs has the required APIAuth resources and confirms that each APIPortal resource is linked to an APIPortalAuth configuration. The analyzer generates tables that show which authentication method is assigned to each API and application, and the diff tool now includes tables that clarify how changes to APIAuth or APIPortalAuth affect your APIs and applications. These improvements help you verify that your offline API management setup is complete and correctly organized before deployment.
For more details, see the API Management Offline Mode, APIAuth, and APIPortalAuth documentation.
New Middleware: Query
We are excited to announce the new Query middleware, which allows you to manipulate query parameters in HTTP requests before forwarding them to services.
This middleware provides a flexible way to modify query parameters in a request, including setting, appending, removing, and renaming them.
For more details, see the Query middleware documentation.
Compatibility Matrix
This release comes with the following components:
| Component | Version |
|---|---|
| Traefik Hub | v3.18.0-beta1 |
| Helm Chart | v37.0.0 |
| Traefik Proxy | v3.4.5 |
| Coraza WAF | v3.3.3 |
| OWASP CRS | v4.14.0 |
| Static Analyzer | v1.5.0 |
| Kubernetes Gateway API | v1.2.1 |
Bug Fixes Timeline
- 2025-06-23: Traefik Hub v3.17.3 and v3.16.6 were released with the following fix:
- Fixed CVE-2025-54386.
June 2025
What's New
AI Gateway General Availability
- AI Gateway graduates from experimental: enable all AI features with
--set hub.aigateway.enabled=true. - New chat-completion middleware replaces the experimental
AIService, adds GenAI metrics, and centralises governance ofmodeland generation parameters. - Model-based routing: use the
Model(`<pattern>`)matcher to steer traffic by JSONmodelfield. - Request-size guard:
hub.aigateway.maxRequestBodySizeprevents OOM/DoS from oversized bodies. - Semantic Cache gains a chat-specific variant, Weaviate vector DB support, and additional vectorizers (Azure OpenAI, Cohere, Gemini, Bedrock).
- Content Guard now offers a chat-aware variant with stream support.
For more details, see the AI Gateway documentation.
Managed Applications (API Management)
Traefik Hub API Management now lets platform teams fully automate application onboarding with the new ManagedApplication resource. Publishers can declaratively create applications, pre-provision API keys, and bind them to ManagedSubscription objects — all without any consumer interaction with the Developer Portal.
Key capabilities include:
- GitOps-friendly
ManagedApplicationresource that storesappId, JWT / API Keys, owner ID, optional notes, and zero-to-many API keys (secrets may be provided inline or by reference). - Publishers provision the
appId, and quotas up front; consumers can call the API straight away - Updated
ManagedSubscriptionresource with amanagedApplicationsselector for explicit targeting of managed apps. - API consumers authenticate immediately with JWT or API keys issued by the publisher; no portal login is required.
- The Hub dashboard lists both managed and self-service applications, with clear indicators and full key management.
- Static-Analyzer rule warns if multiple ManagedApplications share the same
appIdwithin a namespace.
See the Managed Applications documentation for more information.
Offline Mode
Traefik Hub now supports offline mode, which allows you to run the Traefik Hub API Gateway in a completely offline environment.
For more details, see the Offline Mode documentation.
Compatibility Matrix
This release comes with the following components:
| Component | Version |
|---|---|
| Traefik Hub | v3.17.0 |
| Helm Chart | v36.3.0 |
| Traefik Proxy | v3.4.1 |
| Coraza WAF | v3.3.3 |
| OWASP CRS | v4.7.0 |
| Static Analyzer | v1.4.0 |
| Kubernetes Gateway API | v1.2.1 |
Bug Fixes Timeline
- 2025-06-23: Traefik Hub v3.16.2 and v3.15.3 were released with the following fix:
- Fixed CVE-2025-47952.
April 2025
What's New
Multi-Tenant Installation on Kubernetes
Traefik Hub now supports deploying multiple, isolated gateway instances on a single Kubernetes cluster. By configuring specific namespaces for each instance, you can achieve resource isolation, simplify deployments aligned with team structures, and maintain consistent API management across different environments within the same cluster.
Learn more about this feature in the multi-tenancy documentation.
OpenAPI v3.1.x Support
Traefik Hub now supports OpenAPI v3.1.x, in addition to Swagger v2.0 and OpenAPI v3.0.x. Swagger v2 specifications are automatically converted to OpenAPI v3.1 upon processing, ensuring consistency across your API documentation within the Hub.
See the OpenAPI documentation for more details.
March 2025
What's New
New Middleware: Semantic Cache
We introduced a Semantic Cache middleware for the AI Gateway, allowing you to store and retrieve responses based on semantic similarity. If a similar request appears, the middleware returns the cached result immediately instead of calling the AI backend again. This feature helps reduce latency and saves on provider costs.
Learn more about this middleware in it's documentation page.
New Middleware: Content Guard
Content Guard is a middleware that protects sensitive data across both AI and API Gateway environments by blocking or masking content before it reaches any upstream service. It helps ensure that confidential data is safeguarded in all scenarios, whether processing AI-specific traffic or general API requests.
Learn more about this middleware in it's documentation page.
Reference Secrets as Credentials Storage in the AI Gateway
We now allow you to specify tokens in the AIService resource as securely stored credentials in a Kubernetes Secret instead of embedding them directly in YAML (previous token field).
This approach improved security and aligns with centralized governance over secret management.
For more details, see our updated AI Gateway documentation and the relevant example manifest changes.
Traefik Hub Integration Now Available on Nutanix NKP
Traefik Proxy is now the default ingress controller in Nutanix Kubernetes Platform (NKP). You can upgrade your NKP cluster to Traefik Hub API Gateway and API Management to unlock advanced enterprise features, including centralized API governance, enhanced security, and dynamic routing. For more details on the upgrade process and benefits, please read our blog post and refer to the Nutanix NKP Installation Guide.
API, APIVersion & APIBundle Resources: New title & description fields
API, APIVersion, and APIBundle resources now support dedicated title and description fields. For API and APIVersion resources, these fields override the values from the OpenAPI specification, allowing you to present tailored content in the API portal.
For APIBundle resources, you can now specify a custom title to display a more user-friendly name on the portal.
See the API, APIVersion & APIBundle documentation for more information.
Resource Ownership & Editability in the Dashboard
Traefik Hub now distinguishes between resources created through the Online Dashboard and those managed externally (via GitOps), to prevent accidental modifications and conflicting changes. The following changes have been made:
- Resources created via the dashboard remain fully editable, while those managed externally become read-only.
- Visual indicators have been added: read-only resources display a Kubernetes icon, whereas editable resources show a monitor-like icon.
For more details on how resource ownership is handled in the Dashboard now, please refer to the Online Dashboard documentation.
February 2025
What's New
New AI Providers: DeepSeek & QWen
Traefik Hub AI Gateway now supports two additional AI providers:
- DeepSeek
- QWen
Both AI providers use the OpenAI API structure with a different base URL and models.
Updated OpenAI Implementation
The OpenAI integration in Traefik Hub AI Gateway has been enhanced with support a custom baseUrl option for OpenAI-compatible AI services.
New Feature: API Mocking for Expanded API Development & Testing
Traefik Hub is evolving beyond API runtime management to support a comprehensive API Development and Testing use case. This enhancement empowers API developers and platform engineers to:
- Rapidly prototype and test API designs using live API mocks generated via Microcks.
- Refine gateway settings and security policies in a safe, sandboxed environment.
- Iterate quickly based on real-world testing feedback before full-scale production deployment.
For a detailed guide on setting up and leveraging these capabilities, please refer to our On-Premises API Mocking guide.
Including an API Plan is Mandatory in Managed Subscription
A Managed Subscription must always include an API Plan. Even unlimited plans must be explicitly defined, there are no more implicit unlimited plans to improve governance and avoid unwanted misconfiguration scenarios. For existing Traefik Hub Kubernetes deployments, upgrade your cluster to version 34.3.0 or later of the Traefik Helm chart and also upgrade your CRDs to the new version that introduces this change.
Please see upgrading instructions for more information.
Compatibility Matrix
This release comes with the following components:
| Component | Version |
|---|---|
| Traefik Hub | v3.14.1 |
| Helm Chart | v34.4.0 |
| Traefik Proxy | v3.3.4 |
| Coraza WAF | v3.3.2 |
| OWASP CRS | v4.7.0 |
| Static Analyzer | v1.4.0 |
| Kubernetes Gateway API | v1.2.1 |
Bug Fixes Timeline
-
2025-02-11: Traefik Hub v3.11.1 was released with the following fixes:
- Fixed empty API column in the subscription table on the API portal.
- Fixed AI gateway panic when using Gemini with OTel.
-
2025-02-18: Traefik Hub v3.13.0 was released with the following updates:
- Bump Go version from v1.23.0 to v1.23.6.
- Add CORS support for API & API version resources.
- New
baseUrloption for the OpenAI provider in the Traefik Hub AI Gateway. - New
titleoption for the API Bundle, similar to the API and API Version CRDs.
-
2025-02-26: Traefik Hub v3.14.1 was released with the following updates:
- Bump Traefik Proxy to v3.3.4
- New Windows FIPS 140-2 build with
microsoft/go - Add search functionality in the available APIs list on the Portal UI.
January 2025
What’s New
New Feature: Self-Service Subscriptions (API Management)
We are excited to introduce Self-Service Subscriptions, which empower API consumers to directly subscribe their applications to APIs—or entire API Bundle—through the API Portal.
Key Highlights:
- Instant Access: API consumers can subscribe immediately, reducing time-to-integration.
- Bundle Support: Subscribe to multiple APIs at once via a bundle subscription workflow.
- Coexistence with Managed Subscriptions: If a self-service subscription coexists with a managed subscription, the self-service plan takes precedence, but unsubscribing reactivates the managed one.
- Streamlined Portal Subscription Flow: A user-friendly interface in the API Portal lets consumers quickly select an application and confirm a plan, simplifying the overall onboarding process.
For more details, see Self-Service Subscriptions.
New Feature: Block Requests to Undocumented Paths and Methods (API Management)
We’ve introduced a validateRequestMethodAndPath option for both API and APIVersion resources, preventing “zombie” or “shadow” endpoints by blocking requests to paths and methods not defined in your OpenAPI specification.
This helps strengthen security and maintain a well documented API surface.
For more information about the validateRequestMethodAndPath feature, see the API & APIVersion documentation.
Bug Fixes
- We fixed the CVE-2024-53259 vulnerability in Traefik Hub v3.9.0.
December 2024
What’s New
New Feature: Secure, Govern, and Observe AI Endpoints Like APIs
We are excited to announce the new AI gateway feature which allows you to manage and integrate multiple Large Language Model (LLM) providers.
To get started, check out our AI Gateway documentation to learn how to enable & start using it.
New Feature: Managed Subscriptions (API Management)
Introducing managed subscriptions, a powerful way to manage subscriptions between applications and your APIs or API Bundles. With ManagedSubscription, you get the following benefits:
- Application-level control: With managed subscriptions, you can specify applications that will consume APIs via an application identifier (
appId). This allows you to manage API consumption at the application level rather than the user level. - Control access: Define which applications can access specific APIs or API Bundles.
- Enforce API plans: Apply API Plans to subscriptions to enforce rate limits, quotas, and other policies.
- Claims-based authorization: Use expressions to validate claims in authentication tokens (e.g., JWTs) for fine-grained access control.
For more details, refer to the Managed Subscriptions documentation.
New Feature: APICatalogItem (API Management)
We are excited to announce the addition of the APICatalogItem Custom Resource Definition (CRD) in Traefik Hub API Management.
APICatalogItem is a resource in Traefik Hub that defines which APIs are visible to users in the Developer Portal. It allows API managers to control the visibility of APIs and API Bundles to specific user groups, ensuring that API consumers only see the APIs they are authorized to access.
Key Features of APICatalogItem:
- Specify which APIs or API Bundles are displayed to specific user groups.
- Control the visibility of specific operations within APIs.
For more details, refer to the APICatalogItem documentation.
For existing Traefik Hub Kubernetes deployments, you need to upgrade your cluster to use at least v33.1.0 of the Traefik Helm chart that introduces the AIService, ManagedSubscription & APICatalogItem CRDs, please see upgrading instructions for more information.
Deprecation of APIAccess resource (API Management)
As part of our efforts to simplify and enhance the API management experience, we are deprecating the APIAccess CRD. The functionalities provided by APIAccess are now encompassed by the new ManagedSubscription & APICatalogItem CRDs, offering more visibilty, flexibility and control over API access management.
We recommend transitioning from APIAccess to ManagedSubscription & APICatalogItem to take advantage of the new features and improvements.
Bug Fixes
- We fixed the CVE-2024-52003 vulnerability in Traefik Hub v3.8.0.
- We fixed the CVE-2024-45410 vulnerability in Traefik Hub v3.8.1.
November 2024
What's New
Support for Managing APIs with HTTPRoute in API Management
Traefik Hub API Management now supports using HTTPRoute to manage APIs.
For more information, check out our Kubernetes Gateway API glossary page & API resource documentation.
October 2024
What's New
Support for Consul Catalog Enterprise
We are excited to announce that Traefik Hub API Gateway now supports Consul Catalog Enterprise as a part of our providers.
To get started, check out our Consul Catalog Enterprise documentation to learn how to enable & configure it.
September 2024
What's New
New Feature: Traffic Debugger
We are excited to announce that Traefik Hub now integrates with Treblle as the Traffic Debugger, enhancing your API observability experience across both API Management and Gateway features.
What Does This Mean For You?
- Real-Time API Monitoring: Gain immediate insights into your API traffic, helping you identify and address issues as they happen.
- Request and Response Debugging: The Traffic Debugger provides detailed insights into individual API calls, allowing you to troubleshoot and resolve problems efficiently.
- Error Tracking and Performance Metrics: Monitor error rates, response times, and other critical metrics to optimize your APIs.
Why Is This Important?
With the Treblle integration, you can improve the reliability and performance of your APIs, leading to better user experiences and increased confidence in your API infrastructure.
To get started, check out our Treblle integration guide to learn how to enable this feature and start enhancing your API observability.
New Feature: API Plans (API Management)
Introducing API Plans, a comprehensive solution for API governance that centralizes the management of rate limits and quotas. API Plans replace the previous APIRateLimit feature, providing a more structured and policy-driven approach to controlling API consumption. This ensures fair and efficient resource distribution among your API consumers.
Key Features
- Centralized Policy Management: Consolidate rate limiting and quota enforcement into a single resource, making it easier to maintain and update policies.
- Streamlined Access Control: Simplify the association between user groups and APIs through well-defined plans, enhancing access management efficiency.
- Consistent Governance: Apply standardized API Plans across all APIs to ensure uniform governance and reduce the risk of misconfigurations.
Breaking Change
With the introduction of API Plans, the older APIRateLimit feature is removed. Users are encouraged to transition to API Plans to take advantage of the enhanced governance and management capabilities.
Prerequisites
For creating Plans other than unlimited, ensure that Redis is deployed and configured in your cluster and Traefik deployment to utilize the APIPlan feature. For detailed installation and configuration steps, follow the API Plan documentation.
New Feature: API Bundle (API Management)
We are thrilled to introduce API Bundles, a new feature designed to streamline the management of your APIs. API Bundles allow you to group multiple APIs into a single, cohesive entity, enhancing efficiency and governance.
Key Benefits
- Unified Management: Group one or more APIs under a single API Bundle, simplifying reference and access across your infrastructure.
- Centralized Policy Enforcement: Apply API Plans directly to API Bundles, enabling consistent rate limits and quotas across all included APIs.
- Flexible Inclusion Methods: Add APIs to a bundle by explicitly naming them or using Kubernetes-native label selectors for dynamic and scalable management.
To get started with creating API Bundles, refer to our API Bundle Documentation.
July 2024
What's New
- Native Coraza WAF integration: Secure APIs with the Coraza Web Application Firewall (endorsed by OWASP). The native WAF integration in Traefik Hub provides more than 23x performance improvement over Traefik Proxy's WASM-based WAF plugin.
- Distributed ACME on all platforms using Vault: Simplify certificate management and ensure that certificates are always up-to-date by automatically obtaining and renewing TLS certificates with ACME from Certificate Authorities like Let's Encrypt. The Hub-exclusive distributed ACME is more efficient for large-scale or high-availability setups, as it reduces duplication and ensures consistency across all Gateway instances by leveraging HashiCorp Vault as shared secure certificate storage. Now available for all supported installation platforms.
- Vault Public Key Infrastructure: Create your own private certificate authority (CA) with the HashiCorp Vault PKI secret engine to issue, manage, and revoke digital certificates. Combine it with the gateway's ACME resolvers for automated certificate management, even in a distributed way.
- LDAP middleware: Secure your APIs by delegating the authentication to an external LDAP server with the LDAP middleware.
- OPA middleware: The Open Policy Agent middleware restricts access to your APIs and allows you to enrich request headers with data extracted from policies.
- Cache middleware: Add cache middleware to your routers and improve the performance of your infrastructure by reducing latency, network traffic, and the time needed to interact with an API.
- FIPS-compliant Docker image: Traefik Hub is now compliant with FIPS 140-2, a U.S. Federal Government security standard used to approve cryptographic modules.
- Multi-platform install snippets: A newly added platform selector helps you in the new gateway creation wizard to get tailored installation snippets for Kubernetes, Docker Compose, Docker Swarm, HashiCorp Nomad, and Systemd for Linux-based virtual machines, bare-metal hardware or cloud computing instances like AWS EC2.
- The embedded Traefik Proxy version has been updated to bring the latest open-source improvements for Hub.
API Management-Exclusive Features
- Add any third-party Identity Provider with OIDC: User management has never been easier. Secure your API Developer Portals and API Gateways with any third-party Identity Provider you already have, such as Okta or Azure Entra ID, using enterprise-grade OIDC. Check the documentation about how to configure it on the online Hub dashboard.
- Metrics overview in the online dashboard: The Hub online dashboard gives you an overview of your APIs' overall consumption and health. You can also filter for every API, user, and API Management-enabled gateway. Fine-grained metrics are still available on the gateway with OpenTelemetry.
May 2024
What's New
- Traefik Hub now embeds all Traefik Proxy v3.0 features (compatible with Traefik v2).
- Capacity to install Traefik Hub as a drop-in replacement of Traefik Proxy, with additional Enterprise features such as authentication, authorization, distributed rate limit, and more.
- Traefik Hub provides robust API management capabilities for API publishers and consumers. The features include API versioning, user and fine-grained access management, rate limiting, declarative configuration linting, API developer portals, API observability metrics, and many more.
- Promote any Ingress or IngressRoute to become a managed API. This means one can now attach any built-in gateway middleware or plugins to APIs, unlocking Traefik's entire network power for APIs.
- Extend Traefik Hub with your custom WebAssembly (WASM) plugins.
- Leverage the new Coraza Web Application Firewall, a plugin Traefik Labs supports.
- OpenTelemetry (OTel) metrics are now available on both ingresses and managed APIs.
- Operate API Gateways fully offline without reliance on any SaaS platform.
February 2024
What's New
- We've added a new filtering concept in the APIAccess CRD that enables you to select sets of OpenAPI operations defined on APIs or APIVersions. You can find more information in the API CRD reference.
- All-new API Portal. We've refreshed the API Portal UI to create a better user experience.
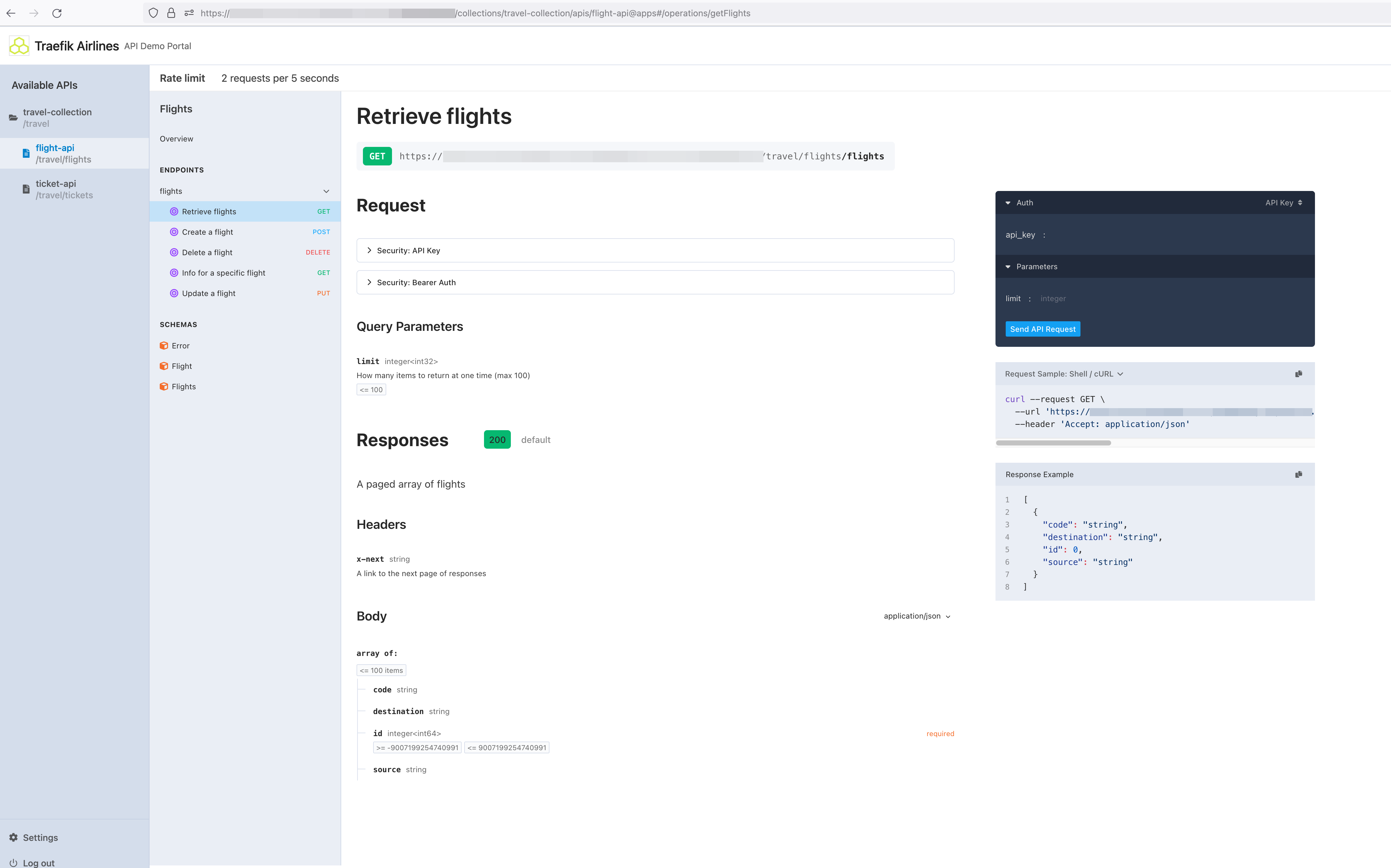
- It is now possible to turn off the generation and usage of traefikhub.io domains for your API Gateways and Portals.
- Error logs generated by the Traefik Hub agent are now transmitted to the Traefik Hub platform and stored for 24 hours to assist in resolving support requests quickly. You can turn off sending error logs by adjusting the default configuration.
- We've enhanced the API and the APIVersion CRDs.
Both CRDs support now naming of the API Service port
service.port.name.
December 2023
What's New
- You can now publish APIs without an OpenAPI specification.
- We've published a complete Traefik Hub GitOps demo.
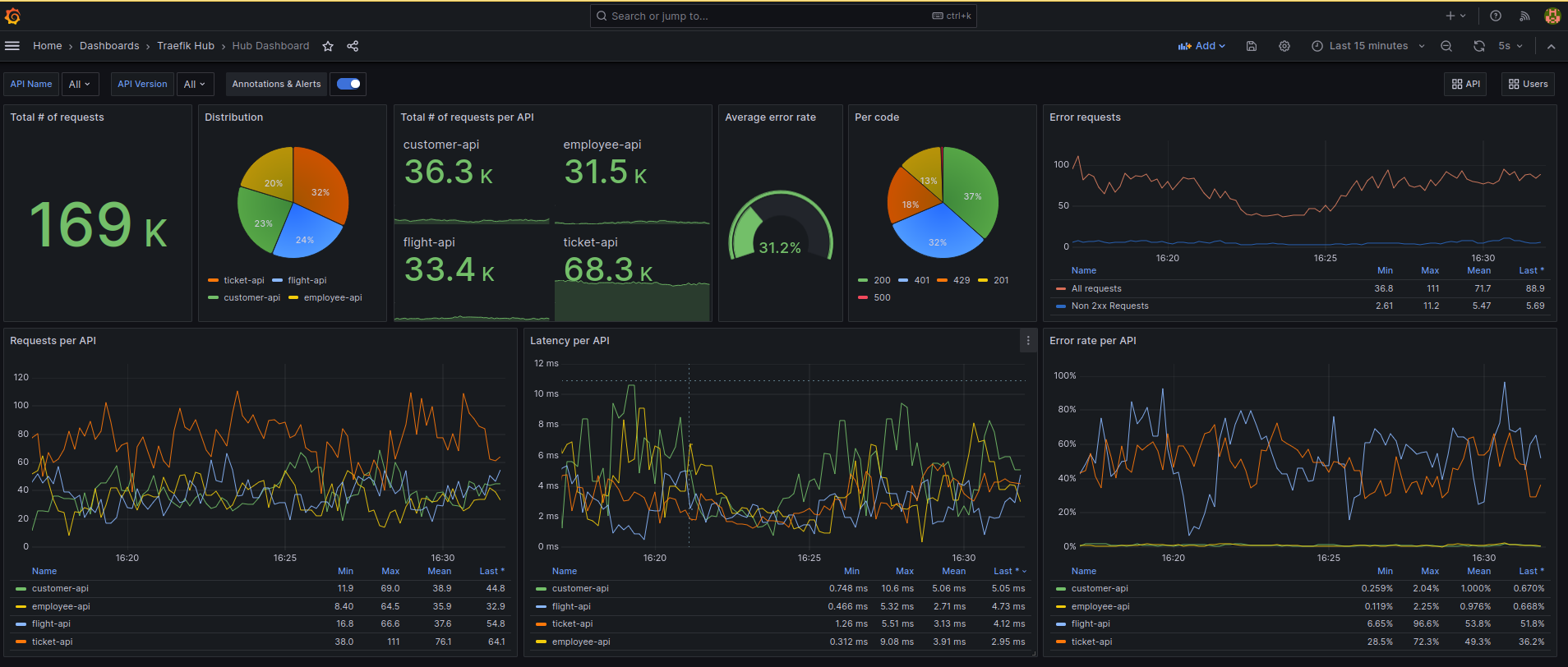
Follow the tutorial to learn how to deploy and manage APIs on a local Kubernetes cluster with Flux.
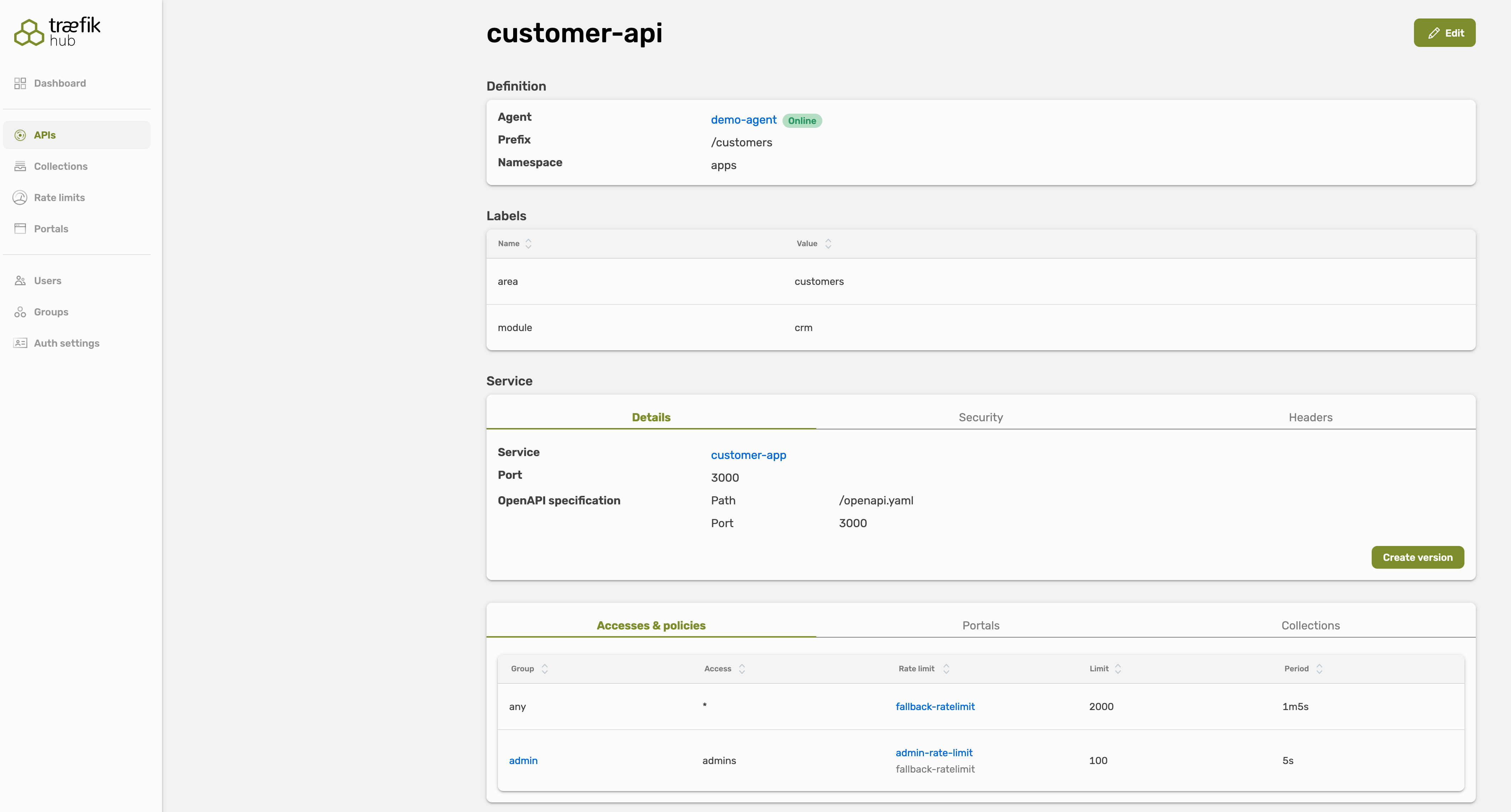
- We've updated the dashboard to make it more effortless for you to get an overview about configured access policies and rate limits.
This information is now displayed in the API details page, as in the user and groups details pages.
November 2023
What's New
- Traefik Hub now has a direct integration with Okta.
- Starting today, you're able to use JWT to secure access to APIs.
- We've added support for distributed rate limiting.
- We've enhanced our OpenTelemetry metrics by adding support for API versions.
- The dashboard now shows a warning sign when a Traefik Hub agent faces a connectivity issue.
- We've released a new version of the Traefik Hub agent
v2.4.2and of the Helm chartv2.5.1v2.5.1 Changelog. Please upgrade the Traefik Hub agent to enjoy the latest enhancements. Depending on your set-up, please follow the detailed documentation about upgrading the Ingress Controller or the Sidecar Mode installation.
October 2023
What's New
- In this release, we've added OpenTelemetry support to Traefik Hub.
- We've added support for adjusting CORS and API header policies through CRDs and via the dashboard.
- You can now manage workspace roles through the dashboard.
Security
- ⚠️ The Traefik Hub agent
v2.3.0and Helm chartv.2.3.0(v2.3.0 Changelog) releases are fixing CVE-2023-44487 in the Traefik Hub agent.
September 2023
What's New
- You can use Keycloak for Single Sign-On (SSO) or as an identity broker for Traefik Hub.
- We enhanced workspace management. You can now assign roles to workspace members.
Every role,
Viewer,EditorandAdminhas a different set of permissions. - Traefik Hub now supports CORS (Cross-Origin Resource Sharing) configuration via CRDs.
August 2023
What's New
- We've added support for API versioning through CRDs and via the dashboard.
- We've published the Traefik Hub Helm Chart on GitHub.
- We've improved the dashboard to provide a better experience when you select Services. You can now better identify if you use an internal or external (API) Service.
- The dashboard shows now a warning sign when the user's initial password reset has not been performed yet.
- We've released a new version of the Traefik Hub Helm chart with an update of the Traefik Hub agent. Please find the changelog for
v2.2.0on GitHub. Please upgrade to versionv2.2.0to enjoy the latest enhancements. Depending on your set-up, please follow the detailed documentation about upgrading the Ingress Controller or the Sidecar Mode installation.
Bug Fixes
- We've fixed a couple of tiny bugs in the user interface (dashboard).
July 2023
What's New
- The Traefik Hub agent supports now two different installation methods, the Ingress Controller mode and the Sidecar Mode.
- We've added Emissary (formerly Ambassador, an Envoy-based) Ingress support with Sidecar Mode.
- We've improved API management, you can now select APIs by name and by Labels. You can combine names and Labels to filter your selections even more.
- We've added support for rate limiting to the dashboard.
- We've added support for Swagger v2.
Bug Fixes
- We've fixed a couple of descriptions in the dashboard.
June 2023
What's New
- You can now manage external APIs, hosted outside your Kubernetes cluster, for example on Virtual Machines (VMs) or third party APIs.
- Starting today, you're able to use rate limiting for APIs.
- We strengthened security. The Traefik Hub token is now provided as a Secret during installation.
- If you deal with large clusters, we made your life easier with filtering Services by namespace in the dashboard, to quickly find what you look for.
- The dashboard provide more guidance, with clear indications of which fields are required and more descriptions.
- We've updated the dashboard to put key information right at your fingertips: information on APIs and API Collections, the API Developer Portal and Users.
Corresponding screens have been updated for better clarity. - We’ve improved the API Developer Portal responsiveness by adding HTTP cache control headers.
- For you to more quickly see how to perform given tasks, we've restructured the documentation, added more tutorials and improved the content overall.
- Based on your feedback, we've tinkered with the internal workings and polished some rough edges.
Bug Fixes
- If your session has expired, you will now be redirected to the login screen.
- We've fixed a couple of bugs in the dashboard related to pop-ups, selecting Services, user groups and error pages.
- We've fixed a bug related to TLS termination.
- There were a few little bugs that caused performances issues, like bugs do. We fixed those, and we’ll fix the next ones too.
May 2023
What's New
- We've changed the architecture, Hub now supports only K8s, the Agent uses a sidecar, and it is compatible with any Ingress Controller.
- We've added a new ACP (Access Control Policy) for API Keys.
- We've added a new OAuth Introspection ACP.
- Starting today, you're able to use CRDs for APIs, API Collections, API Accesses, API Gateways, and API Portal objects.
- API consumption is now protected by tokens.
- We've added API Management, now you can use Hub as a platform for managing, routing, monitoring, and securing APIs.
- You can use Traefik Hub as IdP (Identity Provider).
- We've replaced freemium tiers with a new trial mechanism.
- User deletion is now fully GDPR-compliant, no user data is retained.
- Traefik Hub supports now team collaboration with workspaces.
- Traefik Hub is now compatible with Traefik's IngressRoute.
- We've added support for wildcard domains.
- We've added the functionality to expose Prometheus compatible metrics from the Traefik Hub agent.
- Hub errors are now leveraging K8s events.
- We restructured and updated the documentation.
- We adjusted the Service page in the dashboard, port numbers are now visible when they exceed more than 3 characters.
Bug Fixes
- We fixed an issue that prevented some ACPs to be deleted.
- We improved the process of certificate renewals.
- We solved an issue with custom domain validation.
